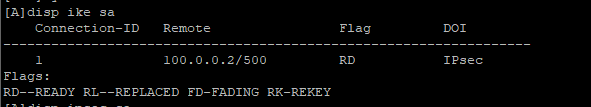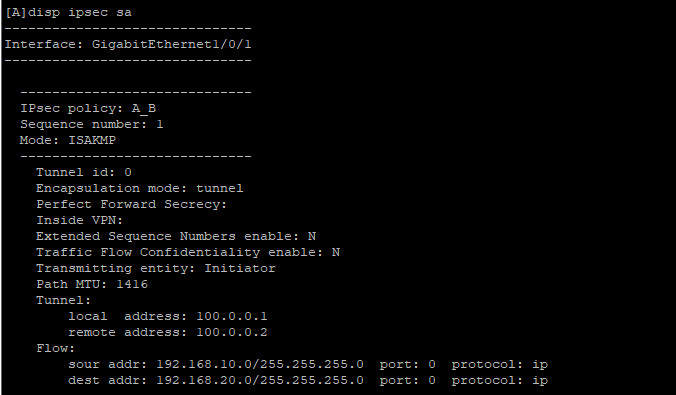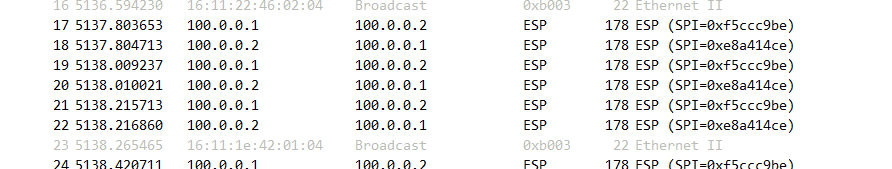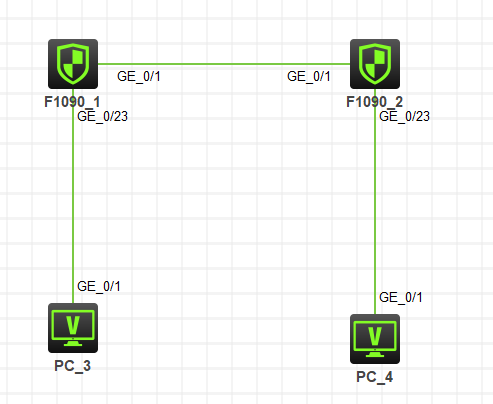
场景说明:PC3访问PC4,通过在防火墙建立IPSEC VPN加密通讯流量提升安全性。
防火墙配置:
#
sysname A
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 100.0.0.1 255.255.255.252
ipsec apply policy A_B //应用IPSEC策略到接口
#
interface GigabitEthernet1/0/23
port link-mode route
combo enable copper
ip address 192.168.10.254 255.255.255.0
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/23
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
ip route-static 192.168.20.0 24 100.0.0.2
#
acl advanced 3000 //配置IPSEC感兴趣流量,保护192.168.10.0访问192.168.20.0的流量
rule 0 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec transform-set A_B //配置IPSEC 安全提议,这里有默认配置,传输模式是隧道模式,安全协议使用的esp,因此没有显示
esp encryption-algorithm aes-cbc-256 //配置加密算法
esp authentication-algorithm sha384 //配置认证算法
#
ipsec policy A_B 1 isakmp //配置IPSEC 策略
transform-set A_B //设置IPSEC安全提议
security acl 3000 //设备被保护流量
local-address 100.0.0.1
remote-address 100.0.0.2
ike-profile A //设置IKE配置文件
#
ike profile A //配置IKE 配置
keychain A //指定IKE钥匙链(预共享密钥)
match remote identity address 100.0.0.2 0.0.0.0
#
ike keychain A //配置IKE钥匙链(预共享密钥)
pre-shared-key address 100.0.0.2 0.0.0.0 key cipher $c$3$wsGYu2O9mPloXgeCBhCyOaN/Bb4pyVybmA==
#
security-policy ip
rule 0 name Untrust_Local_Permit
action pass
source-zone Untrust
destination-zone Local
source-ip-host 100.0.0.2
destination-ip-host 100.0.0.1
rule 1 name Local_Untrust_Permit
action pass
source-zone Local
destination-zone Untrust
rule 2 name Trust_Untrust_Permit
action pass
source-zone Trust
destination-zone Untrust
rule 3 name Untrust_Trust_Permit
action pass
source-zone Untrust
destination-zone Trust
source-ip-subnet 192.168.20.0 255.255.255.0
destination-ip-subnet 192.168.10.0 255.255.255.0
#
sysname A
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 100.0.0.1 255.255.255.252
ipsec apply policy A_B //应用IPSEC策略到接口
#
interface GigabitEthernet1/0/23
port link-mode route
combo enable copper
ip address 192.168.10.254 255.255.255.0
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/23
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
ip route-static 192.168.20.0 24 100.0.0.2
#
acl advanced 3000 //配置IPSEC感兴趣流量,保护192.168.10.0访问192.168.20.0的流量
rule 0 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
ipsec transform-set A_B //配置IPSEC 安全提议,这里有默认配置,传输模式是隧道模式,安全协议使用的esp,因此没有显示
esp encryption-algorithm aes-cbc-256 //配置加密算法
esp authentication-algorithm sha384 //配置认证算法
#
ipsec policy A_B 1 isakmp //配置IPSEC 策略
