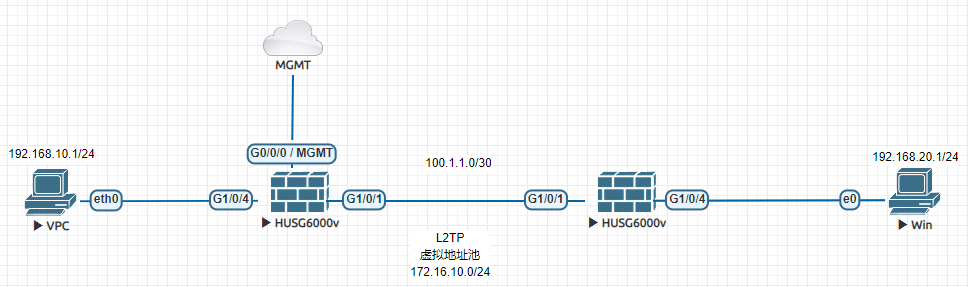
场景说明:Win设备作为终端,与LNS建立L2TP VPN访问VPC,LNS分配地址给终端,Win侧防火墙仅配置SNAT和基础策略, VPC侧防火墙配置L2TP VPN作为LNS对终端进行认证。
LNS配置:
sysname FW-1
#
l2tp enable
l2tp domain suffix-separator @
#
ip pool L2TP_A //创建L2TP VPN使用的地址池
section 0 172.16.10.1 172.16.10.253
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authentication-scheme admin_ldap
authorization-scheme default
accounting-scheme default
service-scheme L2TP //创建L2TP服务方案,绑定相关地址池
ip-pool L2TP_A
domain default
service-type internetaccess ssl-vpn l2tp ike //这里需要给认证域开启l2tp功能
internet-access mode auto-online
reference user current-domain
user-manage group /default/A //创建一个用户组
user-manage user arssra //创建L2TP用户
parent-group /default/A //将用户加入用户组
password arssra //配置用户密码
#
l2tp-group 1 //创建l2tp组
tunnel password cipher %$%$0NR|Ot_>@YQa{.MY2:PT,QSC%$%$ //配置L2TP隧道密码
allow l2tp virtual-template 0 remote A //关联VT接口,以及设置隧道名称
#
interface Virtual-Template0
ppp authentication-mode chap //配置PPP认证方式为CHAP
remote service-scheme L2TP //关联服务方案
ip address 172.16.10.254 255.255.255.0
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.31.201 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.1.1 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.10.254 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Virtual-Template0
#
firewall zone dmz
set priority 50
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_L2TP_Permit
source-zone untrust
destination-zone local
destination-address 100.1.1.1 mask 255.255.255.255
service l2tp
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 172.16.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
sysname FW-1
#
l2tp enable
l2tp domain suffix-separator @
#
ip pool L2TP_A //创建L2TP VPN使用的地址池
section 0 172.16.10.1 172.16.10.253
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authentication-scheme admin_ldap
authorization-scheme default
accounting-scheme default
service-scheme L2TP //创建L2TP服务方案,绑定相关地址池
ip-pool L2TP_A
domain default
service-type internetaccess ssl-vpn l2tp ike //这里需要给认证域开启l2tp功能
internet-access mode auto-online
reference user current-domain
user-manage group /default/A //创建一个用户组
user-manage user arssra //创建L2TP用户
parent-group /default/A //将用户加入用户组
password arssra //配置用户密码
#
l2tp-group 1 //创建l2tp组
tunnel password cipher %$%$0NR|Ot_>@YQa{.MY2:PT,QSC%$%$ //配置L2TP隧道密码
allow l2tp virtual-template 0 remote A //关联VT接口,以及设置隧道名称
