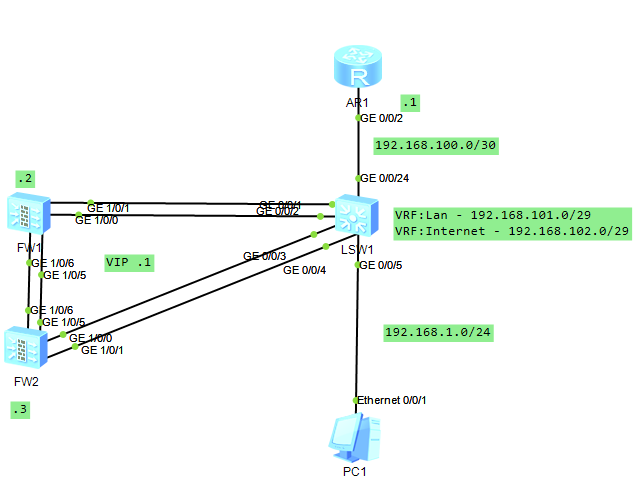
拓扑说明:FW1作为主墙、FW2作为备墙,进行双机热备,旁挂形式组网,PC访问路由器AR1的时候需要流量经过防火墙,并且在防火墙上做SNAT,PC地址对于路由器不可见。
CSW配置:
#
sysname CSW
#
vlan batch 100 to 102
#
dhcp enable
#
ip vpn-instance Internet
ipv4-family
route-distinguisher 100:1
#
ip vpn-instance Lan
ipv4-family
route-distinguisher 100:2
#
interface Vlanif1
ip binding vpn-instance Lan
ip address 192.168.1.254 255.255.255.0
dhcp select interface
#
interface Vlanif100
ip binding vpn-instance Internet
ip address 192.168.100.2 255.255.255.252
#
interface Vlanif101
ip binding vpn-instance Lan
ip address 192.168.101.6 255.255.255.248
#
interface Vlanif102
ip binding vpn-instance Internet
ip address 192.168.102.6 255.255.255.248
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 101 to 102
mode lacp-static
#
interface Eth-Trunk2
port link-type trunk
port trunk allow-pass vlan 101 to 102
mode lacp-static
#
interface GigabitEthernet0/0/1
eth-trunk 1
#
interface GigabitEthernet0/0/2
eth-trunk 1
#
interface GigabitEthernet0/0/3
eth-trunk 2
#
interface GigabitEthernet0/0/4
eth-trunk 2
#
interface GigabitEthernet0/0/5
port link-type access
#
interface GigabitEthernet0/0/24
port link-type access
port default vlan 100
#
ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 192.168.100.1
ip route-static vpn-instance Lan 0.0.0.0 0.0.0.0 192.168.101.1
#
sysname CSW
#
vlan batch 100 to 102
#
dhcp enable
#
ip vpn-instance Internet
ipv4-family
route-distinguisher 100:1
#
ip vpn-instance Lan
ipv4-family
route-distinguisher 100:2
#
interface Vlanif1
ip binding vpn-instance Lan
ip address 192.168.1.254 255.255.255.0
dhcp select interface
#
interface Vlanif100
ip binding vpn-instance Internet
ip address 192.168.100.2 255.255.255.252
#
interface Vlanif101
ip binding vpn-instance Lan
ip address 192.168.101.6 255.255.255.248
#
interface Vlanif102
ip binding vpn-instance Internet
ip address 192.168.102.6 255.255.255.248
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 101 to 102
mode lacp-static
#
interface Eth-Trunk2
port link-type trunk
port trunk allow-pass vlan 101 to 102
mode lacp-static
#
interface GigabitEthernet0/0/1
eth-trunk 1
#
interface GigabitEthernet0/0/2
eth-trunk 1
#
interface GigabitEthernet0/0/3
eth-trunk 2
#
interface GigabitEthernet0/0/4
eth-trunk 2
#
interface GigabitEthernet0/0/5
port link-type access
#
interface GigabitEthernet0/0/24
port link-type access
port default vlan 100
#
ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 192.168.100.1
ip route-static vpn-instance Lan 0.0.0.0 0.0.0.0 192.168.101.1
# sysname CSW # vlan batch 100 to 102 # dhcp enable # ip vpn-instance Internet ipv4-family route-distinguisher 100:1 # ip vpn-instance Lan ipv4-family route-distinguisher 100:2 # interface Vlanif1 ip binding vpn-instance Lan ip address 192.168.1.254 255.255.255.0 dhcp select interface # interface Vlanif100 ip binding vpn-instance Internet ip address 192.168.100.2 255.255.255.252 # interface Vlanif101 ip binding vpn-instance Lan ip address 192.168.101.6 255.255.255.248 # interface Vlanif102 ip binding vpn-instance Internet ip address 192.168.102.6 255.255.255.248 # interface Eth-Trunk1 port link-type trunk port trunk allow-pass vlan 101 to 102 mode lacp-static # interface Eth-Trunk2 port link-type trunk port trunk allow-pass vlan 101 to 102 mode lacp-static # interface GigabitEthernet0/0/1 eth-trunk 1 # interface GigabitEthernet0/0/2 eth-trunk 1 # interface GigabitEthernet0/0/3 eth-trunk 2 # interface GigabitEthernet0/0/4 eth-trunk 2 # interface GigabitEthernet0/0/5 port link-type access # interface GigabitEthernet0/0/24 port link-type access port default vlan 100 # ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 192.168.100.1 ip route-static vpn-instance Lan 0.0.0.0 0.0.0.0 192.168.101.1
FW-1主墙配置:
