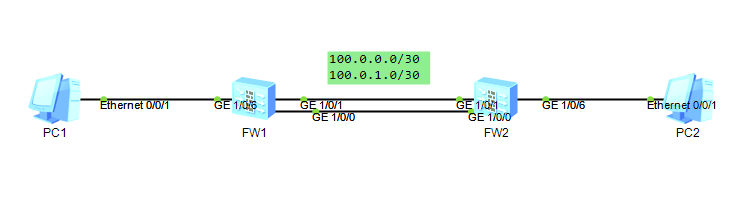
场景说明:FW1作为总部防火墙,与FW2连接的时候采用两条链路进行连接,流量进行负载分担的方式传输,并且对数据进行加密。其中总部的防火墙采用反向路由注入的方式来获取分布的业务地址。
FW1配置:
#
sysname FW-1
#
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec proposal A
encapsulation-mode auto //IPSEC封装模式为自适应,作为发起端以隧道模式封装,作为接收端可以进行隧道或传输模式封装
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal B
encapsulation-mode auto //IPSEC封装模式为自适应,作为发起端以隧道模式封装,作为接收端可以进行隧道或传输模式封装
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
exchange-mode auto //配置IKEv1的阶段一的协商模式,作为发起端采用主模式,作为接收端可以接受主模式和野蛮模式
pre-shared-key %^%#Gfdo+G{9oWT'nG7.="IFmq)7-OWtZ"q5w41)cMM<%^%#
ike-proposal 1
ike peer B
exchange-mode auto //配置IKEv1的阶段一的协商模式,作为发起端采用主模式,作为接收端可以接受主模式和野蛮模式
pre-shared-key %^%#0Cy&~ky%:YEJy\Sk""VJStMYXfL-j-r_,&MwEma)%^%#
ike-proposal 2
#
ipsec policy-template IPSEC_TMP-1 1
security acl 3000
ike-peer A
proposal A
route inject dynamic //反向动态路由注入方式,主要为了如果分支业务网络较多的情况下,采用配置的方式容易出错,为了减少配置量和提高正确性,因此采用反向路由注入,当IPSEC隧道UP后路由会被作为UNR类型注入到路由表中,当隧道DOWN后会撤销相应隧道的路由
ipsec policy-template IPSEC_TMP-2 1
security acl 3000
ike-peer B
proposal B
route inject dynamic
#
ipsec policy POLICY-1 1 isakmp template IPSEC_TMP-1
ipsec policy POLICY-2 1 isakmp template IPSEC_TMP-2
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.252
service-manage ping permit
ipsec policy POLICY-1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.1.1 255.255.255.252
service-manage ping permit
ipsec policy POLICY-2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.10.254 255.255.255.0
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
security-policy
rule name Untrust_Local
source-zone untrust
destination-zone local
source-address 100.0.0.2 mask 255.255.255.255
source-address 100.0.1.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.1.1 mask 255.255.255.255
action permit
rule name Local_Untrust
source-zone local
destination-zone untrust
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.1.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.1.2 mask 255.255.255.255
action permit
rule name Untrust_Trust
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Trust_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
#
retur
#
sysname FW-1
#
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec proposal A
encapsulation-mode auto //IPSEC封装模式为自适应,作为发起端以隧道模式封装,作为接收端可以进行隧道或传输模式封装
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal B
encapsulation-mode auto //IPSEC封装模式为自适应,作为发起端以隧道模式封装,作为接收端可以进行隧道或传输模式封装
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
exchange-mode auto //配置IKEv1的阶段一的协商模式,作为发起端采用主模式,作为接收端可以接受主模式和野蛮模式
pre-shared-key %^%#Gfdo+G{9oWT'nG7.="IFmq)7-OWtZ"q5w41)cMM<%^%#
ike-proposal 1
ike peer B
exchange-mode auto //配置IKEv1的阶段一的协商模式,作为发起端采用主模式,作为接收端可以接受主模式和野蛮模式
pre-shared-key %^%#0Cy&~ky%:YEJy\Sk""VJStMYXfL-j-r_,&MwEma)%^%#
ike-proposal 2
#
ipsec policy-template IPSEC_TMP-1 1
security acl 3000
ike-peer A
proposal A
route inject dynamic //反向动态路由注入方式,主要为了如果分支业务网络较多的情况下,采用配置的方式容易出错,为了减少配置量和提高正确性,因此采用反向路由注入,当IPSEC隧道UP后路由会被作为UNR类型注入到路由表中,当隧道DOWN后会撤销相应隧道的路由
ipsec policy-template IPSEC_TMP-2 1
security acl 3000
ike-peer B
proposal B
route inject dynamic
#
ipsec policy POLICY-1 1 isakmp template IPSEC_TMP-1
ipsec policy POLICY-2 1 isakmp template IPSEC_TMP-2
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.252
service-manage ping permit
ipsec policy POLICY-1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.1.1 255.255.255.252
service-manage ping permit
ipsec policy POLICY-2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.10.254 255.255.255.0
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
security-policy
rule name Untrust_Local
source-zone untrust
destination-zone local
source-address 100.0.0.2 mask 255.255.255.255
source-address 100.0.1.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.1.1 mask 255.255.255.255
action permit
rule name Local_Untrust
source-zone local
destination-zone untrust
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.1.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.1.2 mask 255.255.255.255
action permit
rule name Untrust_Trust
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Trust_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
#
retur
#
sysname FW-1
#
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec proposal A
encapsulation-mode auto //IPSEC封装模式为自适应,作为发起端以隧道模式封装,作为接收端可以进行隧道或传输模式封装
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal B
encapsulation-mode auto //IPSEC封装模式为自适应,作为发起端以隧道模式封装,作为接收端可以进行隧道或传输模式封装
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
exchange-mode auto //配置IKEv1的阶段一的协商模式,作为发起端采用主模式,作为接收端可以接受主模式和野蛮模式
pre-shared-key %^%#Gfdo+G{9oWT'nG7.="IFmq)7-OWtZ"q5w41)cMM<%^%#
ike-proposal 1
ike peer B
exchange-mode auto //配置IKEv1的阶段一的协商模式,作为发起端采用主模式,作为接收端可以接受主模式和野蛮模式
pre-shared-key %^%#0Cy&~ky%:YEJy\Sk""VJStMYXfL-j-r_,&MwEma)%^%#
ike-proposal 2
#
ipsec policy-template IPSEC_TMP-1 1
security acl 3000
ike-peer A
proposal A
route inject dynamic //反向动态路由注入方式,主要为了如果分支业务网络较多的情况下,采用配置的方式容易出错,为了减少配置量和提高正确性,因此采用反向路由注入,当IPSEC隧道UP后路由会被作为UNR类型注入到路由表中,当隧道DOWN后会撤销相应隧道的路由
ipsec policy-template IPSEC_TMP-2 1
security acl 3000
ike-peer B
proposal B
route inject dynamic
#
ipsec policy POLICY-1 1 isakmp template IPSEC_TMP-1
ipsec policy POLICY-2 1 isakmp template IPSEC_TMP-2
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.252
service-manage ping permit
ipsec policy POLICY-1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.1.1 255.255.255.252
service-manage ping permit
ipsec policy POLICY-2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.10.254 255.255.255.0
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
security-policy
rule name Untrust_Local
source-zone untrust
destination-zone local
source-address 100.0.0.2 mask 255.255.255.255
source-address 100.0.1.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.1.1 mask 255.255.255.255
action permit
rule name Local_Untrust
source-zone local
destination-zone untrust
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.1.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.1.2 mask 255.255.255.255
action permit
rule name Untrust_Trust
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Trust_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
#
retur
FW2配置:
#
sysname FW-2
#
acl number 3000
rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
#
ipsec proposal A
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal B
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
exchange-mode auto
pre-shared-key %^%#'CXE,8UAy57o1!>hi-|BvYQ7FQNF2,vD;%#uP>38%^%#
ike-proposal 1
remote-address 100.0.0.1
ike peer B
exchange-mode auto
pre-shared-key %^%#y|x"Yk!i*&`5{EQ:]1-O!'j}G/q9Z!}A)\QSk02/%^%#
ike-proposal 2
remote-address 100.0.1.1
#
ipsec policy POLICY-1 1 isakmp
security acl 3000
ike-peer A
proposal A
tunnel local applied-interface //这里可以直接指定隧道local地址,也可以采用该策略配置到哪个接口就采用哪个接口的地址作为隧道的主地址
sa trigger-mode auto //IPSEC隧道的触发方式为自动触发,无需数据来进行触发隧道建立
ipsec policy POLICY-2 1 isakmp
security acl 3000
ike-peer B
proposal B
tunnel local applied-interface
sa trigger-mode auto
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
ipsec policy POLICY-1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.1.2 255.255.255.252
service-manage ping permit
ipsec policy POLICY-2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.20.254 255.255.255.0
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
ip route-static 192.168.10.0 255.255.255.0 100.0.0.1
ip route-static 192.168.10.0 255.255.255.0 100.0.1.1
#
security-policy
rule name Local_Untrust
source-zone local
destination-zone untrust
source-address 100.0.0.2 mask 255.255.255.255
source-address 100.0.1.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.1.1 mask 255.255.255.255
action permit
rule name Untrust_Local
source-zone untrust
destination-zone local
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.1.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.1.2 mask 255.255.255.255
action permit
rule name Untrust_Trust
source-zone untrust
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Trust_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
#
sysname FW-2
#
acl number 3000
rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
#
ipsec proposal A
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal B
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
exchange-mode auto
pre-shared-key %^%#'CXE,8UAy57o1!>hi-|BvYQ7FQNF2,vD;%#uP>38%^%#
ike-proposal 1
remote-address 100.0.0.1
ike peer B
exchange-mode auto
pre-shared-key %^%#y|x"Yk!i*&`5{EQ:]1-O!'j}G/q9Z!}A)\QSk02/%^%#
ike-proposal 2
remote-address 100.0.1.1
#
ipsec policy POLICY-1 1 isakmp
security acl 3000
ike-peer A
proposal A
tunnel local applied-interface //这里可以直接指定隧道local地址,也可以采用该策略配置到哪个接口就采用哪个接口的地址作为隧道的主地址
sa trigger-mode auto //IPSEC隧道的触发方式为自动触发,无需数据来进行触发隧道建立
ipsec policy POLICY-2 1 isakmp
security acl 3000
ike-peer B
proposal B
tunnel local applied-interface
sa trigger-mode auto
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
ipsec policy POLICY-1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.1.2 255.255.255.252
service-manage ping permit
ipsec policy POLICY-2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.20.254 255.255.255.0
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
