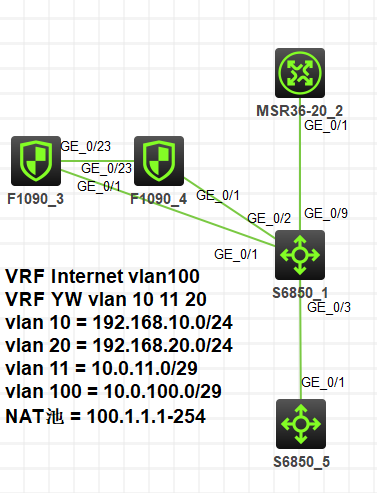
场景说明:防火墙旁挂核心交换机,核心交换机通过vrf区分公网和内网业务,只允许192.168.10.0/24访问公网。通过下联交换机模拟客户端。防火墙采用主备模式,由于复用链路,采用三层子接口终结vlan的方式进行部署,其中vlan11表示内网 vlan100表示公网,全网采用静态路由部署。
防火墙配置:
#
version 7.1.064, Alpha 7164
#
sysname FW-A
#
track 1 interface GigabitEthernet1/0/1
#
nat address-group 0 name SNAT
address 100.1.1.1 100.1.1.254
#
interface GigabitEthernet1/0/1.11 //由于主备组网,需要指定主防火墙vrrp组为active
ip address 10.0.11.2 255.255.255.248
vrrp vrid 11 virtual-ip 10.0.11.1 active
vlan-type dot1q vid 11
#
interface GigabitEthernet1/0/1.100 //由于主备组网,需要指定主防火墙vrrp组为active
ip address 10.0.100.2 255.255.255.248
vrrp vrid 100 virtual-ip 10.0.100.1 active
vlan-type dot1q vid 100
#
interface GigabitEthernet1/0/23
port link-mode route
combo enable copper
ip address 1.1.1.1 255.255.255.252
#
security-zone name Trust
import interface GigabitEthernet1/0/1.11
#
security-zone name DMZ
import interface GigabitEthernet1/0/23
#
security-zone name Untrust
import interface GigabitEthernet1/0/1.100
#
ip route-static 0.0.0.0 0 10.0.100.4
ip route-static 192.168.0.0 16 10.0.11.4
#
nat global-policy
rule name Trust_Untrust_SNAT
source-zone Trust
destination-zone Untrust
source-ip subnet 192.168.10.0 24
action snat address-group name SNAT
#
ip http enable
ip https enable
#
security-policy ip
rule 0 name Trust_Untrust_Permit
action pass
source-zone Trust
destination-zone Untrust
source-ip-subnet 192.168.10.0 255.255.255.0
#
remote-backup group
data-channel interface GigabitEthernet1/0/23
delay-time 1
track 1
local-ip 1.1.1.1
remote-ip 1.1.1.2
device-role primary
#
return
#
version 7.1.064, Alpha 7164
#
sysname FW-A
#
track 1 interface GigabitEthernet1/0/1
#
nat address-group 0 name SNAT
address 100.1.1.1 100.1.1.254
#
interface GigabitEthernet1/0/1.11 //由于主备组网,需要指定主防火墙vrrp组为active
ip address 10.0.11.2 255.255.255.248
vrrp vrid 11 virtual-ip 10.0.11.1 active
vlan-type dot1q vid 11
#
interface GigabitEthernet1/0/1.100 //由于主备组网,需要指定主防火墙vrrp组为active
ip address 10.0.100.2 255.255.255.248
vrrp vrid 100 virtual-ip 10.0.100.1 active
vlan-type dot1q vid 100
#
interface GigabitEthernet1/0/23
port link-mode route
combo enable copper
ip address 1.1.1.1 255.255.255.252
#
security-zone name Trust
import interface GigabitEthernet1/0/1.11
#
security-zone name DMZ
import interface GigabitEthernet1/0/23
#
security-zone name Untrust
import interface GigabitEthernet1/0/1.100
#
ip route-static 0.0.0.0 0 10.0.100.4
ip route-static 192.168.0.0 16 10.0.11.4
#
nat global-policy
rule name Trust_Untrust_SNAT
source-zone Trust
destination-zone Untrust
source-ip subnet 192.168.10.0 24
action snat address-group name SNAT
#
ip http enable
ip https enable
#
security-policy ip
rule 0 name Trust_Untrust_Permit
action pass
source-zone Trust
destination-zone Untrust
source-ip-subnet 192.168.10.0 255.255.255.0
#
remote-backup group
data-channel interface GigabitEthernet1/0/23
delay-time 1
track 1
local-ip 1.1.1.1
remote-ip 1.1.1.2
device-role primary
#
return
# version 7.1.064, Alpha 7164 # sysname FW-A # track 1 interface GigabitEthernet1/0/1 # nat address-group 0 name SNAT address 100.1.1.1 100.1.1.254 # interface GigabitEthernet1/0/1.11 //由于主备组网,需要指定主防火墙vrrp组为active ip address 10.0.11.2 255.255.255.248 vrrp vrid 11 virtual-ip 10.0.11.1 active vlan-type dot1q vid 11 # interface GigabitEthernet1/0/1.100 //由于主备组网,需要指定主防火墙vrrp组为active ip address 10.0.100.2 255.255.255.248 vrrp vrid 100 virtual-ip 10.0.100.1 active vlan-type dot1q vid 100 # interface GigabitEthernet1/0/23 port link-mode route combo enable copper ip address 1.1.1.1 255.255.255.252 # security-zone name Trust import interface GigabitEthernet1/0/1.11 # security-zone name DMZ import interface GigabitEthernet1/0/23 # security-zone name Untrust import interface GigabitEthernet1/0/1.100 # ip route-static 0.0.0.0 0 10.0.100.4 ip route-static 192.168.0.0 16 10.0.11.4 # nat global-policy rule name Trust_Untrust_SNAT source-zone Trust destination-zone Untrust source-ip subnet 192.168.10.0 24 action snat address-group name SNAT # ip http enable ip https enable # security-policy ip rule 0 name Trust_Untrust_Permit action pass source-zone Trust destination-zone Untrust source-ip-subnet 192.168.10.0 255.255.255.0 # remote-backup group data-channel interface GigabitEthernet1/0/23 delay-time 1 track 1 local-ip 1.1.1.1 remote-ip 1.1.1.2 device-role primary # return
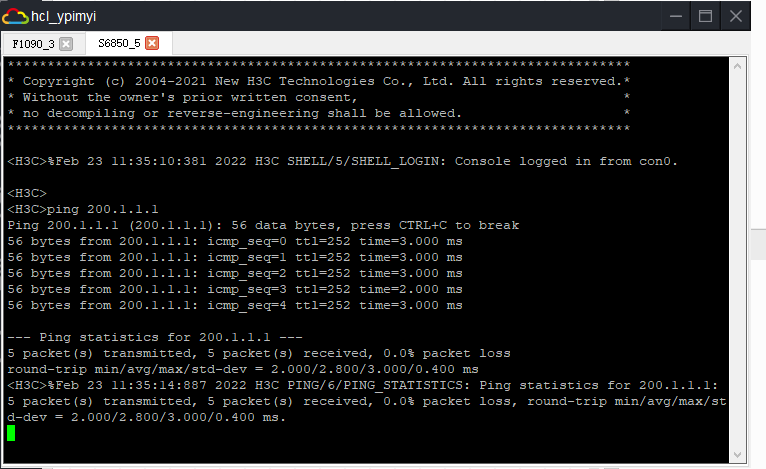
实验结果:通过交换机模拟终端访问路由上公网地址200.1.1.1