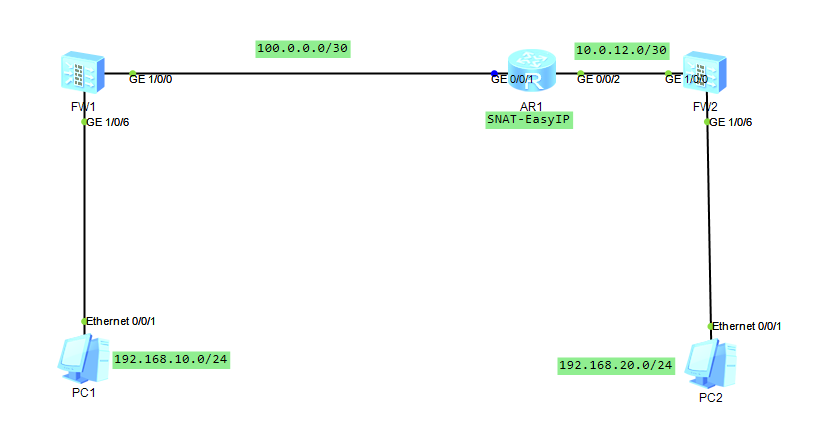
场景说明:FW1作为出口设备连接公网,FW2作为内网防火墙,连接自己放的出口路由器,出口路由器上做SNAT,现在需要两台防火墙之间建立IPSEC VPN隧道保护PC1与PC2之间通讯。
FW1配置:
#
sysname FW1
#
acl number 3000 //配置IPSEC VPN感兴趣流
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec proposal 1 //配置IPSEC安全提议,默认采用隧道模式
esp authentication-algorithm sha2-256 //配置IPSEC的认证算法
esp encryption-algorithm aes-256 //配置IPSEC的加密算法
#
ike proposal 1 //配置IKE安全提议
encryption-algorithm aes-256 //配置加密算法
dh group14 //配置DH公共值的组
authentication-algorithm sha2-256 //配置认证算法
authentication-method pre-share //配置认证方式为预共享密钥
integrity-algorithm hmac-sha2-256 //配置IKEv2版本下的完整性验证算法
prf hmac-sha2-256 //配置IKEv2中使用的伪随机数算法
#
ike peer 1 //配置IKE PEER
pre-shared-key %^%#ybh~2$'Xc/KwoR1:_.MD;TTg&p_2:WaWe30&tHf/%^%#
ike-proposal 1
dpd type on-demand //配置DPD保活检测,周期性发送DPD报文保活IPSEC隧道和检测IPSEC隧道的故障
remote-address 100.0.0.2 //由于是NAT-T场景,对端路由器做了SNAT,因此需要写地址为SNAT后的地址
remote-address authentication-address 10.0.12.1 //由于NAT-T场景,需要验证对等体SNAT之前的地址
#
ipsec policy 1 1 isakmp //配置IPSEC POLICY,采用IKE方式协商IPSEC SA
security acl 3000
ike-peer 1
proposal 1
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.252
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.10.254 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 100.0.0.2
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust&Local_IKE_Permit
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_IPSEC_Permit
source-zone untrust
destination-zone local
source-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
service esp
action permit
#
nat-policy
rule name Trust_Untrust_NO-PAT //配置NO-NAT,让PC1访问PC2不进行NAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action no-nat
rule name Trust_Untrust_SNAT //为了使PC1访问互联网,需要配置SNAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action source-nat easy-ip
#
return
#
sysname FW1
#
acl number 3000 //配置IPSEC VPN感兴趣流
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec proposal 1 //配置IPSEC安全提议,默认采用隧道模式
esp authentication-algorithm sha2-256 //配置IPSEC的认证算法
esp encryption-algorithm aes-256 //配置IPSEC的加密算法
#
ike proposal 1 //配置IKE安全提议
encryption-algorithm aes-256 //配置加密算法
dh group14 //配置DH公共值的组
authentication-algorithm sha2-256 //配置认证算法
authentication-method pre-share //配置认证方式为预共享密钥
integrity-algorithm hmac-sha2-256 //配置IKEv2版本下的完整性验证算法
prf hmac-sha2-256 //配置IKEv2中使用的伪随机数算法
#
ike peer 1 //配置IKE PEER
pre-shared-key %^%#ybh~2$'Xc/KwoR1:_.MD;TTg&p_2:WaWe30&tHf/%^%#
ike-proposal 1
dpd type on-demand //配置DPD保活检测,周期性发送DPD报文保活IPSEC隧道和检测IPSEC隧道的故障
remote-address 100.0.0.2 //由于是NAT-T场景,对端路由器做了SNAT,因此需要写地址为SNAT后的地址
remote-address authentication-address 10.0.12.1 //由于NAT-T场景,需要验证对等体SNAT之前的地址
#
ipsec policy 1 1 isakmp //配置IPSEC POLICY,采用IKE方式协商IPSEC SA
security acl 3000
ike-peer 1
proposal 1
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.252
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.10.254 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 100.0.0.2
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust&Local_IKE_Permit
