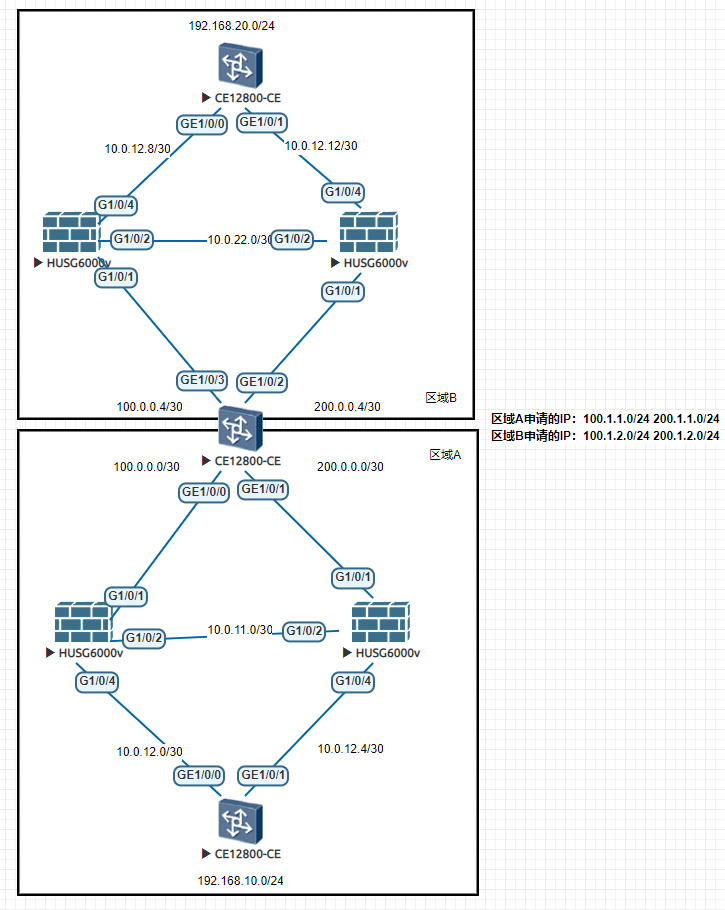
场景说明:A区域和B区域通过防火墙互联, 防火墙单机部署, 中间交换机模拟互联网,两端防火墙通过建立IPSec VPN隧道打通私网互访,并提供加密功能,形成负载场景。防火墙与内部交换机之间运行OSPF。
防火墙配置:
sysname FW-1
#这里配置DPD,用于感知IPSEC VPN故障后,删除IPSEC SA和IKE SA
ike dpd type periodic
ike dpd idle-time 10
ike dpd retransmit-interval 2
ike dpd msg seq-notify-hash
#定义感兴趣流
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#创建IPSEC安全提议
ipsec proposal A
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#创建IKE安全提议
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#创建IKE对等体
ike peer A
pre-shared-key %^%#<Yz_-9h[45BY|K2f]LdRYB}-#L4"I-'|me#AROx&%^%#
ike-proposal 1
remote-address 100.1.2.1
#创建IPSEC策略
ipsec policy A 1 isakmp
security acl 3000
ike-peer A
proposal A
sa trigger-mode auto //配置IPSEC隧道触发方式为自动触发
route inject dynamic //配置根据感兴趣流自动注入unr路由
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.0.11.1 255.255.255.252
ospf network-type p2p
service-manage ping permit
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 10.0.12.1 255.255.255.252
ospf network-type p2p
service-manage ping permit
#
interface Tunnel0
ip address 100.1.1.1 255.255.255.255
tunnel-protocol ipsec
ipsec policy A
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Tunnel0
#
firewall zone dmz
set priority 50
#
ospf 1
default-route-advertise
import-route unr
area 0.0.0.0
network 10.0.11.0 0.0.0.3
network 10.0.12.0 0.0.0.3
network 100.1.1.1 0.0.0.0
#
ip route-static 0.0.0.0 0.0.0.0 100.0.0.1
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
action permit
rule name Untrust&Local_IPSec_Permit
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.0.0.0 mask 255.255.255.252
source-address 100.0.0.4 mask 255.255.255.252
source-address 100.1.1.0 mask 255.255.255.0
source-address 100.1.2.0 mask 255.255.255.0
source-address 200.0.0.0 mask 255.255.255.252
source-address 200.0.0.4 mask 255.255.255.252
source-address 200.1.1.0 mask 255.255.255.0
source-address 200.1.2.0 mask 255.255.255.0
destination-address 100.0.0.0 mask 255.255.255.252
destination-address 100.0.0.4 mask 255.255.255.252
destination-address 100.1.1.0 mask 255.255.255.0
destination-address 100.1.2.0 mask 255.255.255.0
destination-address 200.0.0.0 mask 255.255.255.252
destination-address 200.0.0.4 mask 255.255.255.252
destination-address 200.1.1.0 mask 255.255.255.0
destination-address 200.1.2.0 mask 255.255.255.0
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
sysname FW-1
#这里配置DPD,用于感知IPSEC VPN故障后,删除IPSEC SA和IKE SA
ike dpd type periodic
ike dpd idle-time 10
ike dpd retransmit-interval 2
ike dpd msg seq-notify-hash
#定义感兴趣流
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#创建IPSEC安全提议
ipsec proposal A
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#创建IKE安全提议
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#创建IKE对等体
ike peer A
pre-shared-key %^%#<Yz_-9h[45BY|K2f]LdRYB}-#L4"I-'|me#AROx&%^%#
ike-proposal 1
remote-address 100.1.2.1
#创建IPSEC策略
ipsec policy A 1 isakmp
security acl 3000
ike-peer A
proposal A
sa trigger-mode auto //配置IPSEC隧道触发方式为自动触发
route inject dynamic //配置根据感兴趣流自动注入unr路由
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.0.11.1 255.255.255.252
ospf network-type p2p
service-manage ping permit
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 10.0.12.1 255.255.255.252
ospf network-type p2p
service-manage ping permit
#
interface Tunnel0
ip address 100.1.1.1 255.255.255.255
tunnel-protocol ipsec
ipsec policy A
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Tunnel0
#
firewall zone dmz
set priority 50
#
ospf 1
default-route-advertise
import-route unr
area 0.0.0.0
network 10.0.11.0 0.0.0.3
network 10.0.12.0 0.0.0.3
network 100.1.1.1 0.0.0.0
#
ip route-static 0.0.0.0 0.0.0.0 100.0.0.1
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
