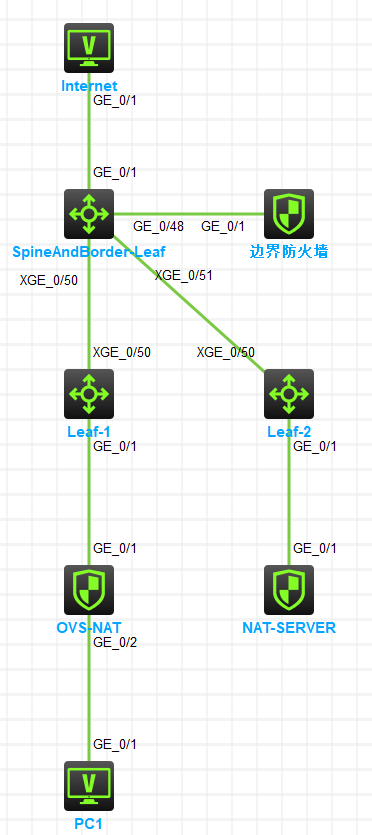
场景说明:使用防火墙模拟OVS设备进行NAT,使用防火墙模拟NAT-SERVER位于DMZ区域,Spine/Border-Leaf融合部署作为集中式网关存在,Border-Leaf旁路部署防火墙,防火墙采用虚拟化vsys部署与Border-Leaf建立OSPF邻居关系。
PC1访问Internet路径为:PC1作为私网首先将流量转发给OVS -> OVS进行NAT将地址转换为vlan301内部地址然后将流量转发至集中式网关Border-Leaf(Inside VRF) -> Border-Leaf将流量转发给虚拟防火墙Inside -> 虚拟防火墙进行安全策略处理完毕后将流量发送回Border-Leaf (DMZ VRF) -> Border-Leaf将流量封装vxlan转发给NAT-SERVER -> NAT-SERVER收到流量后做SNAT处理将地址转为公网地址将流量转发给Border-Leaf (Inside_Internet VRF) -> Border-Leaf将流量转发给根墙进行处理 -> 防火墙根墙经过安全策略处理完毕后将流量转发至Border-Leaf(Internet VRF) -> Border-Leaf将流量转发至Internet。
来回路径一致
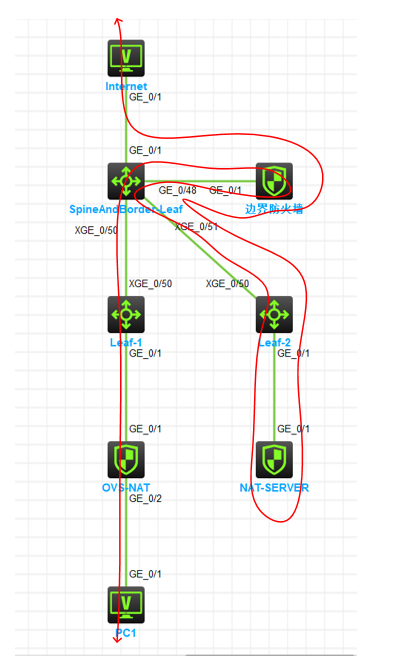
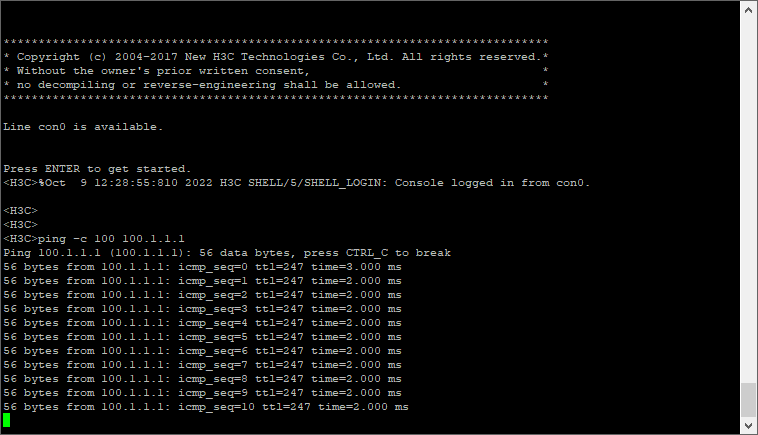
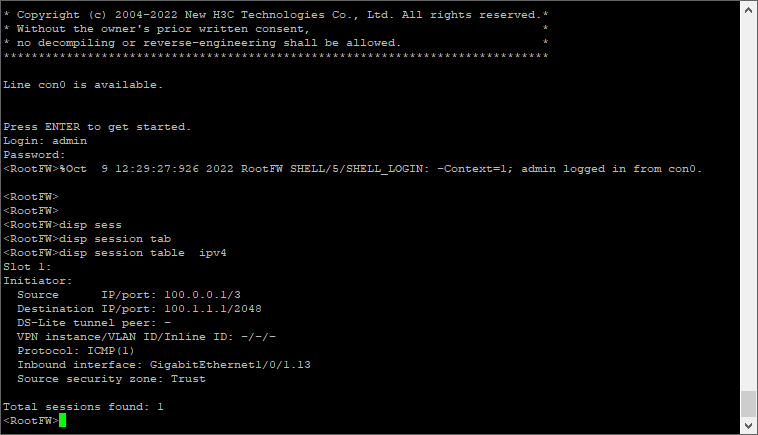
实验结果:
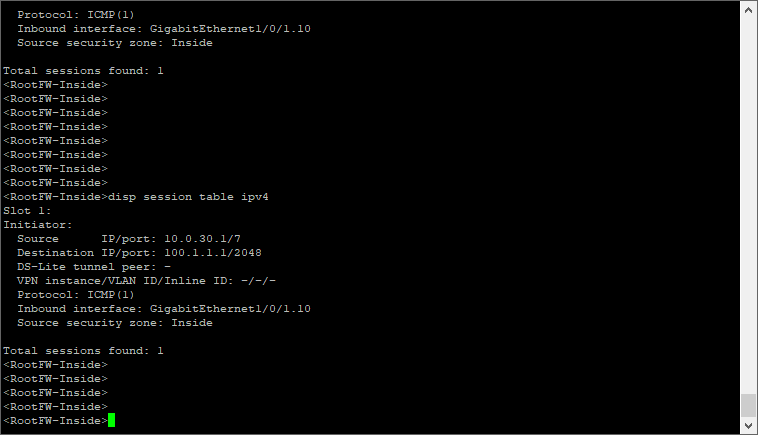
难点设备Border-Leaf配置:
#
sysname SpineAndBorder-Leaf
#建立多个VRF来隔离路由
ip vpn-instance DMZ
#
ip vpn-instance Inside
#
ip vpn-instance Inside_Internet
#
ip vpn-instance Internet
#配置与根墙建立的OSPF邻居
ospf 1 router-id 10.0.12.1 vpn-instance Internet
default-route-advertise type 1 //下发默认路由给根墙和Inside_Internet VRF
area 0.0.0.0
network 10.0.12.0 0.0.0.3
#配置与根墙建立的OSPF邻居
ospf 2 router-id 10.0.13.1 vpn-instance Inside_Internet
vpn-instance-capability simple //这里由于VPN实例下 OSPF DN-BIT置位防环,需要配置该命令解决因为防环导致路由不学习的情况,否则无法学习到Internet下发的默认路由
area 0.0.0.0
network 10.0.13.0 0.0.0.3
network 100.0.0.0 0.0.0.255 //宣告vxlan10200地址
#
ospf 3 router-id 10.0.11.1 vpn-instance DMZ
default-route-advertise type 1 //下发默认路由给虚墙和Inside VRF
area 0.0.0.0
network 10.0.11.0 0.0.0.3
network 10.0.209.0 0.0.0.255 //宣告vxlan10209地址
#
ospf 4 router-id 10.0.10.1 vpn-instance Inside
vpn-instance-capability simple //这里由于VPN实例下 OSPF DN-BIT置位防环,需要配置该命令解决因为防环导致路由不学习的情况,否则无法学习到DMZ下发的默认路由
area 0.0.0.0
network 10.0.10.0 0.0.0.3
network 10.0.30.0 0.0.0.255 //宣告vxlan10301地址
#配置Underlay层通讯使用的OSPF
ospf 100 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.0.1.0 0.0.0.3
network 10.0.1.4 0.0.0.3
#
vlan 10 to 13
#
vlan 301
#
l2vpn enable
#创建3个vxlan并且关联网关和L2 VNI
vsi vxlan10200
gateway vsi-interface 200
vxlan 10200
evpn encapsulation vxlan
