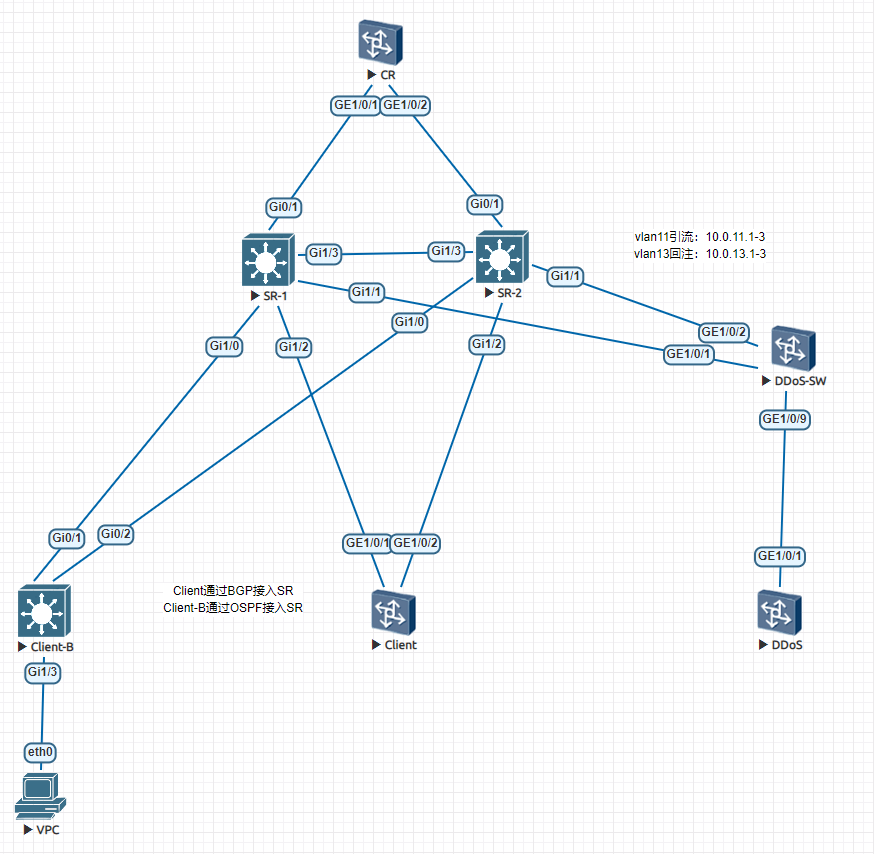
实验场景:使用两台交换机模拟SR业务路由器,两台SR单机部署,横穿有iBGP邻居关系,SR与Client对接采用BGP,SR与Client-B采用OSPF对接。 CR通过BGP下发默认路由,SR通过OSPF下发默认路由。使用交换机模拟DDoS清洗设备,检测假定采用分光器方式检测。
Client上通过Loopback接口地址模拟业务地址100.1.1.1
VPC上模拟Client-B的业务地址100.2.2.1
流量路径:当发生攻击后,流量经过SR通过BGP引流至DDOS清洗,清洗完毕后回注SR,然后通过PBR的方式将流量转发至下联对应的Client设备。
本次实验的主要配置是SR设备,SR配置如下:
CR-1#show running-config
Building configuration...
!
hostname CR-1
!
interface Loopback0 //用于SR之间iBGP邻居建立
ip address 1.1.1.1 255.255.255.255
!
interface GigabitEthernet0/0
negotiation auto
!
interface GigabitEthernet0/1 //与CR对接使用
no switchport
ip address 100.1.12.2 255.255.255.252
negotiation auto
!
interface GigabitEthernet0/2
negotiation auto
!
interface GigabitEthernet0/3
negotiation auto
!
interface GigabitEthernet1/0 //与Client-B互联使用
no switchport
ip address 10.0.22.1 255.255.255.252
negotiation auto
ospfv3 network point-to-point
!
interface GigabitEthernet1/1
no switchport
no ip address
negotiation auto
!
interface GigabitEthernet1/1.11 //与DDoS互联进行引流使用
encapsulation dot1Q 11
ip address 10.0.11.1 255.255.255.240
!
interface GigabitEthernet1/1.13 //与DDoS互联进行流量回注使用
encapsulation dot1Q 13
ip address 10.0.13.1 255.255.255.240
ip policy route-map DDoS_HuiZhu_A //配置PBR,将收到的回注流量转发到下联设备
!
interface GigabitEthernet1/2 //与Client互联使用
no switchport
ip address 10.0.21.1 255.255.255.252
negotiation auto
!
interface GigabitEthernet1/3 //SR之间互联使用
no switchport
ip address 10.0.12.1 255.255.255.252
negotiation auto
!
router ospf 1
network 1.1.1.1 0.0.0.0 area 0
network 10.0.12.0 0.0.0.3 area 0
network 10.0.22.0 0.0.0.3 area 0
default-information originate always //主要用于Client-B的引流,由于Client-B是OSPF接入
!
router bgp 100
bgp log-neighbor-changes
neighbor 1.1.1.2 remote-as 100
neighbor 1.1.1.2 update-source Loopback0
neighbor 10.0.11.3 remote-as 100
neighbor 10.0.21.2 remote-as 65000
neighbor 100.1.12.1 remote-as 101
!
address-family ipv4
network 100.2.2.0 mask 255.255.255.0
neighbor 1.1.1.2 activate
neighbor 1.1.1.2 next-hop-self
neighbor 10.0.11.3 activate
neighbor 10.0.11.3 route-map DDoS_YinLiu_Import in //给DDoS做in方向团体字设置
neighbor 10.0.11.3 route-map DDoS_Deny_All out //拒绝给DDoS通告任何路由
neighbor 10.0.21.2 activate
neighbor 100.1.12.1 activate
exit-address-family
!
access-list 2010 permit ip any host 100.1.1.1 //Client的路由命中
access-list 2011 permit ip any host 100.2.2.1 //Client-B的路由命中
!
route-map DDoS_YinLiu_Import permit 10
set community no-export //给DDoS侧收到的路由设置团体属性no-export,禁止该路由转发到AS外
!
route-map DDoS_Deny_All deny 1000 //拒绝通告所有路由给DDoS
!
route-map DDoS_HuiZhu_A permit 10 //设置Client的PBR
match ip address 2010
set ip next-hop 10.0.21.2
!
route-map DDoS_HuiZhu_A permit 20 //设置Client-B的PBR
match ip address 2011
set ip next-hop 10.0.22.2
!
end
CR-1#show running-config
Building configuration...
!
hostname CR-1
!
interface Loopback0 //用于SR之间iBGP邻居建立
ip address 1.1.1.1 255.255.255.255
!
interface GigabitEthernet0/0
negotiation auto
!
interface GigabitEthernet0/1 //与CR对接使用
no switchport
ip address 100.1.12.2 255.255.255.252
negotiation auto
!
interface GigabitEthernet0/2
negotiation auto
!
interface GigabitEthernet0/3
negotiation auto
!
interface GigabitEthernet1/0 //与Client-B互联使用
no switchport
ip address 10.0.22.1 255.255.255.252
negotiation auto
ospfv3 network point-to-point
!
interface GigabitEthernet1/1
no switchport
no ip address
negotiation auto
!
interface GigabitEthernet1/1.11 //与DDoS互联进行引流使用
encapsulation dot1Q 11
ip address 10.0.11.1 255.255.255.240
!
interface GigabitEthernet1/1.13 //与DDoS互联进行流量回注使用
encapsulation dot1Q 13
ip address 10.0.13.1 255.255.255.240
ip policy route-map DDoS_HuiZhu_A //配置PBR,将收到的回注流量转发到下联设备
!
interface GigabitEthernet1/2 //与Client互联使用
no switchport
ip address 10.0.21.1 255.255.255.252
negotiation auto
!
interface GigabitEthernet1/3 //SR之间互联使用
no switchport
ip address 10.0.12.1 255.255.255.252
negotiation auto
!
router ospf 1
network 1.1.1.1 0.0.0.0 area 0
network 10.0.12.0 0.0.0.3 area 0
network 10.0.22.0 0.0.0.3 area 0
default-information originate always //主要用于Client-B的引流,由于Client-B是OSPF接入
!
router bgp 100
bgp log-neighbor-changes
neighbor 1.1.1.2 remote-as 100
neighbor 1.1.1.2 update-source Loopback0
neighbor 10.0.11.3 remote-as 100
neighbor 10.0.21.2 remote-as 65000
neighbor 100.1.12.1 remote-as 101
!
address-family ipv4
network 100.2.2.0 mask 255.255.255.0
neighbor 1.1.1.2 activate
neighbor 1.1.1.2 next-hop-self
neighbor 10.0.11.3 activate
neighbor 10.0.11.3 route-map DDoS_YinLiu_Import in //给DDoS做in方向团体字设置
neighbor 10.0.11.3 route-map DDoS_Deny_All out //拒绝给DDoS通告任何路由
neighbor 10.0.21.2 activate
neighbor 100.1.12.1 activate
exit-address-family
!
access-list 2010 permit ip any host 100.1.1.1 //Client的路由命中
access-list 2011 permit ip any host 100.2.2.1 //Client-B的路由命中
!
route-map DDoS_YinLiu_Import permit 10
set community no-export //给DDoS侧收到的路由设置团体属性no-export,禁止该路由转发到AS外
!
route-map DDoS_Deny_All deny 1000 //拒绝通告所有路由给DDoS
!
route-map DDoS_HuiZhu_A permit 10 //设置Client的PBR
match ip address 2010
set ip next-hop 10.0.21.2
!
route-map DDoS_HuiZhu_A permit 20 //设置Client-B的PBR
match ip address 2011
set ip next-hop 10.0.22.2
!
end
CR-1#show running-config Building configuration... ! hostname CR-1 ! interface Loopback0 //用于SR之间iBGP邻居建立 ip address 1.1.1.1 255.255.255.255 ! interface GigabitEthernet0/0 negotiation auto ! interface GigabitEthernet0/1 //与CR对接使用 no switchport ip address 100.1.12.2 255.255.255.252 negotiation auto ! interface GigabitEthernet0/2 negotiation auto ! interface GigabitEthernet0/3 negotiation auto ! interface GigabitEthernet1/0 //与Client-B互联使用 no switchport ip address 10.0.22.1 255.255.255.252 negotiation auto ospfv3 network point-to-point ! interface GigabitEthernet1/1 no switchport no ip address negotiation auto ! interface GigabitEthernet1/1.11 //与DDoS互联进行引流使用 encapsulation dot1Q 11 ip address 10.0.11.1 255.255.255.240 ! interface GigabitEthernet1/1.13 //与DDoS互联进行流量回注使用 encapsulation dot1Q 13 ip address 10.0.13.1 255.255.255.240 ip policy route-map DDoS_HuiZhu_A //配置PBR,将收到的回注流量转发到下联设备 ! interface GigabitEthernet1/2 //与Client互联使用 no switchport ip address 10.0.21.1 