#
interface Virtual-Template0
ppp authentication-mode chap //配置PPP认证方式为CHAP
remote service-scheme L2TP //关联服务方案
ip address 172.16.10.254 255.255.255.0
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.31.201 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.1.1 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.10.254 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Virtual-Template0
#
firewall zone dmz
set priority 50
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_L2TP_Permit
source-zone untrust
destination-zone local
destination-address 100.1.1.1 mask 255.255.255.255
service l2tp
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 172.16.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
sysname FW-1
#
l2tp enable
l2tp domain suffix-separator @
#
ip pool L2TP_A //创建L2TP VPN使用的地址池
section 0 172.16.10.1 172.16.10.253
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authentication-scheme admin_ldap
authorization-scheme default
accounting-scheme default
service-scheme L2TP //创建L2TP服务方案,绑定相关地址池
ip-pool L2TP_A
domain default
service-type internetaccess ssl-vpn l2tp ike //这里需要给认证域开启l2tp功能
internet-access mode auto-online
reference user current-domain
user-manage group /default/A //创建一个用户组
user-manage user arssra //创建L2TP用户
parent-group /default/A //将用户加入用户组
password arssra //配置用户密码
#
l2tp-group 1 //创建l2tp组
tunnel password cipher %$%$0NR|Ot_>@YQa{.MY2:PT,QSC%$%$ //配置L2TP隧道密码
allow l2tp virtual-template 0 remote A //关联VT接口,以及设置隧道名称
#
interface Virtual-Template0
ppp authentication-mode chap //配置PPP认证方式为CHAP
remote service-scheme L2TP //关联服务方案
ip address 172.16.10.254 255.255.255.0
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.31.201 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.1.1.1 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.10.254 255.255.255.0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Virtual-Template0
#
firewall zone dmz
set priority 50
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_L2TP_Permit
source-zone untrust
destination-zone local
destination-address 100.1.1.1 mask 255.255.255.255
service l2tp
action permit
rule name Untrust_Trust_Permit
source-zone untrust
destination-zone trust
source-address 172.16.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
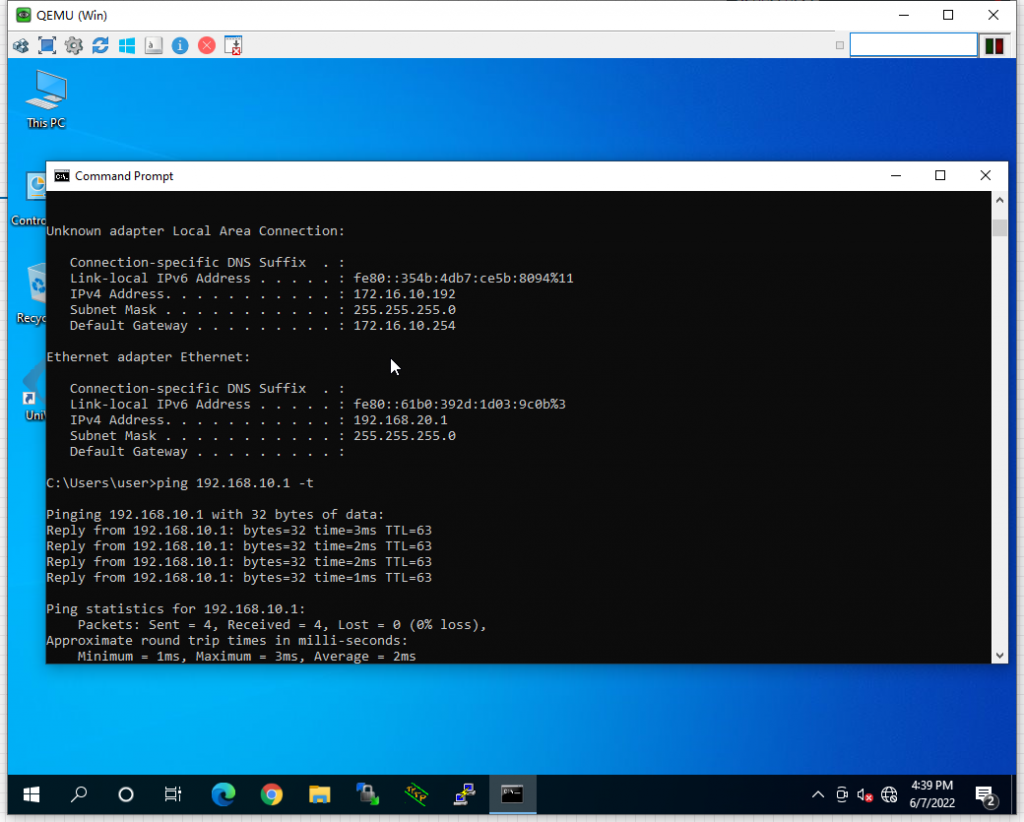
结果:通过VPN客户端可以正常登录到LNS上并访问到VPC