route-distinguisher 1:10200
vpn-target 1:10200 export-extcommunity
vpn-target 1:10200 import-extcommunity
#
vsi vxlan10209
gateway vsi-interface 209
vxlan 10209
evpn encapsulation vxlan
route-distinguisher 1:10209
vpn-target 1:10209 export-extcommunity
vpn-target 1:10209 import-extcommunity
#
vsi vxlan10301
gateway vsi-interface 301
vxlan 10301
evpn encapsulation vxlan
route-distinguisher 1:10301
vpn-target 1:10301 export-extcommunity
vpn-target 1:10301 import-extcommunity
#
interface LoopBack0 //建立vxlan隧道使用的VTEP地址和建立BGP EVPN邻居关系的逻辑接口
ip address 1.1.1.1 255.255.255.255
#vlan逻辑接口用于与防火墙根墙、防火墙虚墙互联的接口
interface Vlan-interface10
ip binding vpn-instance Inside
ip address 10.0.10.1 255.255.255.252
ospf network-type p2p
#
interface Vlan-interface11
ip binding vpn-instance DMZ
ip address 10.0.11.1 255.255.255.252
ospf network-type p2p
#
interface Vlan-interface12
ip binding vpn-instance Internet
ip address 10.0.12.1 255.255.255.252
ospf network-type p2p
#
interface Vlan-interface13
ip binding vpn-instance Inside_Internet
ip address 10.0.13.1 255.255.255.252
ospf network-type p2p
#与Internet 互联的接口
interface GigabitEthernet1/0/1
port link-mode route
combo enable fiber
ip binding vpn-instance Internet
ip address 100.1.1.2 255.255.255.252
#
interface GigabitEthernet1/0/48
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 10 to 13
combo enable fiber
#
interface Ten-GigabitEthernet1/0/50
port link-mode route
combo enable fiber
ip address 10.0.1.1 255.255.255.252
ospf network-type p2p
#
interface Ten-GigabitEthernet1/0/51
port link-mode route
combo enable fiber
ip address 10.0.1.5 255.255.255.252
ospf network-type p2p
#
interface Vsi-interface200 //vxlan10200的网关
ip binding vpn-instance Inside_Internet
ip address 100.0.0.254 255.255.255.0
#
interface Vsi-interface209 //vxlan10209的网关
ip binding vpn-instance DMZ
ip address 10.0.209.254 255.255.255.0
#
interface Vsi-interface301 //vxlan10301的网关
ip binding vpn-instance Inside
ip address 10.0.30.254 255.255.255.0
#
bgp 100 instance EVPN //通过BGP实例的方式来建立EVPN邻居关系,这样如果以后使用BGP其他的AS号来建立传统网络邻居关系依旧可行
