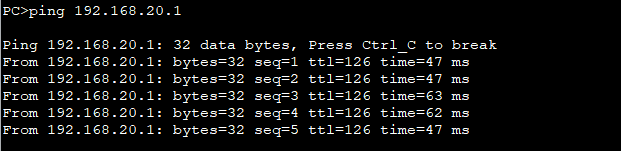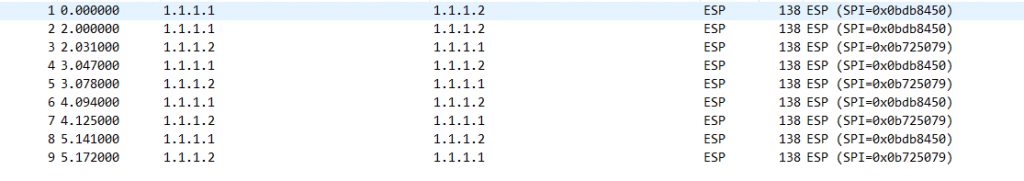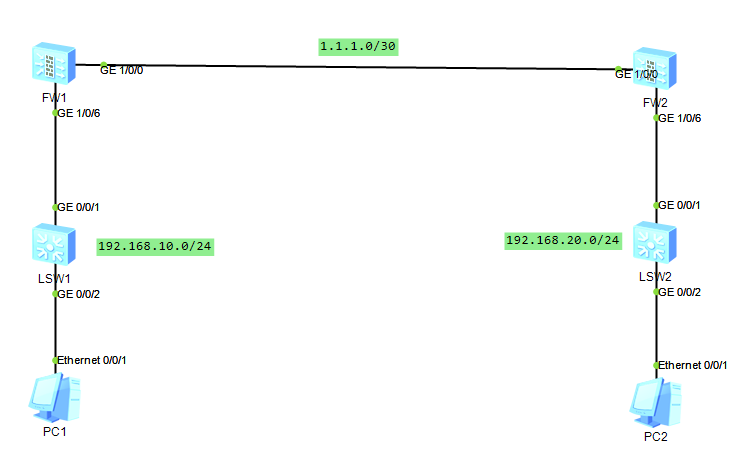
场景:FW1与FW2之间建立Ipsec vpn隧道,使192.168.10.0访问192.168.20.0通过Ipsec VPN进行加密传输来保证数据的安全性。
FW1的配置(FW2类似):
# sysname FW-1 # acl number 3000 //配置Ipsec安全策略中调用的ACL rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 # //配置Ipsec的安全提议 ipsec proposal Ipsec_Proposal esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 1 //配置IKE的安全提议 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer 1.1.1.2 //配置IKE的Peer pre-shared-key %^%#,`bsLMR2(6;%@G0"Xc0:S,fE#}<9pVejWD%m%vg.%^%# ike-proposal 1 remote-address 1.1.1.2 # ipsec policy Ipsec_Policy 1 isakmp //配置Ipsec策略 security acl 3000 ike-peer 1.1.1.2 proposal Ipsec_Proposal # interface GigabitEthernet1/0/0 undo shutdown ip address 1.1.1.1 255.255.255.252 service-manage ping permit ipsec policy Ipsec_Policy //在出接口调用Ipsec策略 # interface GigabitEthernet1/0/6 undo shutdown ip address 192.168.10.254 255.255.255.0 service-manage ping permit # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/6 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0 # ip route-static 192.168.20.0 255.255.255.0 1.1.1.2 //配置访问对端的路由 # security-policy rule name Trust_Untrust_IPSEC //这里配置客户端访问对端客户端出方向策略 source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 destination-address 192.168.20.0 mask 255.255.255.0 action permit rule name Local_Untrust_Ipsec //这里配置防火墙之间建立Ipsec vpn的出方向策略 source-zone local destination-zone untrust source-address 1.1.1.1 mask 255.255.255.255 destination-address 1.1.1.2 mask 255.255.255.255 action permit rule name Untrust_Local_Ipsec //这里配置防火墙之间建立Ipsec vpn的入方向策略 source-zone untrust destination-zone local source-address 1.1.1.2 mask 255.255.255.255 destination-address 1.1.1.1 mask 255.255.255.255 action permit rule name Untrust_Trust_Ipsec //这里配置客户端访问对端客户端入方向策略 source-zone untrust destination-zone trust source-address 192.168.20.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 action permit # return
配置流程:
- 配置相关安全策略
- 配置访问对端网络的路由
- 配置Ipsec策略中需要调用的ACL
- 配置Ipsec安全提议
- 配置IKE安全提议
- 配置IKE Peer
- 配置Ipsec策略
- 在出接口调用Ipsec策略
结果如下: