场景说明:PC3、PC2分别属于租户A、B,互相不能访问,整个网络为VXLAN网络,通过分布式网关部署,网关落于Leaf设备,Spine同时作为Border Leaf和Service Leaf三合一角色。防火墙主备部署,开启虚墙功能,不同租户使用不同虚墙,业务层面逻辑隔离,具体信息如上图所示。在防火墙上做SNAT使内部设备可以访问公网。
流量走向:PC3访问PE(模拟访问公网)路径为: PC3->Leaf->Spine(租户侧)->防火墙(Trust侧)->防火墙(Untrust侧)->Spine(Internet侧)-PE。
Leaf配置:
sysname Leaf # evpn-overlay enable # evpn # ip vpn-instance A //配置租户A的vrf ipv4-family route-distinguisher 1:10000 vpn-target 1:10000 export-extcommunity evpn vpn-target 1:10000 import-extcommunity evpn vxlan vni 10000 # ip vpn-instance B //配置租户B的vrf ipv4-family route-distinguisher 1:10001 vpn-target 1:10001 export-extcommunity evpn vpn-target 1:10001 import-extcommunity evpn vxlan vni 10001 # bridge-domain 10010 //建立vxlan 10010与vlan10关联的BD vxlan vni 10010 evpn route-distinguisher 1:10010 vpn-target 1:10010 export-extcommunity vpn-target 1:10000 export-extcommunity vpn-target 1:10010 import-extcommunity # bridge-domain 10020 //建立vxlan 10020与vlan20关联的BD vxlan vni 10020 evpn route-distinguisher 1:10020 vpn-target 1:10020 export-extcommunity vpn-target 1:10001 export-extcommunity vpn-target 1:10020 import-extcommunity # interface Vbdif10010 //配置分布式网关 ip binding vpn-instance A ip address 192.168.10.254 255.255.255.0 arp collect host enable //用于感知主机上线,收集主机信息 # interface Vbdif10020 //配置分布式网关 ip binding vpn-instance B ip address 192.168.20.254 255.255.255.0 arp collect host enable //用于感知主机上线,收集主机信息 # interface GE1/0/0 undo portswitch undo shutdown ip address 10.0.12.2 255.255.255.252 ospf network-type p2p # interface GE1/0/9.10 mode l2 encapsulation dot1q vid 10 bridge-domain 10010 # interface GE1/0/9.20 mode l2 encapsulation dot1q vid 20 bridge-domain 10020 # interface LoopBack0 ip address 1.1.1.2 255.255.255.255 # interface Nve1 source 1.1.1.2 vni 10010 head-end peer-list protocol bgp vni 10020 head-end peer-list protocol bgp # bgp 100 peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack0 # ipv4-family unicast undo peer 1.1.1.1 enable # l2vpn-family evpn policy vpn-target peer 1.1.1.1 enable peer 1.1.1.1 advertise irb # ospf 1 area 0.0.0.0 network 1.1.1.2 0.0.0.0 network 10.0.12.0 0.0.0.3 # return
Spine配置:
sysname Spine # vlan batch 11 21 100 to 101 # evpn-overlay enable # evpn # ip vpn-instance A //配置租户A的vrf ipv4-family route-distinguisher 1:10000 vpn-target 1:10000 export-extcommunity evpn vpn-target 1:10000 import-extcommunity evpn vxlan vni 10000 //租户A的L3 VNI # ip vpn-instance B //配置租户B的vrf ipv4-family route-distinguisher 1:10001 vpn-target 1:10001 export-extcommunity evpn vpn-target 1:10001 import-extcommunity evpn vxlan vni 10001 //租户B的L3 VNI # ip vpn-instance Internet ipv4-family route-distinguisher 100:100 vpn-target 100:100 export-extcommunity vpn-target 100:100 import-extcommunity # bfd # bridge-domain 10011 vxlan vni 10011 evpn route-distinguisher 1:10011 vpn-target 1:10011 export-extcommunity vpn-target 1:10000 export-extcommunity vpn-target 1:10011 import-extcommunity # bridge-domain 10021 vxlan vni 10021 evpn route-distinguisher 1:10021 vpn-target 1:10021 export-extcommunity vpn-target 1:10001 export-extcommunity vpn-target 1:10021 import-extcommunity # interface Vbdif10011 //与租户A虚墙互联接口 ip binding vpn-instance A ip address 10.0.11.4 255.255.255.248 # interface Vbdif10021 //与租户B虚墙互联接口 ip binding vpn-instance B ip address 10.0.21.4 255.255.255.248 # interface Vlanif100 //租户A虚墙与Internet侧互联接口 ip binding vpn-instance Internet ip address 10.0.100.4 255.255.255.248 # interface Vlanif101 //租户B虚墙与Internet侧互联接口 ip binding vpn-instance Internet ip address 10.0.101.4 255.255.255.248 # interface GE1/0/0 undo portswitch undo shutdown ip binding vpn-instance Internet ip address 100.0.0.2 255.255.255.252 # interface GE1/0/3 undo shutdown port link-type trunk port trunk allow-pass vlan 100 to 101 # interface GE1/0/3.11 mode l2 encapsulation dot1q vid 11 bridge-domain 10011 # interface GE1/0/3.21 mode l2 encapsulation dot1q vid 21 bridge-domain 10021 # interface GE1/0/4 undo shutdown port link-type trunk port trunk allow-pass vlan 100 to 101 # interface GE1/0/4.11 mode l2 encapsulation dot1q vid 11 bridge-domain 10011 # interface GE1/0/4.21 mode l2 encapsulation dot1q vid 21 bridge-domain 10021 # interface GE1/0/9 undo portswitch undo shutdown ip address 10.0.12.1 255.255.255.252 ospf network-type p2p # interface LoopBack0 ip address 1.1.1.1 255.255.255.255 # interface Nve1 source 1.1.1.1 vni 10011 head-end peer-list protocol bgp vni 10021 head-end peer-list protocol bgp # bgp 100 peer 1.1.1.2 as-number 100 peer 1.1.1.2 connect-interface LoopBack0 # ipv4-family unicast undo peer 1.1.1.2 enable # ipv4-family vpn-instance A //通过BGP EVPN 给租户A发布缺省路由 default-route imported import-route static advertise l2vpn evpn # ipv4-family vpn-instance B //通过BGP EVPN 给租户B发布缺省路由 default-route imported import-route static advertise l2vpn evpn # l2vpn-family evpn policy vpn-target peer 1.1.1.2 enable peer 1.1.1.2 advertise irb peer 1.1.1.2 reflect-client # ospf 1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 network 10.0.12.0 0.0.0.3 # ospf 100 vpn-instance Internet default-route-advertise bfd all-interfaces enable area 0.0.0.0 network 10.0.100.0 0.0.0.7 network 10.0.101.0 0.0.0.7 # ip route-static vpn-instance Internet 0.0.0.0 0.0.0.0 100.0.0.1 ip route-static vpn-instance A 0.0.0.0 0.0.0.0 10.0.11.1 ip route-static vpn-instance B 0.0.0.0 0.0.0.0 10.0.21.1 # return
防火墙(租户A虚墙相关配置)配置都差不多:
根墙下配置: # vsys name A 1 //给虚墙A分配资源 assign interface GigabitEthernet1/0/2.11 assign interface GigabitEthernet1/0/2.100 assign global-ip 100.0.1.0 100.0.1.255 exclusive # ospf 1 vpn-instance A //虚墙A与Internet侧建立OSPF bfd all-interfaces enable import-route static route-policy import_static_A //发布公网业务路由 area 0.0.0.0 network 10.0.100.0 0.0.0.7 # route-policy import_static_A permit node 10 if-match ip-prefix import_static_A # route-policy import_static_A deny node 20 # ip ip-prefix import_static_A index 10 permit 100.0.1.0 24 虚墙A配置: # switch vsys A # interface GigabitEthernet1/0/2.11 vlan-type dot1q 11 ip binding vpn-instance A ip address 10.0.11.2 255.255.255.248 vrrp vrid 1 virtual-ip 10.0.11.1 active service-manage ping permit # interface GigabitEthernet1/0/2.100 vlan-type dot1q 100 ip binding vpn-instance A ip address 10.0.100.2 255.255.255.248 vrrp vrid 2 virtual-ip 10.0.100.1 active service-manage ping permit # interface Virtual-if1 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/2.11 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/2.100 # firewall zone dmz set priority 50 # nat address-group SNAT_1 0 mode pat section 0 100.0.1.1 100.0.1.1 # security-policy rule name Trust_Untrust source-zone trust destination-zone untrust action permit # nat-policy rule name Trust_Untrust source-zone trust destination-zone untrust source-address 192.168.10.0 mask 255.255.255.0 action source-nat address-group SNAT_1 //主备墙不建议用easy_ip的方式做SNAT # ip route-static 100.0.1.0 255.255.255.0 NULL0 //为分配给虚墙A的公网业务路由做黑洞路由 ip route-static 192.168.10.0 255.255.255.0 10.0.11.4 # return
实验结果:
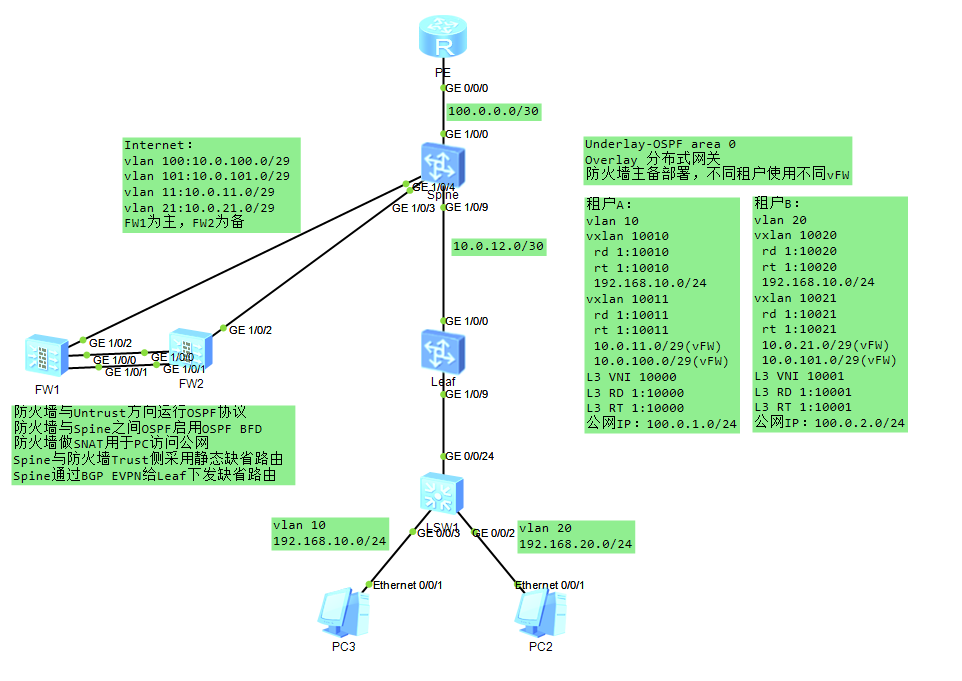
PC2可以正常访问公网,同理PC3也一样
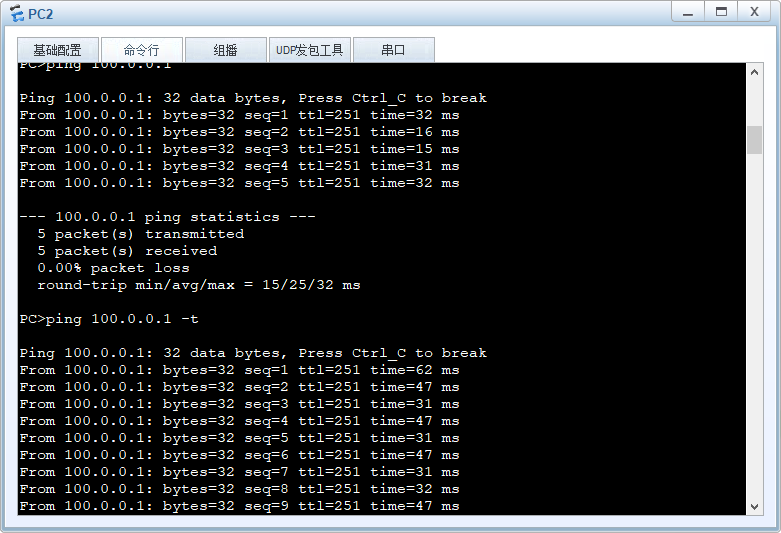
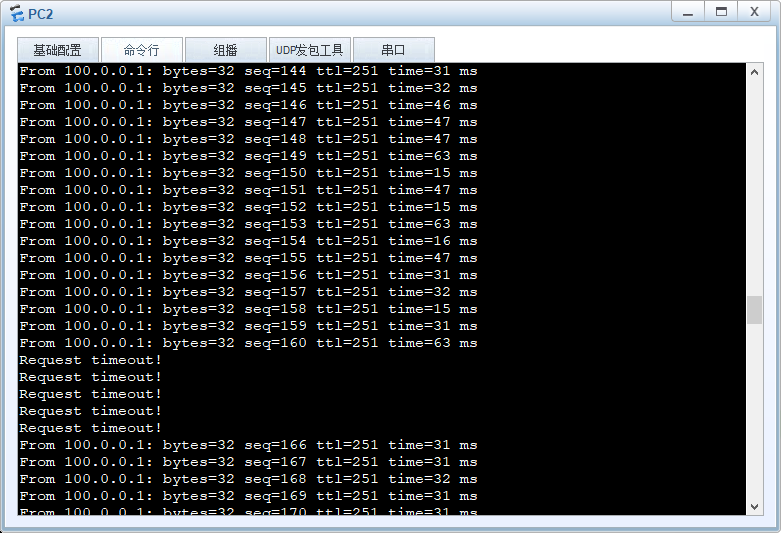
防火墙主备切换发生丢包,然后恢复通讯
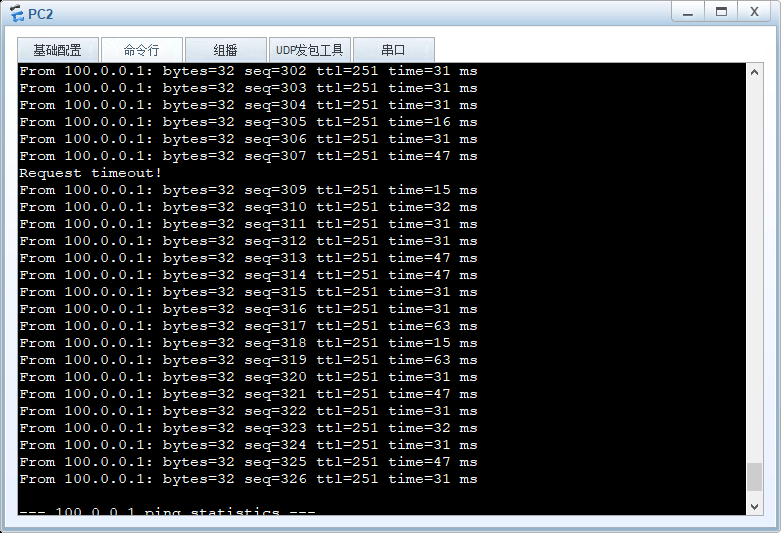
防火墙回切导致丢包
interface Vbdif10011 //与租户A虚墙互联接口
ip binding vpn-instance A
ip address 10.0.11.4 255.255.255.248
#
interface Vbdif10021 //与租户B虚墙互联接口
ip binding vpn-instance B
ip address 10.0.21.4 255.255.255.248
这个没弄明白?能解释一下吗?这是什么接口啊?不是用vlanif互联的吗?
这个是BD口的地址,在华为的VXLAN中是有一个BD的概念,用来桥接VXLAN和VLAN。因此整个接口的地址配置在Vbdif下, 类似H3C的地址配置在Vsi-interface接口下面,锐捷是配置在OverlayRouter接口下
你好:拜读了。有个问题:
1、spine与FW互联,为什么与虚墙untrust互联用vlanif,与虚墙Trust互联用vbdif呢?
2、如果租户A与租户B有互访需求,是在两个虚墙内直接相互指路由,还是流量通过根墙打通路由进行互访。
我也经常做数据中心的项目,有兴趣加个微信seven_sususu一起研究下技术。
你好:拜读了。有个问题: 1、spine与FW互联,为什么与虚墙untrust互联用vlanif,与虚墙Trust互联用vbdif呢? 2、如果租户A与租户B有互访需求,是在两个虚墙内直接相互指路由,还是流量通过根墙打通路由进行互访。
我也经常做数据中心的项目,有兴趣加个微信seven_sususu一起研究下技术。
你好:拜读了。有个问题:
1、spine与FW互联,为什么与虚墙untrust互联用vlanif,与虚墙Trust互联用vbdif呢?
2、如果租户A与租户B有互访需求,是在两个虚墙内直接相互指路由,还是流量通过根墙打通路由进行互访。?
3、在虚墙A内配置trust方向的明细路由,是全局IPv4路由,但互联接口在VPN-instance下,这样可以通吗?
我也经常做数据中心的项目,有兴趣加个微信seven_sususu一起研究下技术。
你好:拜读了。有个问题:
1、spine与FW互联,为什么与虚墙untrust互联用vlanif,与虚墙Trust互联用vbdif呢?
2、如果租户A与租户B有互访需求,是在两个虚墙内直接相互指路由,还是流量通过根墙打通路由进行互访。?
3、在虚墙A内配置trust方向的明细路由,是全局IPv4路由,但互联接口在instance下,这样可以通吗?
我也经常做数据中心的项目,有兴趣加个微信seven_sususu一起研究下技术。