#
sysname FW-1
#
hrp enable
hrp interface Eth-Trunk63 remote 1.1.1.2
hrp mirror session enable
hrp standby config enable
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
#
interface Eth-Trunk1
mode lacp-static
#
interface Eth-Trunk1.101
vlan-type dot1q 101
ip address 192.168.101.2 255.255.255.248
vrrp vrid 1 virtual-ip 192.168.101.1 active
service-manage ping permit
#
interface Eth-Trunk1.102
vlan-type dot1q 102
ip address 192.168.102.2 255.255.255.248
vrrp vrid 2 virtual-ip 192.168.102.1 active
service-manage ping permit
#
interface Eth-Trunk63
ip address 1.1.1.1 255.255.255.252
mode lacp-static
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/5
undo shutdown
eth-trunk 63
#
interface GigabitEthernet1/0/6
undo shutdown
eth-trunk 63
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface Eth-Trunk1.101
add interface Eth-Trunk63
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
add interface Eth-Trunk1.102
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 192.168.102.6
ip route-static 192.168.1.0 255.255.255.0 192.168.101.6
#
nat address-group PC 0
mode pat
section 0 192.168.102.5 192.168.102.5
#
security-policy
rule name Trust_To_Local
source-zone trust
destination-zone local
action permit
rule name Trust_To_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
#
nat-policy
rule name Turst_Untrust_Easy-ip
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action source-nat address-group PC
#
#
sysname FW-1
#
hrp enable
hrp interface Eth-Trunk63 remote 1.1.1.2
hrp mirror session enable
hrp standby config enable
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
#
interface Eth-Trunk1
mode lacp-static
#
interface Eth-Trunk1.101
vlan-type dot1q 101
ip address 192.168.101.2 255.255.255.248
vrrp vrid 1 virtual-ip 192.168.101.1 active
service-manage ping permit
#
interface Eth-Trunk1.102
vlan-type dot1q 102
ip address 192.168.102.2 255.255.255.248
vrrp vrid 2 virtual-ip 192.168.102.1 active
service-manage ping permit
#
interface Eth-Trunk63
ip address 1.1.1.1 255.255.255.252
mode lacp-static
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/5
undo shutdown
eth-trunk 63
#
interface GigabitEthernet1/0/6
undo shutdown
eth-trunk 63
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface Eth-Trunk1.101
add interface Eth-Trunk63
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
add interface Eth-Trunk1.102
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 192.168.102.6
ip route-static 192.168.1.0 255.255.255.0 192.168.101.6
#
nat address-group PC 0
mode pat
section 0 192.168.102.5 192.168.102.5
#
security-policy
rule name Trust_To_Local
source-zone trust
destination-zone local
action permit
rule name Trust_To_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
#
nat-policy
rule name Turst_Untrust_Easy-ip
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action source-nat address-group PC