255.255.255.252 negotiation auto ! interface GigabitEthernet1/3 //SR之间互联使用 no switchport ip address 10.0.12.1 255.255.255.252 negotiation auto ! router ospf 1 network 1.1.1.1 0.0.0.0 area 0 network 10.0.12.0 0.0.0.3 area 0 network 10.0.22.0 0.0.0.3 area 0 default-information originate always //主要用于Client-B的引流,由于Client-B是OSPF接入 ! router bgp 100 bgp log-neighbor-changes neighbor 1.1.1.2 remote-as 100 neighbor 1.1.1.2 update-source Loopback0 neighbor 10.0.11.3 remote-as 100 neighbor 10.0.21.2 remote-as 65000 neighbor 100.1.12.1 remote-as 101 ! address-family ipv4 network 100.2.2.0 mask 255.255.255.0 neighbor 1.1.1.2 activate neighbor 1.1.1.2 next-hop-self neighbor 10.0.11.3 activate neighbor 10.0.11.3 route-map DDoS_YinLiu_Import in //给DDoS做in方向团体字设置 neighbor 10.0.11.3 route-map DDoS_Deny_All out //拒绝给DDoS通告任何路由 neighbor 10.0.21.2 activate neighbor 100.1.12.1 activate exit-address-family ! access-list 2010 permit ip any host 100.1.1.1 //Client的路由命中 access-list 2011 permit ip any host 100.2.2.1 //Client-B的路由命中 ! route-map DDoS_YinLiu_Import permit 10 set community no-export //给DDoS侧收到的路由设置团体属性no-export,禁止该路由转发到AS外 ! route-map DDoS_Deny_All deny 1000 //拒绝通告所有路由给DDoS ! route-map DDoS_HuiZhu_A permit 10 //设置Client的PBR match ip address 2010 set ip next-hop 10.0.21.2 ! route-map DDoS_HuiZhu_A permit 20 //设置Client-B的PBR match ip address 2011 set ip next-hop 10.0.22.2 ! end
实验结果:
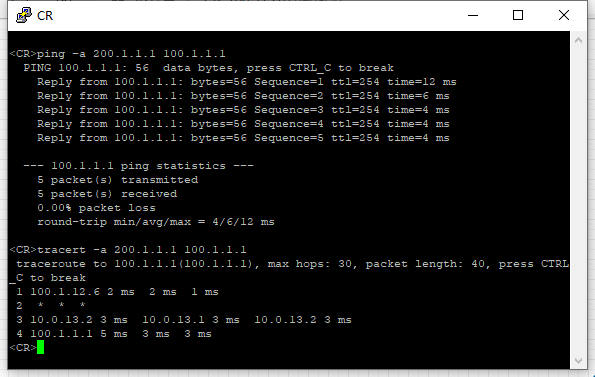
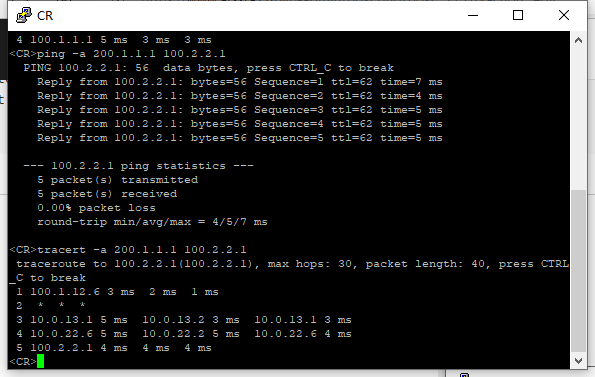
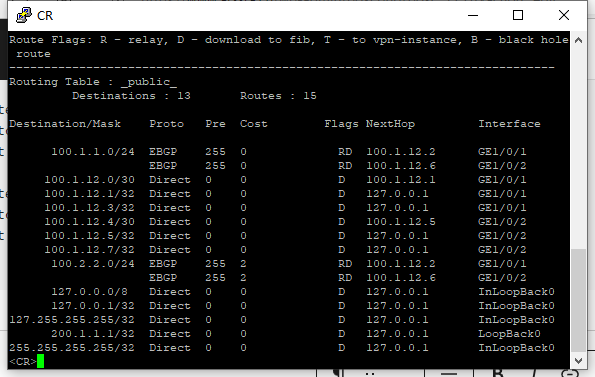
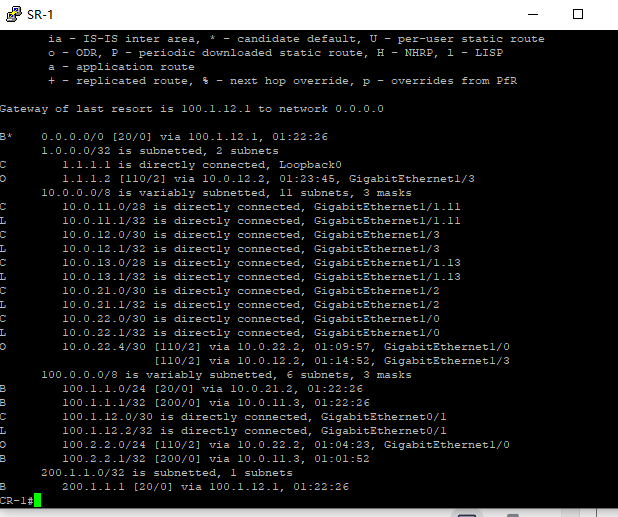
从CR访问Client的100.1.1.1和100.2.2.1,并查看CR和SR的路由表。
总结:配置比较简单,大部分配置都集中在SR上了,SR上的主要配置就是BGP的路由策略了,主要是给DDOS引流方向收到的路由打上no-export的团体属性,如果中间的SR是1台设备或者交换机堆叠设备,且没有横穿iBGP邻居关系作为逃生链路的话,可以考虑配置no-advertise团体属性。
能把全篇配置发给我参考下吗?邮件地址244405079@qq.com
感谢
没存,这种实验我一般都只会贴出来关键配置