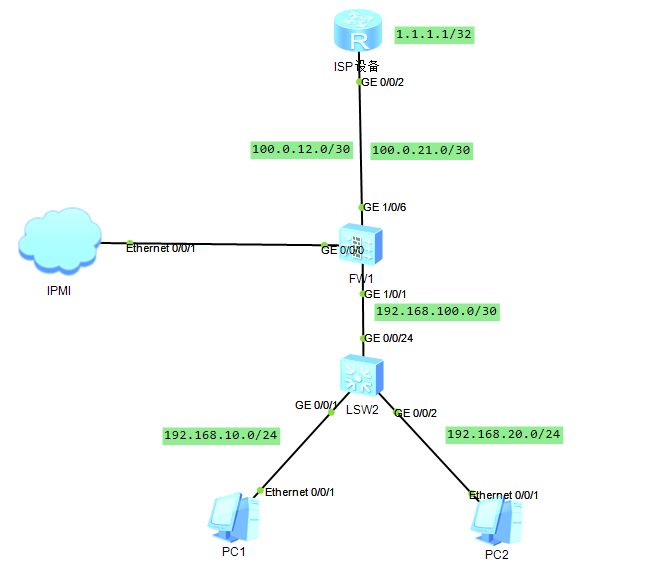
场景说明:在防火墙上做策略路由,让192.168.10.0/24和192.168.20.0/24访问1.1.1.1的时候走100.0.21.0/30这条链路。
防火墙通过子接口方式模拟多条链路接入,交换机作为三层网关,防火墙部署PBR同时使用IP-LINK监控该PBR。
FW配置:
#
sysname FW
#
firewall defend action discard
#
icmp ttl-exceeded send //为了显示tracert的路径,需要开启该命令
# //配置IP-LINK,用于监控策略路由下一跳是否生效,也可以监控路由
ip-link check enable
ip-link name PBR_ISP
destination 100.0.21.2 mode icmp
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.100.1 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/6.1
vlan-type dot1q 10
ip address 100.0.12.1 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/6.2
vlan-type dot1q 11
ip address 100.0.21.1 255.255.255.252
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/6.1
add interface GigabitEthernet1/0/6.2
#
ip route-static 0.0.0.0 0.0.0.0 100.0.12.2
ip route-static 0.0.0.0 0.0.0.0 100.0.21.2
ip route-static 192.168.10.0 255.255.255.0 192.168.100.2
ip route-static 192.168.20.0 255.255.255.0 192.168.100.2
#
security-policy //配置安全策略放行Trust到Untrust
rule name Trust_Untrust_Internet
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
action permit
#
policy-based-route //配置PBR,让两个网段访问的数据定向给100.0.21.2
rule name vlan10_20 1
source-zone trust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
track ip-link PBR_ISP
action pbr next-hop 100.0.21.2
#
nat-policy //配置NAT策略,简略的EasyIP配置
rule name Trust_Untrust_EasyNAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
action source-nat easy-ip
#
return
#
sysname FW
#
firewall defend action discard
#
icmp ttl-exceeded send //为了显示tracert的路径,需要开启该命令
# //配置IP-LINK,用于监控策略路由下一跳是否生效,也可以监控路由
ip-link check enable
ip-link name PBR_ISP
destination 100.0.21.2 mode icmp
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.100.1 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/6.1
vlan-type dot1q 10
ip address 100.0.12.1 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/6.2
vlan-type dot1q 11
ip address 100.0.21.1 255.255.255.252
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/6.1
add interface GigabitEthernet1/0/6.2
#
ip route-static 0.0.0.0 0.0.0.0 100.0.12.2
ip route-static 0.0.0.0 0.0.0.0 100.0.21.2
ip route-static 192.168.10.0 255.255.255.0 192.168.100.2
ip route-static 192.168.20.0 255.255.255.0 192.168.100.2
#
security-policy //配置安全策略放行Trust到Untrust
rule name Trust_Untrust_Internet