group Leaf internal
peer Leaf connect-interface LoopBack0
peer 1.1.1.2 group Leaf
peer 1.1.1.3 group Leaf
#
address-family l2vpn evpn //由于是集中式网关,不需要配置undo policy vpn-target,如果网络内有其他二层vxlan需要通过Spine传递的话,则需要配置,或者Spine上创建该vxlan对应的RD/RT也行
peer Leaf enable
peer Leaf reflect-client //同时Spine又作为RR存在
#
ip route-static vpn-instance Internet 0.0.0.0 0 100.1.1.1 //配置到Internet的出口的默认路由
ip route-static vpn-instance DMZ 0.0.0.0 0 10.0.209.1 //配置到DMZ中NAT-SERVER的默认路由
#
return
#
sysname SpineAndBorder-Leaf
#建立多个VRF来隔离路由
ip vpn-instance DMZ
#
ip vpn-instance Inside
#
ip vpn-instance Inside_Internet
#
ip vpn-instance Internet
#配置与根墙建立的OSPF邻居
ospf 1 router-id 10.0.12.1 vpn-instance Internet
default-route-advertise type 1 //下发默认路由给根墙和Inside_Internet VRF
area 0.0.0.0
network 10.0.12.0 0.0.0.3
#配置与根墙建立的OSPF邻居
ospf 2 router-id 10.0.13.1 vpn-instance Inside_Internet
vpn-instance-capability simple //这里由于VPN实例下 OSPF DN-BIT置位防环,需要配置该命令解决因为防环导致路由不学习的情况,否则无法学习到Internet下发的默认路由
area 0.0.0.0
network 10.0.13.0 0.0.0.3
network 100.0.0.0 0.0.0.255 //宣告vxlan10200地址
#
ospf 3 router-id 10.0.11.1 vpn-instance DMZ
default-route-advertise type 1 //下发默认路由给虚墙和Inside VRF
area 0.0.0.0
network 10.0.11.0 0.0.0.3
network 10.0.209.0 0.0.0.255 //宣告vxlan10209地址
#
ospf 4 router-id 10.0.10.1 vpn-instance Inside
vpn-instance-capability simple //这里由于VPN实例下 OSPF DN-BIT置位防环,需要配置该命令解决因为防环导致路由不学习的情况,否则无法学习到DMZ下发的默认路由
area 0.0.0.0
network 10.0.10.0 0.0.0.3
network 10.0.30.0 0.0.0.255 //宣告vxlan10301地址
#配置Underlay层通讯使用的OSPF
ospf 100 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.0.1.0 0.0.0.3
network 10.0.1.4 0.0.0.3
#
vlan 10 to 13
#
vlan 301
#
l2vpn enable
#创建3个vxlan并且关联网关和L2 VNI
vsi vxlan10200
gateway vsi-interface 200
vxlan 10200
evpn encapsulation vxlan
route-distinguisher 1:10200
vpn-target 1:10200 export-extcommunity
vpn-target 1:10200 import-extcommunity
#
vsi vxlan10209
gateway vsi-interface 209
vxlan 10209
evpn encapsulation vxlan
route-distinguisher 1:10209
vpn-target 1:10209 export-extcommunity
vpn-target 1:10209 import-extcommunity
#
vsi vxlan10301
gateway vsi-interface 301
vxlan 10301
evpn encapsulation vxlan
route-distinguisher 1:10301
vpn-target 1:10301 export-extcommunity
vpn-target 1:10301 import-extcommunity
#
interface LoopBack0 //建立vxlan隧道使用的VTEP地址和建立BGP EVPN邻居关系的逻辑接口
ip address 1.1.1.1 255.255.255.255
#vlan逻辑接口用于与防火墙根墙、防火墙虚墙互联的接口
interface Vlan-interface10
ip binding vpn-instance Inside
ip address 10.0.10.1 255.255.255.252
ospf network-type p2p
#
interface Vlan-interface11
ip binding vpn-instance DMZ
ip address 10.0.11.1 255.255.255.252
ospf network-type p2p
#
interface Vlan-interface12
ip binding vpn-instance Internet
ip address 10.0.12.1 255.255.255.252
ospf network-type p2p
#
interface Vlan-interface13
ip binding vpn-instance Inside_Internet
ip address 10.0.13.1 255.255.255.252
ospf network-type p2p
#与Internet 互联的接口
interface GigabitEthernet1/0/1
port link-mode route
combo enable fiber
ip binding vpn-instance Internet
ip address 100.1.1.2 255.255.255.252
#
interface GigabitEthernet1/0/48
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 10 to 13
combo enable fiber
#
interface Ten-GigabitEthernet1/0/50
port link-mode route
combo enable fiber
ip address 10.0.1.1 255.255.255.252
ospf network-type p2p
#
interface Ten-GigabitEthernet1/0/51
port link-mode route
combo enable fiber
ip address 10.0.1.5 255.255.255.252
ospf network-type p2p
#
interface Vsi-interface200 //vxlan10200的网关
ip binding vpn-instance Inside_Internet
ip address 100.0.0.254 255.255.255.0
#
interface Vsi-interface209 //vxlan10209的网关
ip binding vpn-instance DMZ
ip address 10.0.209.254 255.255.255.0
#
interface Vsi-interface301 //vxlan10301的网关
ip binding vpn-instance Inside
ip address 10.0.30.254 255.255.255.0
#
bgp 100 instance EVPN //通过BGP实例的方式来建立EVPN邻居关系,这样如果以后使用BGP其他的AS号来建立传统网络邻居关系依旧可行
group Leaf internal
peer Leaf connect-interface LoopBack0
peer 1.1.1.2 group Leaf
peer 1.1.1.3 group Leaf
#
address-family l2vpn evpn //由于是集中式网关,不需要配置undo policy vpn-target,如果网络内有其他二层vxlan需要通过Spine传递的话,则需要配置,或者Spine上创建该vxlan对应的RD/RT也行
peer Leaf enable