action permit
rule name Untrust&Local_IPSec_Permit
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 100.0.0.0 mask 255.255.255.252
source-address 100.0.0.4 mask 255.255.255.252
source-address 100.1.1.0 mask 255.255.255.0
source-address 100.1.2.0 mask 255.255.255.0
source-address 200.0.0.0 mask 255.255.255.252
source-address 200.0.0.4 mask 255.255.255.252
source-address 200.1.1.0 mask 255.255.255.0
source-address 200.1.2.0 mask 255.255.255.0
destination-address 100.0.0.0 mask 255.255.255.252
destination-address 100.0.0.4 mask 255.255.255.252
destination-address 100.1.1.0 mask 255.255.255.0
destination-address 100.1.2.0 mask 255.255.255.0
destination-address 200.0.0.0 mask 255.255.255.252
destination-address 200.0.0.4 mask 255.255.255.252
destination-address 200.1.1.0 mask 255.255.255.0
destination-address 200.1.2.0 mask 255.255.255.0
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
sysname FW-1 #这里配置DPD,用于感知IPSEC VPN故障后,删除IPSEC SA和IKE SA ike dpd type periodic ike dpd idle-time 10 ike dpd retransmit-interval 2 ike dpd msg seq-notify-hash #定义感兴趣流 acl number 3000 rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 #创建IPSEC安全提议 ipsec proposal A esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 #创建IKE安全提议 ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 #创建IKE对等体 ike peer A pre-shared-key %^%#<Yz_-9h[45BY|K2f]LdRYB}-#L4"I-'|me#AROx&%^%# ike-proposal 1 remote-address 100.1.2.1 #创建IPSEC策略 ipsec policy A 1 isakmp security acl 3000 ike-peer A proposal A sa trigger-mode auto //配置IPSEC隧道触发方式为自动触发 route inject dynamic //配置根据感兴趣流自动注入unr路由 # interface GigabitEthernet1/0/0 undo shutdown # interface GigabitEthernet1/0/1 undo shutdown ip address 100.0.0.2 255.255.255.252 service-manage ping permit # interface GigabitEthernet1/0/2 undo shutdown ip address 10.0.11.1 255.255.255.252 ospf network-type p2p service-manage ping permit # interface GigabitEthernet1/0/3 undo shutdown # interface GigabitEthernet1/0/4 undo shutdown ip address 10.0.12.1 255.255.255.252 ospf network-type p2p service-manage ping permit # interface Tunnel0 ip address 100.1.1.1 255.255.255.255 tunnel-protocol ipsec ipsec policy A # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/4 add interface GigabitEthernet1/0/2 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 add interface Tunnel0 # firewall zone dmz set priority 50 # ospf 1 default-route-advertise import-route unr area 0.0.0.0 network 10.0.11.0 0.0.0.3 network 10.0.12.0 0.0.0.3 network 100.1.1.1 0.0.0.0 # ip route-static 0.0.0.0 0.0.0.0 100.0.0.1 # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust action permit rule name Untrust&Local_IPSec_Permit source-zone local source-zone untrust destination-zone local destination-zone untrust source-address 100.0.0.0 mask 255.255.255.252 source-address 100.0.0.4 mask 255.255.255.252 source-address 100.1.1.0 mask 255.255.255.0 source-address 100.1.2.0 mask 255.255.255.0 source-address 200.0.0.0 mask 255.255.255.252 source-address 200.0.0.4 mask 255.255.255.252 source-address 200.1.1.0 mask 255.255.255.0 source-address 200.1.2.0 mask 255.255.255.0 destination-address 100.0.0.0 mask 255.255.255.252 destination-address 100.0.0.4 mask 255.255.255.252 destination-address 100.1.1.0 mask 255.255.255.0 destination-address 100.1.2.0 mask 255.255.255.0 destination-address 200.0.0.0 mask 255.255.255.252 destination-address 200.0.0.4 mask 255.255.255.252 destination-address 200.1.1.0 mask 255.255.255.0 destination-address 200.1.2.0 mask 255.255.255.0 action permit rule name Untrust_Trust_Permit source-zone untrust destination-zone trust source-address 192.168.20.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 action permit # return