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
action permit
#
policy-based-route //配置PBR,让两个网段访问的数据定向给100.0.21.2
rule name vlan10_20 1
source-zone trust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
track ip-link PBR_ISP
action pbr next-hop 100.0.21.2
#
nat-policy //配置NAT策略,简略的EasyIP配置
rule name Trust_Untrust_EasyNAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
action source-nat easy-ip
#
return
# sysname FW # firewall defend action discard # icmp ttl-exceeded send //为了显示tracert的路径,需要开启该命令 # //配置IP-LINK,用于监控策略路由下一跳是否生效,也可以监控路由 ip-link check enable ip-link name PBR_ISP destination 100.0.21.2 mode icmp # interface GigabitEthernet1/0/1 undo shutdown ip address 192.168.100.1 255.255.255.252 service-manage ping permit # interface GigabitEthernet1/0/6.1 vlan-type dot1q 10 ip address 100.0.12.1 255.255.255.252 service-manage ping permit # interface GigabitEthernet1/0/6.2 vlan-type dot1q 11 ip address 100.0.21.1 255.255.255.252 service-manage ping permit # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/1 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/6.1 add interface GigabitEthernet1/0/6.2 # ip route-static 0.0.0.0 0.0.0.0 100.0.12.2 ip route-static 0.0.0.0 0.0.0.0 100.0.21.2 ip route-static 192.168.10.0 255.255.255.0 192.168.100.2 ip route-static 192.168.20.0 255.255.255.0 192.168.100.2 # security-policy //配置安全策略放行Trust到Untrust rule name Trust_Untrust_Internet source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 source-address 192.168.20.0 mask 255.255.255.0 action permit # policy-based-route //配置PBR,让两个网段访问的数据定向给100.0.21.2 rule name vlan10_20 1 source-zone trust source-address 192.168.10.0 mask 255.255.255.0 source-address 192.168.20.0 mask 255.255.255.0 track ip-link PBR_ISP action pbr next-hop 100.0.21.2 # nat-policy //配置NAT策略,简略的EasyIP配置 rule name Trust_Untrust_EasyNAT source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 source-address 192.168.20.0 mask 255.255.255.0 action source-nat easy-ip # return
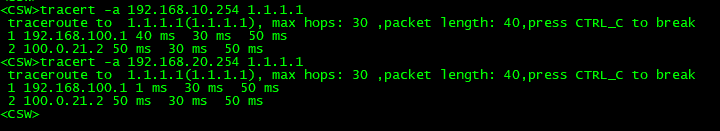
实验结果:由于PC的tracer有问题不能显示中间设备的地址,因此在交换机上通过tracert -a 指定网关地址tracert 1.1.1.1结果如下:
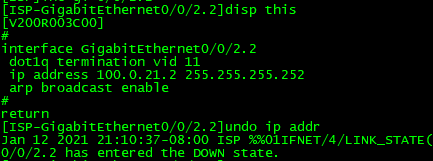
都是通过100.0.21.2访问到1.1.1.1的,说明PBR已生效,下面模拟故障,删除掉ISP上的100.0.21.2地址,看IP-LINK监控是否生效,同时PC长PING 1.1.1.1.
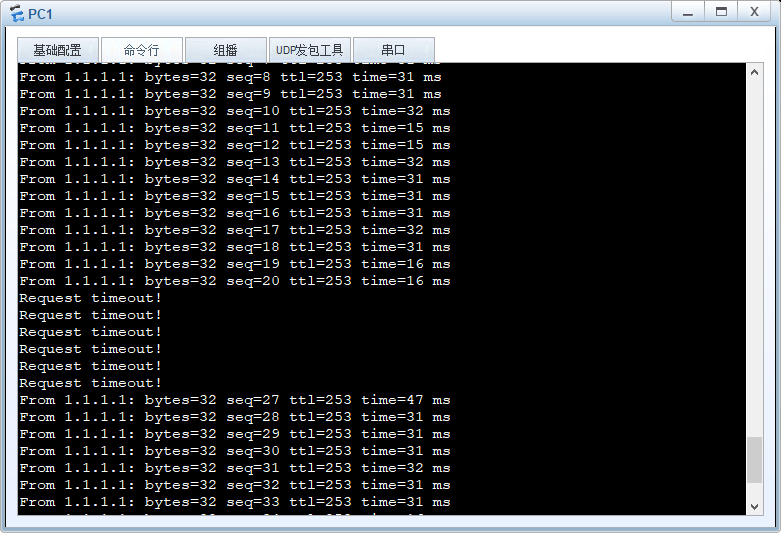
实验结果:IP-LINK检测到PBR失效后,开始进行正常路由选路。