peer Leaf reflect-client //同时Spine又作为RR存在
#
ip route-static vpn-instance Internet 0.0.0.0 0 100.1.1.1 //配置到Internet的出口的默认路由
ip route-static vpn-instance DMZ 0.0.0.0 0 10.0.209.1 //配置到DMZ中NAT-SERVER的默认路由
#
return
# sysname SpineAndBorder-Leaf #建立多个VRF来隔离路由 ip vpn-instance DMZ # ip vpn-instance Inside # ip vpn-instance Inside_Internet # ip vpn-instance Internet #配置与根墙建立的OSPF邻居 ospf 1 router-id 10.0.12.1 vpn-instance Internet default-route-advertise type 1 //下发默认路由给根墙和Inside_Internet VRF area 0.0.0.0 network 10.0.12.0 0.0.0.3 #配置与根墙建立的OSPF邻居 ospf 2 router-id 10.0.13.1 vpn-instance Inside_Internet vpn-instance-capability simple //这里由于VPN实例下 OSPF DN-BIT置位防环,需要配置该命令解决因为防环导致路由不学习的情况,否则无法学习到Internet下发的默认路由 area 0.0.0.0 network 10.0.13.0 0.0.0.3 network 100.0.0.0 0.0.0.255 //宣告vxlan10200地址 # ospf 3 router-id 10.0.11.1 vpn-instance DMZ default-route-advertise type 1 //下发默认路由给虚墙和Inside VRF area 0.0.0.0 network 10.0.11.0 0.0.0.3 network 10.0.209.0 0.0.0.255 //宣告vxlan10209地址 # ospf 4 router-id 10.0.10.1 vpn-instance Inside vpn-instance-capability simple //这里由于VPN实例下 OSPF DN-BIT置位防环,需要配置该命令解决因为防环导致路由不学习的情况,否则无法学习到DMZ下发的默认路由 area 0.0.0.0 network 10.0.10.0 0.0.0.3 network 10.0.30.0 0.0.0.255 //宣告vxlan10301地址 #配置Underlay层通讯使用的OSPF ospf 100 router-id 1.1.1.1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 network 10.0.1.0 0.0.0.3 network 10.0.1.4 0.0.0.3 # vlan 10 to 13 # vlan 301 # l2vpn enable #创建3个vxlan并且关联网关和L2 VNI vsi vxlan10200 gateway vsi-interface 200 vxlan 10200 evpn encapsulation vxlan route-distinguisher 1:10200 vpn-target 1:10200 export-extcommunity vpn-target 1:10200 import-extcommunity # vsi vxlan10209 gateway vsi-interface 209 vxlan 10209 evpn encapsulation vxlan route-distinguisher 1:10209 vpn-target 1:10209 export-extcommunity vpn-target 1:10209 import-extcommunity # vsi vxlan10301 gateway vsi-interface 301 vxlan 10301 evpn encapsulation vxlan route-distinguisher 1:10301 vpn-target 1:10301 export-extcommunity vpn-target 1:10301 import-extcommunity # interface LoopBack0 //建立vxlan隧道使用的VTEP地址和建立BGP EVPN邻居关系的逻辑接口 ip address 1.1.1.1 255.255.255.255 #vlan逻辑接口用于与防火墙根墙、防火墙虚墙互联的接口 interface Vlan-interface10 ip binding vpn-instance Inside ip address 10.0.10.1 255.255.255.252 ospf network-type p2p # interface Vlan-interface11 ip binding vpn-instance DMZ ip address 10.0.11.1 255.255.255.252 ospf network-type p2p # interface Vlan-interface12 ip binding vpn-instance Internet ip address 10.0.12.1 255.255.255.252 ospf network-type p2p # interface Vlan-interface13 ip binding vpn-instance Inside_Internet ip address 10.0.13.1 255.255.255.252 ospf network-type p2p #与Internet 互联的接口 interface GigabitEthernet1/0/1 port link-mode route combo enable fiber ip binding vpn-instance Internet ip address 100.1.1.2 255.255.255.252 # interface GigabitEthernet1/0/48 port link-mode bridge port link-type trunk undo port trunk permit vlan 1 port trunk permit vlan 10 to 13 combo enable fiber # interface Ten-GigabitEthernet1/0/50 port link-mode route combo enable fiber ip address 10.0.1.1 255.255.255.252 ospf network-type p2p # interface Ten-GigabitEthernet1/0/51 port link-mode route combo enable fiber ip address 10.0.1.5 255.255.255.252 ospf network-type p2p # interface Vsi-interface200 //vxlan10200的网关 ip binding vpn-instance Inside_Internet ip address 100.0.0.254 255.255.255.0 # interface Vsi-interface209 //vxlan10209的网关 ip binding vpn-instance DMZ ip address 10.0.209.254 255.255.255.0 # interface Vsi-interface301 //vxlan10301的网关 ip binding vpn-instance Inside ip address 10.0.30.254 255.255.255.0 # bgp 100 instance EVPN //通过BGP实例的方式来建立EVPN邻居关系,这样如果以后使用BGP其他的AS号来建立传统网络邻居关系依旧可行 group Leaf internal peer Leaf connect-interface LoopBack0 peer 1.1.1.2 group Leaf peer 1.1.1.3 group Leaf # address-family l2vpn evpn //由于是集中式网关,不需要配置undo policy vpn-target,如果网络内有其他二层vxlan需要通过Spine传递的话,则需要配置,或者Spine上创建该vxlan对应的RD/RT也行 peer Leaf enable peer Leaf reflect-client //同时Spine又作为RR存在 # ip route-static vpn-instance Internet 0.0.0.0 0 100.1.1.1 //配置到Internet的出口的默认路由 ip route-static vpn-instance DMZ 0.0.0.0 0 10.0.209.1 //配置到DMZ中NAT-SERVER的默认路由 # return