#
# sysname FW-1 # hrp enable hrp interface Eth-Trunk63 remote 1.1.1.2 hrp mirror session enable hrp standby config enable hrp track interface GigabitEthernet1/0/0 hrp track interface GigabitEthernet1/0/1 # interface Eth-Trunk1 mode lacp-static # interface Eth-Trunk1.101 vlan-type dot1q 101 ip address 192.168.101.2 255.255.255.248 vrrp vrid 1 virtual-ip 192.168.101.1 active service-manage ping permit # interface Eth-Trunk1.102 vlan-type dot1q 102 ip address 192.168.102.2 255.255.255.248 vrrp vrid 2 virtual-ip 192.168.102.1 active service-manage ping permit # interface Eth-Trunk63 ip address 1.1.1.1 255.255.255.252 mode lacp-static # interface GigabitEthernet1/0/0 undo shutdown eth-trunk 1 # interface GigabitEthernet1/0/1 undo shutdown eth-trunk 1 # interface GigabitEthernet1/0/5 undo shutdown eth-trunk 63 # interface GigabitEthernet1/0/6 undo shutdown eth-trunk 63 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface Eth-Trunk1.101 add interface Eth-Trunk63 add interface GigabitEthernet0/0/0 # firewall zone untrust set priority 5 add interface Eth-Trunk1.102 # firewall zone dmz set priority 50 # ip route-static 0.0.0.0 0.0.0.0 192.168.102.6 ip route-static 192.168.1.0 255.255.255.0 192.168.101.6 # nat address-group PC 0 mode pat section 0 192.168.102.5 192.168.102.5 # security-policy rule name Trust_To_Local source-zone trust destination-zone local action permit rule name Trust_To_Untrust source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action permit # nat-policy rule name Turst_Untrust_Easy-ip source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action source-nat address-group PC #
FW-2备墙配置:
#
sysname FW-2
#
hrp enable
hrp standby-device
hrp interface Eth-Trunk63 remote 1.1.1.1
hrp mirror session enable
hrp standby config enable
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
#
interface Eth-Trunk1
mode lacp-static
#
interface Eth-Trunk1.101
vlan-type dot1q 101
ip address 192.168.101.3 255.255.255.248
vrrp vrid 1 virtual-ip 192.168.101.1 standby
service-manage ping permit
#
interface Eth-Trunk1.102
vlan-type dot1q 102
ip address 192.168.102.3 255.255.255.248
vrrp vrid 2 virtual-ip 192.168.102.1 standby
service-manage ping permit
#
interface Eth-Trunk63
ip address 1.1.1.2 255.255.255.252
mode lacp-static
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/5
undo shutdown
eth-trunk 63
#
interface GigabitEthernet1/0/6
undo shutdown
eth-trunk 63
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface Eth-Trunk1.101
add interface Eth-Trunk63
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
add interface Eth-Trunk1.102
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 192.168.102.6
ip route-static 192.168.1.0 255.255.255.0 192.168.101.6
#
nat address-group PC 0
mode pat
section 0 192.168.102.5 192.168.102.5
#
security-policy
rule name Trust_To_Local
source-zone trust
destination-zone local
action permit
rule name Trust_To_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
#
nat-policy
rule name Turst_Untrust_Easy-ip
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action source-nat address-group PC
#
#
sysname FW-2
#
hrp enable
hrp standby-device
hrp interface Eth-Trunk63 remote 1.1.1.1
hrp mirror session enable
hrp standby config enable
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
#
interface Eth-Trunk1
mode lacp-static
#
interface Eth-Trunk1.101
vlan-type dot1q 101
ip address 192.168.101.3 255.255.255.248
vrrp vrid 1 virtual-ip 192.168.101.1 standby
service-manage ping permit
#
interface Eth-Trunk1.102
vlan-type dot1q 102
ip address 192.168.102.3 255.255.255.248
vrrp vrid 2 virtual-ip 192.168.102.1 standby
service-manage ping permit
#
interface Eth-Trunk63
ip address 1.1.1.2 255.255.255.252
mode lacp-static
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/5
undo shutdown
eth-trunk 63
#
interface GigabitEthernet1/0/6
undo shutdown
eth-trunk 63
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface Eth-Trunk1.101
add interface Eth-Trunk63
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
add interface Eth-Trunk1.102
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 192.168.102.6
ip route-static 192.168.1.0 255.255.255.0 192.168.101.6
#
nat address-group PC 0
mode pat
section 0 192.168.102.5 192.168.102.5
#
security-policy
rule name Trust_To_Local
source-zone trust
destination-zone local
action permit
rule name Trust_To_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
#
nat-policy
rule name Turst_Untrust_Easy-ip
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action source-nat address-group PC
#
# sysname FW-2 # hrp enable hrp standby-device hrp interface Eth-Trunk63 remote 1.1.1.1 hrp mirror session enable hrp standby config enable hrp track interface GigabitEthernet1/0/0 hrp track interface GigabitEthernet1/0/1 # interface Eth-Trunk1 mode lacp-static # interface Eth-Trunk1.101 vlan-type dot1q 101 ip address 192.168.101.3 255.255.255.248 vrrp vrid 1 virtual-ip 192.168.101.1 standby service-manage ping permit # interface Eth-Trunk1.102 vlan-type dot1q 102 ip address 192.168.102.3 255.255.255.248 vrrp vrid 2 virtual-ip 192.168.102.1 standby service-manage ping permit # interface Eth-Trunk63 ip address 1.1.1.2 255.255.255.252 mode lacp-static # interface GigabitEthernet1/0/0 undo shutdown eth-trunk 1 # interface GigabitEthernet1/0/1 undo shutdown eth-trunk 1 # interface GigabitEthernet1/0/5 undo shutdown eth-trunk 63 # interface GigabitEthernet1/0/6 undo shutdown eth-trunk 63 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface Eth-Trunk1.101 add interface Eth-Trunk63 add interface GigabitEthernet0/0/0 # firewall zone untrust set priority 5 add interface Eth-Trunk1.102 # firewall zone dmz set priority 50 # ip route-static 0.0.0.0 0.0.0.0 192.168.102.6 ip route-static 192.168.1.0 255.255.255.0 192.168.101.6 # nat address-group PC 0 mode pat section 0 192.168.102.5 192.168.102.5 # security-policy rule name Trust_To_Local source-zone trust destination-zone local action permit rule name Trust_To_Untrust source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action permit # nat-policy rule name Turst_Untrust_Easy-ip source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action source-nat address-group PC #
结果:
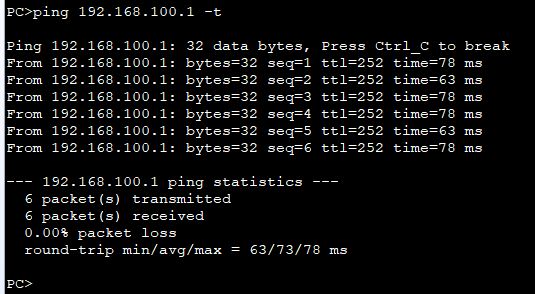
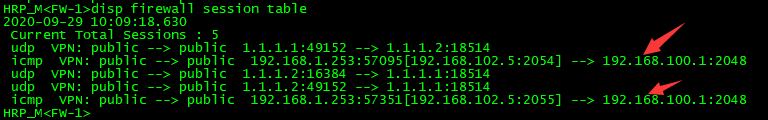
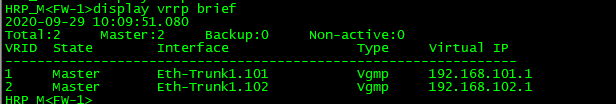
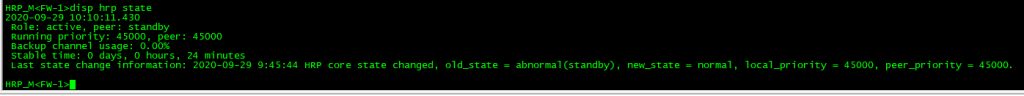
知识点:由于华为不能设置hrp track的优先级,当track接口down后,优先级会-2,然后会进行主备切换,当track接口为Eth-trunk接口的时候,可以设置Eth-trunk的成员的下限阈值来控制最小的端口活动数,如果不满足则down掉eth-trunk接口,如:least active-linknumber 2,就是当成员端口数量大于等于2的时候接口状态为UP,否者为DOWN。