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_IPSEC_Permit
source-zone untrust
destination-zone local
source-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
service esp
action permit
#
nat-policy
rule name Trust_Untrust_NO-PAT //配置NO-NAT,让PC1访问PC2不进行NAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action no-nat
rule name Trust_Untrust_SNAT //为了使PC1访问互联网,需要配置SNAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action source-nat easy-ip
#
return
# sysname FW1 # acl number 3000 //配置IPSEC VPN感兴趣流 rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 # ipsec proposal 1 //配置IPSEC安全提议,默认采用隧道模式 esp authentication-algorithm sha2-256 //配置IPSEC的认证算法 esp encryption-algorithm aes-256 //配置IPSEC的加密算法 # ike proposal 1 //配置IKE安全提议 encryption-algorithm aes-256 //配置加密算法 dh group14 //配置DH公共值的组 authentication-algorithm sha2-256 //配置认证算法 authentication-method pre-share //配置认证方式为预共享密钥 integrity-algorithm hmac-sha2-256 //配置IKEv2版本下的完整性验证算法 prf hmac-sha2-256 //配置IKEv2中使用的伪随机数算法 # ike peer 1 //配置IKE PEER pre-shared-key %^%#ybh~2$'Xc/KwoR1:_.MD;TTg&p_2:WaWe30&tHf/%^%# ike-proposal 1 dpd type on-demand //配置DPD保活检测,周期性发送DPD报文保活IPSEC隧道和检测IPSEC隧道的故障 remote-address 100.0.0.2 //由于是NAT-T场景,对端路由器做了SNAT,因此需要写地址为SNAT后的地址 remote-address authentication-address 10.0.12.1 //由于NAT-T场景,需要验证对等体SNAT之前的地址 # ipsec policy 1 1 isakmp //配置IPSEC POLICY,采用IKE方式协商IPSEC SA security acl 3000 ike-peer 1 proposal 1 # interface GigabitEthernet1/0/0 undo shutdown ip address 100.0.0.1 255.255.255.252 # interface GigabitEthernet1/0/6 undo shutdown ip address 192.168.10.254 255.255.255.0 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/6 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0 # firewall zone dmz set priority 50 # ip route-static 0.0.0.0 0.0.0.0 100.0.0.2 # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action permit rule name Untrust&Local_IKE_Permit source-zone local source-zone untrust destination-zone local destination-zone untrust source-address 100.0.0.1 mask 255.255.255.255 source-address 100.0.0.2 mask 255.255.255.255 destination-address 100.0.0.1 mask 255.255.255.255 destination-address 100.0.0.2 mask 255.255.255.255 action permit rule name Untrust_Trust_Permit source-zone untrust destination-zone trust source-address 192.168.20.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 action permit rule name Untrust_Local_IPSEC_Permit source-zone untrust destination-zone local source-address 100.0.0.2 mask 255.255.255.255 destination-address 100.0.0.1 mask 255.255.255.255 service esp action permit # nat-policy rule name Trust_Untrust_NO-PAT //配置NO-NAT,让PC1访问PC2不进行NAT source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 destination-address 192.168.20.0 mask 255.255.255.0 action no-nat rule name Trust_Untrust_SNAT //为了使PC1访问互联网,需要配置SNAT source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action source-nat easy-ip # return
要点:该场景要点,需要由于是NAT-T场景, 由于是路由器进行SNAT,FW2在内网工作,因此第一次流量发起者需要是PC2访问PC1,如果是PC1访问PC2的话是无法建立IKE SA的。 另外配置DPD来保活后续建立的通道,让PC1也可以访问PC2,防止没有流量的时候隧道被拆除。