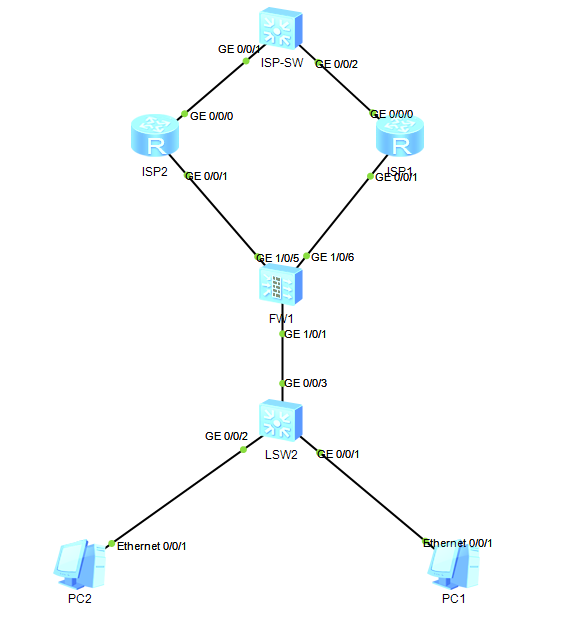
场景说明:防火墙作为出口设备,连接两个ISP,当访问ISP-SW的地址1.1.1.1时,PC1走ISP1、PC2走ISP2,并且防火墙使用track两个运营商。
FW1配置如下:
sysname FW # ip-link check enable //配置IP-link监控每条运营商链路 ip-link name ISP1 source-ip 100.0.100.2 destination 100.0.100.1 interface GigabitEthernet1/0/6 mode icmp tx-interval 3 ip-link name ISP2 source-ip 200.0.200.2 destination 200.0.200.1 interface GigabitEthernet1/0/5 mode icmp tx-interval 3 # interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.0.1 255.255.255.0 alias GE0/METH # interface GigabitEthernet1/0/1 undo shutdown ip address 192.168.10.254 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/5 undo shutdown ip address 200.0.200.2 255.255.255.252 service-manage ping permit # interface GigabitEthernet1/0/6 undo shutdown ip address 100.0.100.2 255.255.255.252 service-manage ping permit # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/1 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/5 add interface GigabitEthernet1/0/6 # # ip route-static 0.0.0.0 0.0.0.0 100.0.100.1 track ip-link ISP1 ip route-static 0.0.0.0 0.0.0.0 200.0.200.1 track ip-link ISP2 # security-policy //配置安全策略允许PC访问公网 rule name Trust_Untrust source-zone trust destination-zone untrust action permit # # policy-based-route //配置PBR,让PC1走ISP1、PC2走ISP2 rule name PC1_ISP1 1 source-zone trust source-address 192.168.10.1 mask 255.255.255.255 action pbr egress-interface GigabitEthernet1/0/6 next-hop 100.0.100.1 rule name PC2_ISP2 2 source-zone trust source-address 192.168.10.2 mask 255.255.255.255 action pbr egress-interface GigabitEthernet1/0/5 next-hop 200.0.200.1 # nat-policy //配置SNAT让PC1、PC2访问公网 rule name Trust—trust_EasyIP source-zone trust destination-zone untrust action source-nat easy-ip # return
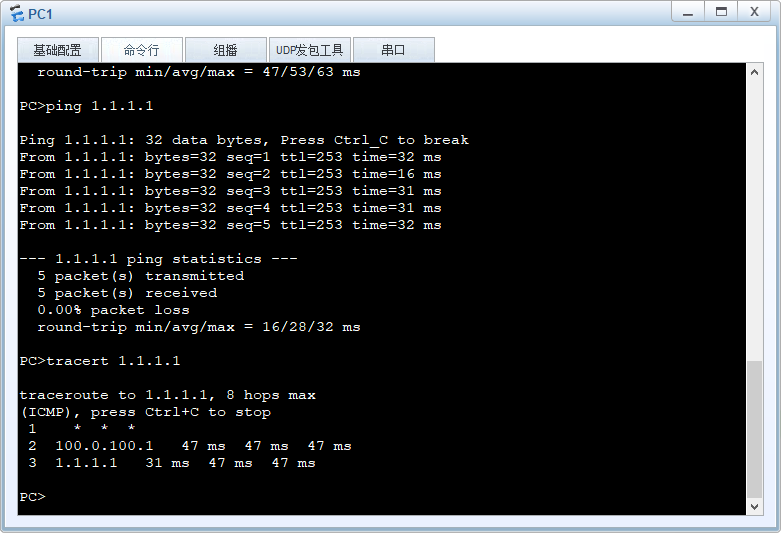
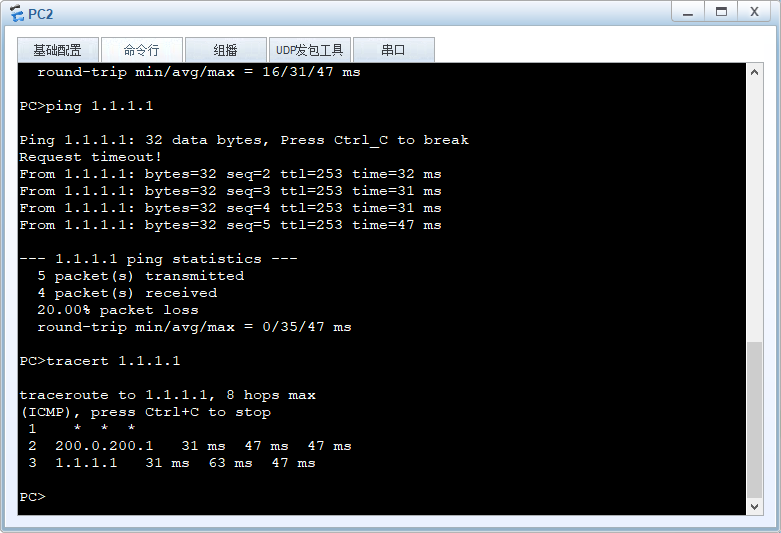
实验结果: