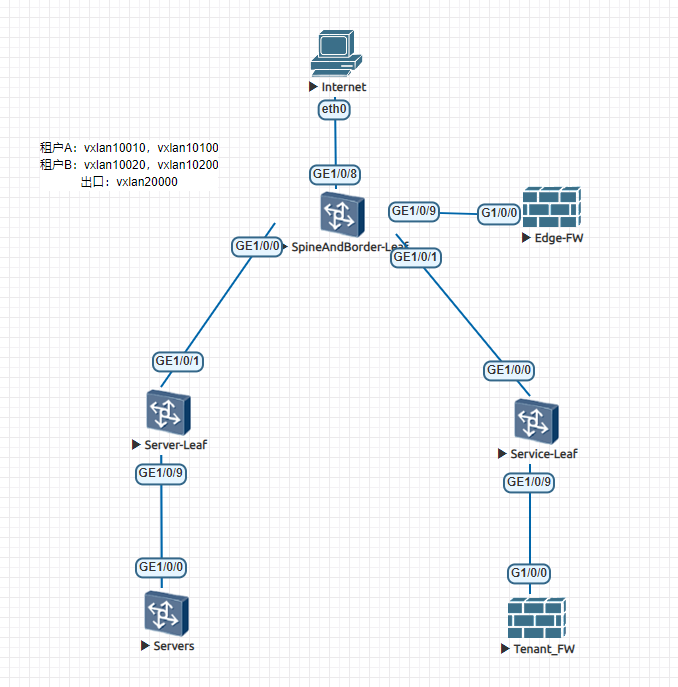
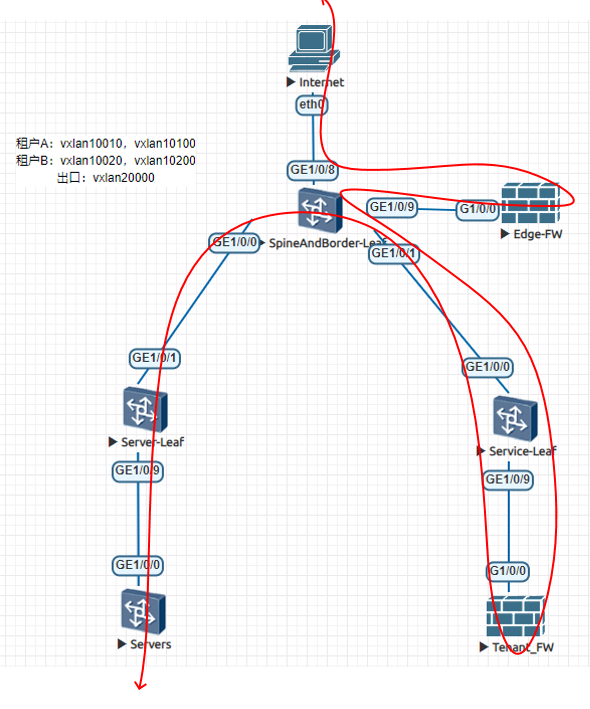
场景说明:Servers模拟虚拟机,在ServerLeaf上有两个租户分别为租户A、租户B,他们购买了各自的防火墙,在ServiceLeaf下联,Spine和Border融合部署,要求租户访问互联网流量先经过租户的防火墙,再经过边界防火墙然后访问互联网。租户防火墙采用vsys方式部署
流量路径:
关于租户防火墙内流量路径:防火墙分为根墙、租户虚墙A、租户虚墙B,流量需要先经过租户虚墙后,然后在经过根墙然后转发给Spine。
Spine/Border-Leaf配置:
sysname SpineAndBorder-Leaf
#
vlan batch 3 to 4
#
evpn-overlay enable
#两个VRF Internet和Inside_Internet用于隔离内部和外部路由,然后通过防火墙打通两个VRF
ip vpn-instance Internet
ipv4-family
route-distinguisher 1:200
vpn-target 1:200 export-extcommunity
vpn-target 1:200 import-extcommunity
#
ip vpn-instance Inside_Internet
ipv4-family
route-distinguisher 1:201
vpn-target 1:201 export-extcommunity
vpn-target 1:201 import-extcommunity
#
bridge-domain 20000 //配置与外部互联的VXLAN
vxlan vni 20000
evpn
route-distinguisher 1:20000
vpn-target 1:20000 export-extcommunity
vpn-target 1:20000 import-extcommunity
#
#
interface Vbdif20000 //承接外部流量的vxlan网关
ip binding vpn-instance Inside_Internet
ip address 10.0.255.254 255.255.255.0
#
interface Vlanif3 //与防火墙Untrust互联的接口
ip binding vpn-instance Internet
ip address 10.0.3.1 255.255.255.252
ospf network-type p2p
#
interface Vlanif4 //与防火墙Trust互联的接口
ip binding vpn-instance Inside_Internet
ip address 10.0.4.1 255.255.255.252
ospf network-type p2p
#
interface GE1/0/0
undo portswitch
undo shutdown
ip address 10.0.1.1 255.255.255.252
ospf network-type p2p
#
interface GE1/0/1
undo portswitch
undo shutdown
ip address 10.0.1.5 255.255.255.252
ospf network-type p2p
#
interface GE1/0/2
undo shutdown
#
interface GE1/0/8 //与Internet互联的接口
undo portswitch
undo shutdown
ip binding vpn-instance Internet
ip address 100.1.1.2 255.255.255.252
#
interface GE1/0/9 //与旁路防火墙互联的接口
undo shutdown
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 3 to 4
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Nve1 //配置vtep与头端复制方式
source 1.1.1.1
vni 20000 head-end peer-list protocol bgp
#
interface NULL0
#
bgp 100 instance EVPN //配置BGP EVPN,这里模拟器有BUG,采用peer group方式配置的话,会出现邻居关系无法正常建立的情况。
peer 1.1.1.2 as-number 100
peer 1.1.1.2 connect-interface LoopBack0
peer 1.1.1.3 as-number 100
peer 1.1.1.3 connect-interface LoopBack0
#
l2vpn-family evpn
undo policy vpn-target
peer 1.1.1.2 enable
peer 1.1.1.2 advertise irb //通告irb路由,如果不配置该命令,则无法正常传递主机路由
peer 1.1.1.2 reflect-client
peer 1.1.1.3 enable
peer 1.1.1.3 advertise irb //通告irb路由,如果不配置该命令,则无法正常传递主机路由
peer 1.1.1.3 reflect-client
#
ospf 1 //Underlay层通讯使用OSPF打通
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.0.1.0 0.0.0.3
network 10.0.1.4 0.0.0.3
#
ospf 100 vpn-instance Inside_Internet //与防火墙Trust互联的OSPF
import-route static
vpn-instance-capability simple
area 0.0.0.0
network 10.0.4.0 0.0.0.3
network 100.1.0.0 0.0.0.255
network 100.2.0.0 0.0.0.255
#
ospf 101 vpn-instance Internet //与防火墙Untrust互联的OSPF
default-route-advertise
area 0.0.0.0
network 10.0.3.0 0.0.0.3
#
ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 100.1.1.1
ip route-static vpn-instance Inside_Internet 100.1.0.0 255.255.255.0 10.0.255.1 //回程路由到租户防火墙
ip route-static vpn-instance Inside_Internet 100.2.0.0 255.255.255.0 10.0.255.1 //回程路由到租户防火墙
sysname SpineAndBorder-Leaf
#
vlan batch 3 to 4
#
evpn-overlay enable
#两个VRF Internet和Inside_Internet用于隔离内部和外部路由,然后通过防火墙打通两个VRF
ip vpn-instance Internet
ipv4-family
route-distinguisher 1:200
vpn-target 1:200 export-extcommunity
vpn-target 1:200 import-extcommunity
#
ip vpn-instance Inside_Internet
ipv4-family
route-distinguisher 1:201
vpn-target 1:201 export-extcommunity
vpn-target 1:201 import-extcommunity
#
bridge-domain 20000 //配置与外部互联的VXLAN
vxlan vni 20000
evpn
route-distinguisher 1:20000
vpn-target 1:20000 export-extcommunity
vpn-target 1:20000 import-extcommunity
#
#
interface Vbdif20000 //承接外部流量的vxlan网关
ip binding vpn-instance Inside_Internet
ip address 10.0.255.254 255.255.255.0
#
interface Vlanif3 //与防火墙Untrust互联的接口
ip binding vpn-instance Internet
ip address 10.0.3.1 255.255.255.252
ospf network-type p2p
#
interface Vlanif4 //与防火墙Trust互联的接口
ip binding vpn-instance Inside_Internet
ip address 10.0.4.1 255.255.255.252
ospf network-type p2p
#
interface GE1/0/0
undo portswitch
undo shutdown
ip address 10.0.1.1 255.255.255.252
ospf network-type p2p
#
interface GE1/0/1
undo portswitch
undo shutdown
ip address 10.0.1.5 255.255.255.252
ospf network-type p2p
#
interface GE1/0/2
undo shutdown
#
interface GE1/0/8 //与Internet互联的接口
undo portswitch
undo shutdown
ip binding vpn-instance Internet
ip address 100.1.1.2 255.255.255.252
#
interface GE1/0/9 //与旁路防火墙互联的接口
undo shutdown
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 3 to 4
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Nve1 //配置vtep与头端复制方式
source 1.1.1.1
vni 20000 head-end peer-list protocol bgp
#
interface NULL0
#
bgp 100 instance EVPN //配置BGP EVPN,这里模拟器有BUG,采用peer group方式配置的话,会出现邻居关系无法正常建立的情况。
peer 1.1.1.2 as-number 100
peer 1.1.1.2 connect-interface LoopBack0
peer 1.1.1.3 as-number 100
peer 1.1.1.3 connect-interface LoopBack0
#
l2vpn-family evpn
undo policy vpn-target
peer 1.1.1.2 enable
peer 1.1.1.2 advertise irb //通告irb路由,如果不配置该命令,则无法正常传递主机路由
peer 1.1.1.2 reflect-client
peer 1.1.1.3 enable
peer 1.1.1.3 advertise irb //通告irb路由,如果不配置该命令,则无法正常传递主机路由
peer 1.1.1.3 reflect-client
#
ospf 1 //Underlay层通讯使用OSPF打通
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.0.1.0 0.0.0.3
network 10.0.1.4 0.0.0.3
#
ospf 100 vpn-instance Inside_Internet //与防火墙Trust互联的OSPF
import-route static
vpn-instance-capability simple
area 0.0.0.0
network 10.0.4.0 0.0.0.3
network 100.1.0.0 0.0.0.255
network 100.2.0.0 0.0.0.255
#
ospf 101 vpn-instance Internet //与防火墙Untrust互联的OSPF
default-route-advertise
area 0.0.0.0
network 10.0.3.0 0.0.0.3
#
ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 100.1.1.1
ip route-static vpn-instance Inside_Internet 100.1.0.0 255.255.255.0 10.0.255.1 //回程路由到租户防火墙
ip route-static vpn-instance Inside_Internet 100.2.0.0 255.255.255.0 10.0.255.1 //回程路由到租户防火墙
sysname SpineAndBorder-Leaf # vlan batch 3 to 4 # evpn-overlay enable #两个VRF Internet和Inside_Internet用于隔离内部和外部路由,然后通过防火墙打通两个VRF ip vpn-instance Internet ipv4-family route-distinguisher 1:200 vpn-target 1:200 export-extcommunity vpn-target 1:200 import-extcommunity # ip vpn-instance Inside_Internet ipv4-family route-distinguisher 1:201 vpn-target 1:201 export-extcommunity vpn-target 1:201 import-extcommunity # bridge-domain 20000 //配置与外部互联的VXLAN vxlan vni 20000 evpn route-distinguisher 1:20000 vpn-target 1:20000 export-extcommunity vpn-target 1:20000 import-extcommunity # # interface Vbdif20000 //承接外部流量的vxlan网关 ip binding vpn-instance Inside_Internet ip address 10.0.255.254 255.255.255.0 # interface Vlanif3 //与防火墙Untrust互联的接口 ip binding vpn-instance Internet ip address 10.0.3.1 255.255.255.252 ospf network-type p2p # interface Vlanif4 //与防火墙Trust互联的接口 ip binding vpn-instance Inside_Internet ip address 10.0.4.1 255.255.255.252 ospf network-type p2p # interface GE1/0/0 undo portswitch undo shutdown ip address 10.0.1.1 255.255.255.252 ospf network-type p2p # interface GE1/0/1 undo portswitch undo shutdown ip address 10.0.1.5 255.255.255.252 ospf network-type p2p # interface GE1/0/2 undo shutdown # interface GE1/0/8 //与Internet互联的接口 undo portswitch undo shutdown ip binding vpn-instance Internet ip address 100.1.1.2 255.255.255.252 # interface GE1/0/9 //与旁路防火墙互联的接口 undo shutdown port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 3 to 4 # interface LoopBack0 ip address 1.1.1.1 255.255.255.255 # interface Nve1 //配置vtep与头端复制方式 source 1.1.1.1 vni 20000 head-end peer-list protocol bgp # interface NULL0 # bgp 100 instance EVPN //配置BGP EVPN,这里模拟器有BUG,采用peer group方式配置的话,会出现邻居关系无法正常建立的情况。 peer 1.1.1.2 as-number 100 peer 1.1.1.2 connect-interface LoopBack0 peer 1.1.1.3 as-number 100 peer 1.1.1.3 connect-interface LoopBack0 # l2vpn-family evpn undo policy vpn-target peer 1.1.1.2 enable peer 1.1.1.2 advertise irb //通告irb路由,如果不配置该命令,则无法正常传递主机路由 peer 1.1.1.2 reflect-client peer 1.1.1.3 enable peer 1.1.1.3 advertise irb //通告irb路由,如果不配置该命令,则无法正常传递主机路由 peer 1.1.1.3 reflect-client # ospf 1 //Underlay层通讯使用OSPF打通 area 0.0.0.0 network 1.1.1.1 0.0.0.0 network 10.0.1.0 0.0.0.3 network 10.0.1.4 0.0.0.3 # ospf 100 vpn-instance Inside_Internet //与防火墙Trust互联的OSPF import-route static vpn-instance-capability simple area 0.0.0.0 network 10.0.4.0 0.0.0.3 network 100.1.0.0 0.0.0.255 network 100.2.0.0 0.0.0.255 # ospf 101 vpn-instance Internet //与防火墙Untrust互联的OSPF default-route-advertise area 0.0.0.0 network 10.0.3.0 0.0.0.3 # ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 100.1.1.1 ip route-static vpn-instance Inside_Internet 100.1.0.0 255.255.255.0 10.0.255.1 //回程路由到租户防火墙 ip route-static vpn-instance Inside_Internet 100.2.0.0 255.255.255.0 10.0.255.1 //回程路由到租户防火墙
Server-Leaf配置:
sysname Server-Leaf
#
vlan batch 10 20
#
evpn-overlay enable
#
evpn
#
ip vpn-instance A //配置租户A的VRF
ipv4-family
route-distinguisher 1:1000
vpn-target 1:1000 export-extcommunity
vpn-target 1:1000 export-extcommunity evpn //这里一定要配置带EVPN的RT值,如果不配置,那么5类路由不会加入路由表
vpn-target 1:1000 import-extcommunity
vpn-target 1:1000 import-extcommunity evpn
vxlan vni 1000 //L3 VNI
#
ip vpn-instance B //配置租户B的VRF
ipv4-family
route-distinguisher 1:2000
vpn-target 1:2000 export-extcommunity
vpn-target 1:2000 export-extcommunity evpn //这里一定要配置带EVPN的RT值,如果不配置,那么5类路由不会加入路由表
vpn-target 1:2000 import-extcommunity
vpn-target 1:2000 import-extcommunity evpn
vxlan vni 2000 //L3 VNI
#
bridge-domain 10010
vxlan vni 10010
evpn
route-distinguisher 1:10010
vpn-target 1:10010 export-extcommunity
vpn-target 1:1000 export-extcommunity //配置租户A的RT交叉
vpn-target 1:10010 import-extcommunity
#
bridge-domain 10020
vxlan vni 10020
evpn
route-distinguisher 1:10020
vpn-target 1:10020 export-extcommunity
vpn-target 1:2000 export-extcommunity
vpn-target 1:10020 import-extcommunity
#
interface Vbdif10010
ip binding vpn-instance A
ip address 192.168.10.254 255.255.255.0
arp collect host enable //配置通过ARP表项来生成32位主机路由
#
interface Vbdif10020
ip binding vpn-instance B
ip address 192.168.20.254 255.255.255.0
arp collect host enable //配置通过ARP表项来生成32位主机路由
#
interface GE1/0/1
undo portswitch
undo shutdown
ip address 10.0.1.2 255.255.255.252
ospf network-type p2p
#
interface GE1/0/9
undo shutdown
port link-type trunk
#
interface GE1/0/9.10 mode l2
encapsulation dot1q vid 10
bridge-domain 10010
#
interface GE1/0/9.20 mode l2
encapsulation dot1q vid 20
bridge-domain 10020
#
interface LoopBack0
ip address 1.1.1.2 255.255.255.255
#
interface Nve1
source 1.1.1.2
vni 10010 head-end peer-list protocol bgp
vni 10020 head-end peer-list protocol bgp
#
interface NULL0
#
bgp 100
undo default ipv4-unicast
peer 1.1.1.1 as-number 100
peer 1.1.1.1 connect-interface LoopBack0
#
ipv4-family unicast
undo peer 1.1.1.1 enable
#
l2vpn-family evpn
policy vpn-target
peer 1.1.1.1 enable
peer 1.1.1.1 advertise irb
#
ospf 1
area 0.0.0.0
network 1.1.1.2 0.0.0.0
network 10.0.1.0 0.0.0.3
#
sysname Server-Leaf
#
vlan batch 10 20
#
evpn-overlay enable
#
evpn
#
ip vpn-instance A //配置租户A的VRF
ipv4-family
route-distinguisher 1:1000
vpn-target 1:1000 export-extcommunity
vpn-target 1:1000 export-extcommunity evpn //这里一定要配置带EVPN的RT值,如果不配置,那么5类路由不会加入路由表
vpn-target 1:1000 import-extcommunity
vpn-target 1:1000 import-extcommunity evpn
vxlan vni 1000 //L3 VNI
#
ip vpn-instance B //配置租户B的VRF
ipv4-family
route-distinguisher 1:2000
vpn-target 1:2000 export-extcommunity
vpn-target 1:2000 export-extcommunity evpn //这里一定要配置带EVPN的RT值,如果不配置,那么5类路由不会加入路由表
vpn-target 1:2000 import-extcommunity
vpn-target 1:2000 import-extcommunity evpn
vxlan vni 2000 //L3 VNI
#
bridge-domain 10010
vxlan vni 10010
evpn
route-distinguisher 1:10010
vpn-target 1:10010 export-extcommunity
vpn-target 1:1000 export-extcommunity //配置租户A的RT交叉
vpn-target 1:10010 import-extcommunity
#
bridge-domain 10020
vxlan vni 10020
evpn
route-distinguisher 1:10020
vpn-target 1:10020 export-extcommunity
vpn-target 1:2000 export-extcommunity
vpn-target 1:10020 import-extcommunity
#
interface Vbdif10010
ip binding vpn-instance A
ip address 192.168.10.254 255.255.255.0
arp collect host enable //配置通过ARP表项来生成32位主机路由
#
interface Vbdif10020
ip binding vpn-instance B
ip address 192.168.20.254 255.255.255.0
arp collect host enable //配置通过ARP表项来生成32位主机路由
#
interface GE1/0/1
undo portswitch
undo shutdown
ip address 10.0.1.2 255.255.255.252
ospf network-type p2p
#
interface GE1/0/9
undo shutdown
port link-type trunk
#
interface GE1/0/9.10 mode l2
encapsulation dot1q vid 10
bridge-domain 10010
#
interface GE1/0/9.20 mode l2
encapsulation dot1q vid 20
bridge-domain 10020
#
interface LoopBack0
ip address 1.1.1.2 255.255.255.255
#
interface Nve1
source 1.1.1.2
vni 10010 head-end peer-list protocol bgp
vni 10020 head-end peer-list protocol bgp
#
interface NULL0
#
bgp 100
undo default ipv4-unicast
peer 1.1.1.1 as-number 100
peer 1.1.1.1 connect-interface LoopBack0
#
ipv4-family unicast
undo peer 1.1.1.1 enable
#
l2vpn-family evpn
policy vpn-target
peer 1.1.1.1 enable
peer 1.1.1.1 advertise irb
#
ospf 1
area 0.0.0.0
network 1.1.1.2 0.0.0.0
network 10.0.1.0 0.0.0.3
#
sysname Server-Leaf # vlan batch 10 20 # evpn-overlay enable # evpn # ip vpn-instance A //配置租户A的VRF ipv4-family route-distinguisher 1:1000 vpn-target 1:1000 export-extcommunity vpn-target 1:1000 export-extcommunity evpn //这里一定要配置带EVPN的RT值,如果不配置,那么5类路由不会加入路由表 vpn-target 1:1000 import-extcommunity vpn-target 1:1000 import-extcommunity evpn vxlan vni 1000 //L3 VNI # ip vpn-instance B //配置租户B的VRF ipv4-family route-distinguisher 1:2000 vpn-target 1:2000 export-extcommunity vpn-target 1:2000 export-extcommunity evpn //这里一定要配置带EVPN的RT值,如果不配置,那么5类路由不会加入路由表 vpn-target 1:2000 import-extcommunity vpn-target 1:2000 import-extcommunity evpn vxlan vni 2000 //L3 VNI # bridge-domain 10010 vxlan vni 10010 evpn route-distinguisher 1:10010 vpn-target 1:10010 export-extcommunity vpn-target 1:1000 export-extcommunity //配置租户A的RT交叉 vpn-target 1:10010 import-extcommunity # bridge-domain 10020 vxlan vni 10020 evpn route-distinguisher 1:10020 vpn-target 1:10020 export-extcommunity vpn-target 1:2000 export-extcommunity vpn-target 1:10020 import-extcommunity # interface Vbdif10010 ip binding vpn-instance A ip address 192.168.10.254 255.255.255.0 arp collect host enable //配置通过ARP表项来生成32位主机路由 # interface Vbdif10020 ip binding vpn-instance B ip address 192.168.20.254 255.255.255.0 arp collect host enable //配置通过ARP表项来生成32位主机路由 # interface GE1/0/1 undo portswitch undo shutdown ip address 10.0.1.2 255.255.255.252 ospf network-type p2p # interface GE1/0/9 undo shutdown port link-type trunk # interface GE1/0/9.10 mode l2 encapsulation dot1q vid 10 bridge-domain 10010 # interface GE1/0/9.20 mode l2 encapsulation dot1q vid 20 bridge-domain 10020 # interface LoopBack0 ip address 1.1.1.2 255.255.255.255 # interface Nve1 source 1.1.1.2 vni 10010 head-end peer-list protocol bgp vni 10020 head-end peer-list protocol bgp # interface NULL0 # bgp 100 undo default ipv4-unicast peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack0 # ipv4-family unicast undo peer 1.1.1.1 enable # l2vpn-family evpn policy vpn-target peer 1.1.1.1 enable peer 1.1.1.1 advertise irb # ospf 1 area 0.0.0.0 network 1.1.1.2 0.0.0.0 network 10.0.1.0 0.0.0.3 #
Service-Leaf配置:
sysname Service-Leaf
#
evpn-overlay enable
#
ip vpn-instance A
ipv4-family
route-distinguisher 1:1000
vpn-target 1:1000 export-extcommunity
vpn-target 1:1000 export-extcommunity evpn
vpn-target 1:1000 import-extcommunity
vpn-target 1:1000 import-extcommunity evpn
vxlan vni 1000
#
ip vpn-instance B
ipv4-family
route-distinguisher 1:2000
vpn-target 1:2000 export-extcommunity
vpn-target 1:2000 export-extcommunity evpn
vpn-target 1:2000 import-extcommunity
vpn-target 1:2000 import-extcommunity evpn
vxlan vni 2000
#
bridge-domain 10100
vxlan vni 10100
evpn
route-distinguisher 1:10100
vpn-target 1:10100 export-extcommunity
vpn-target 1:1000 export-extcommunity //配置租户的交叉ERT
vpn-target 1:10100 import-extcommunity
#
bridge-domain 10200
vxlan vni 10200
evpn
route-distinguisher 1:10200
vpn-target 1:10200 export-extcommunity
vpn-target 1:2000 export-extcommunity //配置租户的交叉ERT
vpn-target 1:10200 import-extcommunity
#
bridge-domain 20000 //与外部通讯的vxlan20000
vxlan vni 20000
evpn
route-distinguisher 1:20000
vpn-target 1:20000 export-extcommunity
vpn-target 1:20000 import-extcommunity
#
interface Vbdif10100
ip binding vpn-instance A
ip address 10.0.100.254 255.255.255.0
arp collect host enable
#
interface Vbdif10200
ip binding vpn-instance B
ip address 10.0.200.254 255.255.255.0
#
interface MEth0/0/0
undo shutdown
#
interface GE1/0/0
undo portswitch
undo shutdown
ip address 10.0.1.6 255.255.255.252
ospf network-type p2p
#
interface GE1/0/9
undo shutdown
port link-type trunk
#
interface GE1/0/9.100 mode l2
encapsulation dot1q vid 100
bridge-domain 10100
#
interface GE1/0/9.200 mode l2
encapsulation dot1q vid 200
bridge-domain 10200
#
interface GE1/0/9.255 mode l2
encapsulation dot1q vid 255
bridge-domain 20000
#
interface LoopBack0
ip address 1.1.1.3 255.255.255.255
#
interface Nve1
source 1.1.1.3
vni 20000 head-end peer-list protocol bgp
#
bgp 100
undo default ipv4-unicast
peer 1.1.1.1 as-number 100
peer 1.1.1.1 connect-interface LoopBack0
#
ipv4-family unicast
undo peer 1.1.1.1 enable
#
ipv4-family vpn-instance A //配置租户的路由,且允许引入默认路由,并且允许将租户路由通过EVPN方式通告
default-route imported
import-route static
advertise l2vpn evpn
#
ipv4-family vpn-instance B //配置租户的路由,且允许引入默认路由,并且允许将租户路由通过EVPN方式通告
default-route imported
import-route static
advertise l2vpn evpn
#
l2vpn-family evpn
policy vpn-target
peer 1.1.1.1 enable
peer 1.1.1.1 advertise irb
#
ospf 1
area 0.0.0.0
network 1.1.1.3 0.0.0.0
network 10.0.1.4 0.0.0.3
#
ip route-static vpn-instance A 0.0.0.0 0.0.0.0 10.0.100.1 //将流量引流到租户防火墙
ip route-static vpn-instance B 0.0.0.0 0.0.0.0 10.0.200.1 //将流量引流到租户防火墙
#
return
sysname Service-Leaf
#
evpn-overlay enable
#
ip vpn-instance A
ipv4-family
route-distinguisher 1:1000
vpn-target 1:1000 export-extcommunity
vpn-target 1:1000 export-extcommunity evpn
vpn-target 1:1000 import-extcommunity
vpn-target 1:1000 import-extcommunity evpn
vxlan vni 1000
#
ip vpn-instance B
ipv4-family
route-distinguisher 1:2000
vpn-target 1:2000 export-extcommunity
vpn-target 1:2000 export-extcommunity evpn
vpn-target 1:2000 import-extcommunity
vpn-target 1:2000 import-extcommunity evpn
vxlan vni 2000
#
bridge-domain 10100
vxlan vni 10100
evpn
route-distinguisher 1:10100
vpn-target 1:10100 export-extcommunity
vpn-target 1:1000 export-extcommunity //配置租户的交叉ERT
vpn-target 1:10100 import-extcommunity
#
bridge-domain 10200
vxlan vni 10200
evpn
route-distinguisher 1:10200
vpn-target 1:10200 export-extcommunity
vpn-target 1:2000 export-extcommunity //配置租户的交叉ERT
vpn-target 1:10200 import-extcommunity
#
bridge-domain 20000 //与外部通讯的vxlan20000
vxlan vni 20000
evpn
route-distinguisher 1:20000
vpn-target 1:20000 export-extcommunity
vpn-target 1:20000 import-extcommunity
#
interface Vbdif10100
ip binding vpn-instance A
ip address 10.0.100.254 255.255.255.0
arp collect host enable
#
interface Vbdif10200
ip binding vpn-instance B
ip address 10.0.200.254 255.255.255.0
#
interface MEth0/0/0
undo shutdown
#
interface GE1/0/0
undo portswitch
undo shutdown
ip address 10.0.1.6 255.255.255.252
ospf network-type p2p
#
interface GE1/0/9
undo shutdown
port link-type trunk
#
interface GE1/0/9.100 mode l2
encapsulation dot1q vid 100
bridge-domain 10100
#
interface GE1/0/9.200 mode l2
encapsulation dot1q vid 200
bridge-domain 10200
#
interface GE1/0/9.255 mode l2
encapsulation dot1q vid 255
bridge-domain 20000
#
interface LoopBack0
ip address 1.1.1.3 255.255.255.255
#
interface Nve1
source 1.1.1.3
vni 20000 head-end peer-list protocol bgp
#
bgp 100
undo default ipv4-unicast
peer 1.1.1.1 as-number 100
peer 1.1.1.1 connect-interface LoopBack0
#
ipv4-family unicast
undo peer 1.1.1.1 enable
#
ipv4-family vpn-instance A //配置租户的路由,且允许引入默认路由,并且允许将租户路由通过EVPN方式通告
default-route imported
import-route static
advertise l2vpn evpn
#
ipv4-family vpn-instance B //配置租户的路由,且允许引入默认路由,并且允许将租户路由通过EVPN方式通告
default-route imported
import-route static
advertise l2vpn evpn
#
l2vpn-family evpn
policy vpn-target
peer 1.1.1.1 enable
peer 1.1.1.1 advertise irb
#
ospf 1
area 0.0.0.0
network 1.1.1.3 0.0.0.0
network 10.0.1.4 0.0.0.3
#
ip route-static vpn-instance A 0.0.0.0 0.0.0.0 10.0.100.1 //将流量引流到租户防火墙
ip route-static vpn-instance B 0.0.0.0 0.0.0.0 10.0.200.1 //将流量引流到租户防火墙
#
return
sysname Service-Leaf # evpn-overlay enable # ip vpn-instance A ipv4-family route-distinguisher 1:1000 vpn-target 1:1000 export-extcommunity vpn-target 1:1000 export-extcommunity evpn vpn-target 1:1000 import-extcommunity vpn-target 1:1000 import-extcommunity evpn vxlan vni 1000 # ip vpn-instance B ipv4-family route-distinguisher 1:2000 vpn-target 1:2000 export-extcommunity vpn-target 1:2000 export-extcommunity evpn vpn-target 1:2000 import-extcommunity vpn-target 1:2000 import-extcommunity evpn vxlan vni 2000 # bridge-domain 10100 vxlan vni 10100 evpn route-distinguisher 1:10100 vpn-target 1:10100 export-extcommunity vpn-target 1:1000 export-extcommunity //配置租户的交叉ERT vpn-target 1:10100 import-extcommunity # bridge-domain 10200 vxlan vni 10200 evpn route-distinguisher 1:10200 vpn-target 1:10200 export-extcommunity vpn-target 1:2000 export-extcommunity //配置租户的交叉ERT vpn-target 1:10200 import-extcommunity # bridge-domain 20000 //与外部通讯的vxlan20000 vxlan vni 20000 evpn route-distinguisher 1:20000 vpn-target 1:20000 export-extcommunity vpn-target 1:20000 import-extcommunity # interface Vbdif10100 ip binding vpn-instance A ip address 10.0.100.254 255.255.255.0 arp collect host enable # interface Vbdif10200 ip binding vpn-instance B ip address 10.0.200.254 255.255.255.0 # interface MEth0/0/0 undo shutdown # interface GE1/0/0 undo portswitch undo shutdown ip address 10.0.1.6 255.255.255.252 ospf network-type p2p # interface GE1/0/9 undo shutdown port link-type trunk # interface GE1/0/9.100 mode l2 encapsulation dot1q vid 100 bridge-domain 10100 # interface GE1/0/9.200 mode l2 encapsulation dot1q vid 200 bridge-domain 10200 # interface GE1/0/9.255 mode l2 encapsulation dot1q vid 255 bridge-domain 20000 # interface LoopBack0 ip address 1.1.1.3 255.255.255.255 # interface Nve1 source 1.1.1.3 vni 20000 head-end peer-list protocol bgp # bgp 100 undo default ipv4-unicast peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack0 # ipv4-family unicast undo peer 1.1.1.1 enable # ipv4-family vpn-instance A //配置租户的路由,且允许引入默认路由,并且允许将租户路由通过EVPN方式通告 default-route imported import-route static advertise l2vpn evpn # ipv4-family vpn-instance B //配置租户的路由,且允许引入默认路由,并且允许将租户路由通过EVPN方式通告 default-route imported import-route static advertise l2vpn evpn # l2vpn-family evpn policy vpn-target peer 1.1.1.1 enable peer 1.1.1.1 advertise irb # ospf 1 area 0.0.0.0 network 1.1.1.3 0.0.0.0 network 10.0.1.4 0.0.0.3 # ip route-static vpn-instance A 0.0.0.0 0.0.0.0 10.0.100.1 //将流量引流到租户防火墙 ip route-static vpn-instance B 0.0.0.0 0.0.0.0 10.0.200.1 //将流量引流到租户防火墙 # return
租户防火墙配置:
!Software Version V500R005C00SPC100
#
sysname Tenant_FW
#
vsys enable
#
vsys name A 1 //创建虚墙A并分配相应端口和公网IP
assign interface GigabitEthernet1/0/0.100
assign global-ip 100.1.0.100 100.1.0.200 exclusive
#
vsys name B 2 //创建虚墙B并分配相应端口和公网IP
assign interface GigabitEthernet1/0/0.200
assign global-ip 100.2.0.100 100.2.0.200 exclusive
#
ip vpn-instance A
ipv4-family
#
ip vpn-instance B
ipv4-family
#
ip vpn-instance default
ipv4-family
#配置根墙、虚墙所归属的子接口
interface GigabitEthernet1/0/0.100
vlan-type dot1q 100
ip binding vpn-instance A
ip address 10.0.100.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0.200
vlan-type dot1q 200
ip binding vpn-instance B
ip address 10.0.200.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0.255
vlan-type dot1q 255
ip address 10.0.255.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface Virtual-if0 //这里防火墙虚拟内联口需要配置地址才会生成路由,可以是根墙和虚墙可以同子网地址也可以是不同子网地址。
ip address 1.1.1.1 255.255.255.0
#
interface Virtual-if1
ip address 1.1.1.2 255.255.255.0
#
interface Virtual-if2
ip address 1.1.3.1 255.255.255.0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface Virtual-if0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0.255
#
firewall zone dmz
set priority 50
#
api
#
ip route-static 0.0.0.0 0.0.0.0 10.0.255.254
ip route-static 100.1.0.0 255.255.255.0 vpn-instance A //配置虚墙A的回程路由
ip route-static 100.2.0.0 255.255.255.0 vpn-instance B //配置虚墙B的回程路由
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 100.1.0.0 mask 255.255.255.0
source-address 100.2.0.0 mask 255.255.255.0
action permit
#############################################虚墙A的配置##################################################
switch vsys A
#
interface GigabitEthernet1/0/0.100
vlan-type dot1q 100
ip binding vpn-instance A
ip address 10.0.100.1 255.255.255.0
service-manage ping permit
#
interface Virtual-if1
ip address 1.1.1.2 255.255.255.0
#
sa
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0.100
#
firewall zone untrust
set priority 5
add interface Virtual-if1
#
firewall zone dmz
set priority 50
#
location
#
nat address-group SNAT 1
mode pat
route enable
section 0 100.1.0.100 100.1.0.100
#
multi-linkif
mode proportion-of-weight
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Local_Trust_Permit
source-zone local
destination-zone trust
action permit
#
nat-policy //将租户VPC内地址转换为公网地址SNAT方式
rule name Trust_Untrust_SNAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action source-nat address-group SNAT
#
ip route-static 0.0.0.0 0.0.0.0 public //配置去往根墙的路由
ip route-static 192.168.10.0 255.255.255.0 10.0.100.254 //回程路由
#
return
#
#############################################虚墙B的配置##################################################
switch vsys B
#
interface GigabitEthernet1/0/0.200
vlan-type dot1q 200
ip binding vpn-instance B
ip address 10.0.200.1 255.255.255.0
service-manage ping permit
#
interface Virtual-if2
ip address 1.1.3.1 255.255.255.0
#
sa
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0.200
#
firewall zone untrust
set priority 5
add interface Virtual-if2
#
firewall zone dmz
set priority 50
#
location
#
nat address-group SNAT 0
mode pat
route enable
section 0 100.2.0.100 100.2.0.100
#
multi-linkif
mode proportion-of-weight
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Local_Trust_Permit
source-zone local
destination-zone trust
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy //将租户VPC内地址转换为公网地址SNAT方式
rule name Trust_Untrust_SNAT
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action source-nat address-group SNAT
#
proxy-policy
#
pcp-policy
#
ip route-static 0.0.0.0 0.0.0.0 public //配置去往根墙的路由
ip route-static 192.168.20.0 255.255.255.0 10.0.200.254 //回程路由
#
return
!Software Version V500R005C00SPC100
#
sysname Tenant_FW
#
vsys enable
#
vsys name A 1 //创建虚墙A并分配相应端口和公网IP
assign interface GigabitEthernet1/0/0.100
assign global-ip 100.1.0.100 100.1.0.200 exclusive
#
vsys name B 2 //创建虚墙B并分配相应端口和公网IP
assign interface GigabitEthernet1/0/0.200
assign global-ip 100.2.0.100 100.2.0.200 exclusive
#
ip vpn-instance A
ipv4-family
#
ip vpn-instance B
ipv4-family
#
ip vpn-instance default
ipv4-family
#配置根墙、虚墙所归属的子接口
interface GigabitEthernet1/0/0.100
vlan-type dot1q 100
ip binding vpn-instance A
ip address 10.0.100.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0.200
vlan-type dot1q 200
ip binding vpn-instance B
ip address 10.0.200.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0.255
vlan-type dot1q 255
ip address 10.0.255.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface Virtual-if0 //这里防火墙虚拟内联口需要配置地址才会生成路由,可以是根墙和虚墙可以同子网地址也可以是不同子网地址。
ip address 1.1.1.1 255.255.255.0
#
interface Virtual-if1
ip address 1.1.1.2 255.255.255.0
#
interface Virtual-if2
ip address 1.1.3.1 255.255.255.0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface Virtual-if0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0.255
#
firewall zone dmz
set priority 50
#
api
#
ip route-static 0.0.0.0 0.0.0.0 10.0.255.254
ip route-static 100.1.0.0 255.255.255.0 vpn-instance A //配置虚墙A的回程路由
ip route-static 100.2.0.0 255.255.255.0 vpn-instance B //配置虚墙B的回程路由
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 100.1.0.0 mask 255.255.255.0
source-address 100.2.0.0 mask 255.255.255.0
action permit
#############################################虚墙A的配置##################################################
switch vsys A
#
interface GigabitEthernet1/0/0.100
vlan-type dot1q 100
ip binding vpn-instance A
ip address 10.0.100.1 255.255.255.0
service-manage ping permit
#
interface Virtual-if1
ip address 1.1.1.2 255.255.255.0
#
sa
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0.100
#
firewall zone untrust
set priority 5
add interface Virtual-if1
#
firewall zone dmz
set priority 50
#
location
#
nat address-group SNAT 1
mode pat
route enable
section 0 100.1.0.100 100.1.0.100
#
multi-linkif
mode proportion-of-weight
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Local_Trust_Permit
source-zone local
destination-zone trust
action permit
#
nat-policy //将租户VPC内地址转换为公网地址SNAT方式
rule name Trust_Untrust_SNAT
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action source-nat address-group SNAT
#
ip route-static 0.0.0.0 0.0.0.0 public //配置去往根墙的路由
ip route-static 192.168.10.0 255.255.255.0 10.0.100.254 //回程路由
#
return
#
#############################################虚墙B的配置##################################################
switch vsys B
#
interface GigabitEthernet1/0/0.200
vlan-type dot1q 200
ip binding vpn-instance B
ip address 10.0.200.1 255.255.255.0
service-manage ping permit
#
interface Virtual-if2
ip address 1.1.3.1 255.255.255.0
#
sa
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0.200
#
firewall zone untrust
set priority 5
add interface Virtual-if2
#
firewall zone dmz
set priority 50
#
location
#
nat address-group SNAT 0
mode pat
route enable
section 0 100.2.0.100 100.2.0.100
#
multi-linkif
mode proportion-of-weight
#
security-policy
rule name Trust_Untrust_Permit
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Local_Trust_Permit
source-zone local
destination-zone trust
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy //将租户VPC内地址转换为公网地址SNAT方式
rule name Trust_Untrust_SNAT
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action source-nat address-group SNAT
#
proxy-policy
#
pcp-policy
#
ip route-static 0.0.0.0 0.0.0.0 public //配置去往根墙的路由
ip route-static 192.168.20.0 255.255.255.0 10.0.200.254 //回程路由
#
return
!Software Version V500R005C00SPC100 # sysname Tenant_FW # vsys enable # vsys name A 1 //创建虚墙A并分配相应端口和公网IP assign interface GigabitEthernet1/0/0.100 assign global-ip 100.1.0.100 100.1.0.200 exclusive # vsys name B 2 //创建虚墙B并分配相应端口和公网IP assign interface GigabitEthernet1/0/0.200 assign global-ip 100.2.0.100 100.2.0.200 exclusive # ip vpn-instance A ipv4-family # ip vpn-instance B ipv4-family # ip vpn-instance default ipv4-family #配置根墙、虚墙所归属的子接口 interface GigabitEthernet1/0/0.100 vlan-type dot1q 100 ip binding vpn-instance A ip address 10.0.100.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/0.200 vlan-type dot1q 200 ip binding vpn-instance B ip address 10.0.200.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/0.255 vlan-type dot1q 255 ip address 10.0.255.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown # interface GigabitEthernet1/0/2 undo shutdown # interface GigabitEthernet1/0/3 undo shutdown # interface GigabitEthernet1/0/4 undo shutdown # interface Virtual-if0 //这里防火墙虚拟内联口需要配置地址才会生成路由,可以是根墙和虚墙可以同子网地址也可以是不同子网地址。 ip address 1.1.1.1 255.255.255.0 # interface Virtual-if1 ip address 1.1.1.2 255.255.255.0 # interface Virtual-if2 ip address 1.1.3.1 255.255.255.0 # interface NULL0 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface Virtual-if0 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0.255 # firewall zone dmz set priority 50 # api # ip route-static 0.0.0.0 0.0.0.0 10.0.255.254 ip route-static 100.1.0.0 255.255.255.0 vpn-instance A //配置虚墙A的回程路由 ip route-static 100.2.0.0 255.255.255.0 vpn-instance B //配置虚墙B的回程路由 # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust source-address 100.1.0.0 mask 255.255.255.0 source-address 100.2.0.0 mask 255.255.255.0 action permit #############################################虚墙A的配置################################################## switch vsys A # interface GigabitEthernet1/0/0.100 vlan-type dot1q 100 ip binding vpn-instance A ip address 10.0.100.1 255.255.255.0 service-manage ping permit # interface Virtual-if1 ip address 1.1.1.2 255.255.255.0 # sa # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/0.100 # firewall zone untrust set priority 5 add interface Virtual-if1 # firewall zone dmz set priority 50 # location # nat address-group SNAT 1 mode pat route enable section 0 100.1.0.100 100.1.0.100 # multi-linkif mode proportion-of-weight # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action permit rule name Local_Trust_Permit source-zone local destination-zone trust action permit # nat-policy //将租户VPC内地址转换为公网地址SNAT方式 rule name Trust_Untrust_SNAT source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action source-nat address-group SNAT # ip route-static 0.0.0.0 0.0.0.0 public //配置去往根墙的路由 ip route-static 192.168.10.0 255.255.255.0 10.0.100.254 //回程路由 # return # #############################################虚墙B的配置################################################## switch vsys B # interface GigabitEthernet1/0/0.200 vlan-type dot1q 200 ip binding vpn-instance B ip address 10.0.200.1 255.255.255.0 service-manage ping permit # interface Virtual-if2 ip address 1.1.3.1 255.255.255.0 # sa # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/0.200 # firewall zone untrust set priority 5 add interface Virtual-if2 # firewall zone dmz set priority 50 # location # nat address-group SNAT 0 mode pat route enable section 0 100.2.0.100 100.2.0.100 # multi-linkif mode proportion-of-weight # security-policy rule name Trust_Untrust_Permit source-zone trust destination-zone untrust source-address 192.168.20.0 mask 255.255.255.0 action permit rule name Local_Trust_Permit source-zone local destination-zone trust action permit # auth-policy # traffic-policy # policy-based-route # nat-policy //将租户VPC内地址转换为公网地址SNAT方式 rule name Trust_Untrust_SNAT source-zone trust destination-zone untrust source-address 192.168.20.0 mask 255.255.255.0 action source-nat address-group SNAT # proxy-policy # pcp-policy # ip route-static 0.0.0.0 0.0.0.0 public //配置去往根墙的路由 ip route-static 192.168.20.0 255.255.255.0 10.0.200.254 //回程路由 # return
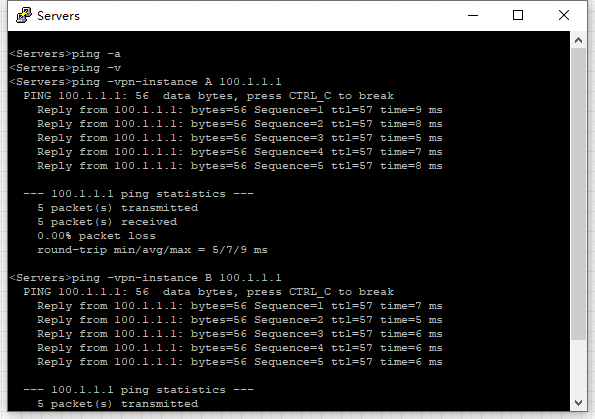
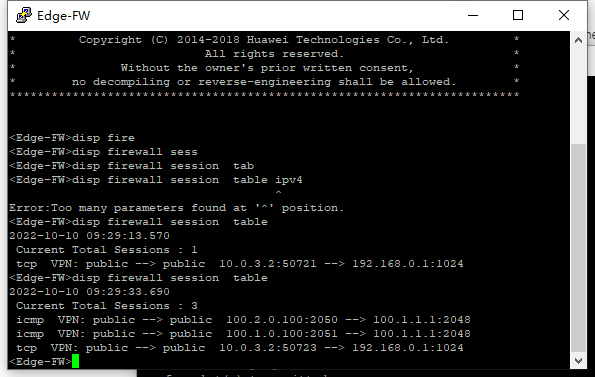
实验结果:
配置要点:主要的要点是在租户防火墙和Service-Leaf,一个是Service-Leaf需要引导租户流量进入防火墙的配置,另外一个就是租户防火墙内虚墙和根墙的流量处理,这里比较简单。另外一个就是模拟器虚墙有BUG,虚墙接口不主动相应ARP,需要先通过虚墙ping一下对应的vxlan网关才可以正常通讯。