ip route-static 192.168.10.0 255.255.255.0 100.0.0.1
ip route-static 192.168.10.0 255.255.255.0 100.0.1.1
#
security-policy
rule name Local_Untrust
source-zone local
destination-zone untrust
source-address 100.0.0.2 mask 255.255.255.255
source-address 100.0.1.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.1.1 mask 255.255.255.255
action permit
rule name Untrust_Local
source-zone untrust
destination-zone local
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.1.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.1.2 mask 255.255.255.255
action permit
rule name Untrust_Trust
source-zone untrust
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Trust_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
#
sysname FW-2
#
acl number 3000
rule 5 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
#
ipsec proposal A
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec proposal B
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 2
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer A
exchange-mode auto
pre-shared-key %^%#'CXE,8UAy57o1!>hi-|BvYQ7FQNF2,vD;%#uP>38%^%#
ike-proposal 1
remote-address 100.0.0.1
ike peer B
exchange-mode auto
pre-shared-key %^%#y|x"Yk!i*&`5{EQ:]1-O!'j}G/q9Z!}A)\QSk02/%^%#
ike-proposal 2
remote-address 100.0.1.1
#
ipsec policy POLICY-1 1 isakmp
security acl 3000
ike-peer A
proposal A
tunnel local applied-interface //这里可以直接指定隧道local地址,也可以采用该策略配置到哪个接口就采用哪个接口的地址作为隧道的主地址
sa trigger-mode auto //IPSEC隧道的触发方式为自动触发,无需数据来进行触发隧道建立
ipsec policy POLICY-2 1 isakmp
security acl 3000
ike-peer B
proposal B
tunnel local applied-interface
sa trigger-mode auto
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
ipsec policy POLICY-1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 100.0.1.2 255.255.255.252
service-manage ping permit
ipsec policy POLICY-2
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.20.254 255.255.255.0
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
ip route-static 192.168.10.0 255.255.255.0 100.0.0.1
ip route-static 192.168.10.0 255.255.255.0 100.0.1.1
#
security-policy
rule name Local_Untrust
source-zone local
destination-zone untrust
source-address 100.0.0.2 mask 255.255.255.255
source-address 100.0.1.2 mask 255.255.255.255
destination-address 100.0.0.1 mask 255.255.255.255
destination-address 100.0.1.1 mask 255.255.255.255
action permit
rule name Untrust_Local
source-zone untrust
destination-zone local
source-address 100.0.0.1 mask 255.255.255.255
source-address 100.0.1.1 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
destination-address 100.0.1.2 mask 255.255.255.255
action permit
rule name Untrust_Trust
source-zone untrust
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
rule name Trust_Untrust
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
#
return
实验结果:
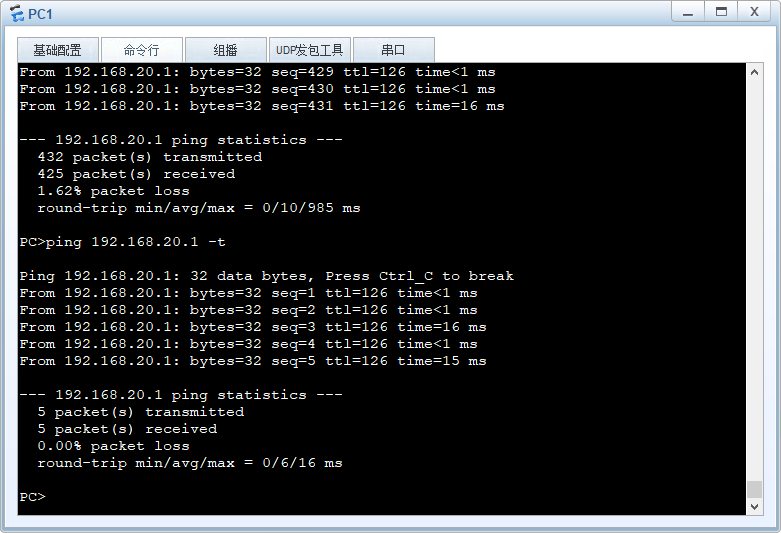
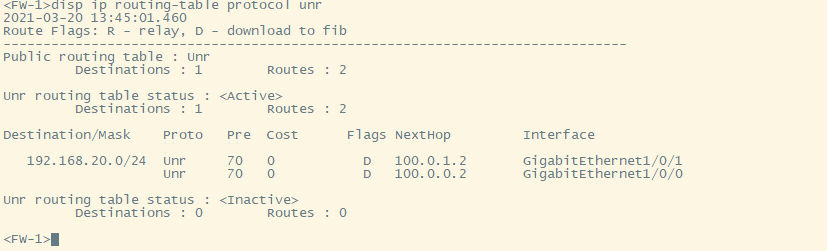
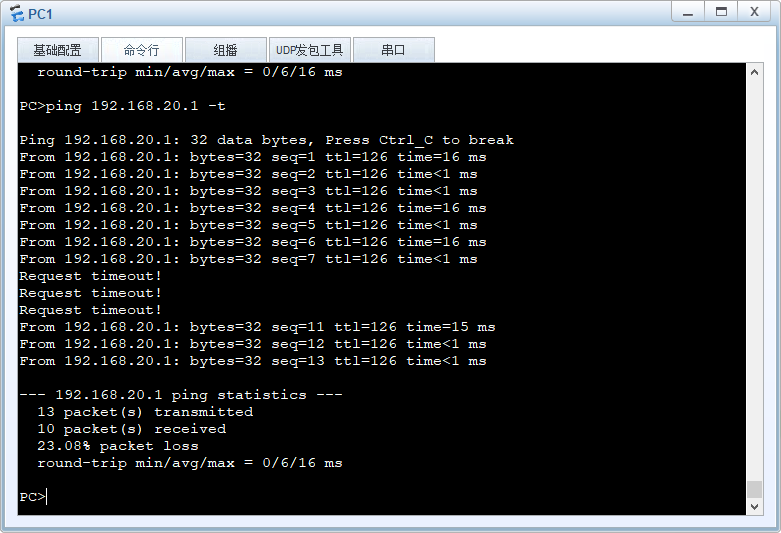
上图为中断链路后,流量会切到另外一条链路进行转发。
由于是负载分担的方式做的IPSEC VPN,但是在同一条会话中进行流量转发的时候默认是开启源进源出的。
注:本场景只适合单一CPU的防火墙,不适合多CPU的防火墙,多CPU防火墙会导致会话分离不通的CPU进行处理,华为建议采用主备双机负载分担的IPSEC VPN设计,该实验下回进行。