transform-set A_B //设置IPSEC安全提议
security acl 3000 //设备被保护流量
local-address 100.0.0.1
remote-address 100.0.0.2
ike-profile A //设置IKE配置文件
#
ike profile A //配置IKE 配置
keychain A //指定IKE钥匙链(预共享密钥)
match remote identity address 100.0.0.2 0.0.0.0
#
ike keychain A //配置IKE钥匙链(预共享密钥)
pre-shared-key address 100.0.0.2 0.0.0.0 key cipher $c$3$wsGYu2O9mPloXgeCBhCyOaN/Bb4pyVybmA==
#
security-policy ip
rule 0 name Untrust_Local_Permit
action pass
source-zone Untrust
destination-zone Local
source-ip-host 100.0.0.2
destination-ip-host 100.0.0.1
rule 1 name Local_Untrust_Permit
action pass
source-zone Local
destination-zone Untrust
rule 2 name Trust_Untrust_Permit
action pass
source-zone Trust
destination-zone Untrust
rule 3 name Untrust_Trust_Permit
action pass
source-zone Untrust
destination-zone Trust
source-ip-subnet 192.168.20.0 255.255.255.0
destination-ip-subnet 192.168.10.0 255.255.255.0
# sysname A # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 100.0.0.1 255.255.255.252 ipsec apply policy A_B //应用IPSEC策略到接口 # interface GigabitEthernet1/0/23 port link-mode route combo enable copper ip address 192.168.10.254 255.255.255.0 # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/23 # security-zone name Untrust import interface GigabitEthernet1/0/1 # ip route-static 192.168.20.0 24 100.0.0.2 # acl advanced 3000 //配置IPSEC感兴趣流量,保护192.168.10.0访问192.168.20.0的流量 rule 0 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255 # ipsec transform-set A_B //配置IPSEC 安全提议,这里有默认配置,传输模式是隧道模式,安全协议使用的esp,因此没有显示 esp encryption-algorithm aes-cbc-256 //配置加密算法 esp authentication-algorithm sha384 //配置认证算法 # ipsec policy A_B 1 isakmp //配置IPSEC 策略 transform-set A_B //设置IPSEC安全提议 security acl 3000 //设备被保护流量 local-address 100.0.0.1 remote-address 100.0.0.2 ike-profile A //设置IKE配置文件 # ike profile A //配置IKE 配置 keychain A //指定IKE钥匙链(预共享密钥) match remote identity address 100.0.0.2 0.0.0.0 # ike keychain A //配置IKE钥匙链(预共享密钥) pre-shared-key address 100.0.0.2 0.0.0.0 key cipher $c$3$wsGYu2O9mPloXgeCBhCyOaN/Bb4pyVybmA== # security-policy ip rule 0 name Untrust_Local_Permit action pass source-zone Untrust destination-zone Local source-ip-host 100.0.0.2 destination-ip-host 100.0.0.1 rule 1 name Local_Untrust_Permit action pass source-zone Local destination-zone Untrust rule 2 name Trust_Untrust_Permit action pass source-zone Trust destination-zone Untrust rule 3 name Untrust_Trust_Permit action pass source-zone Untrust destination-zone Trust source-ip-subnet 192.168.20.0 255.255.255.0 destination-ip-subnet 192.168.10.0 255.255.255.0
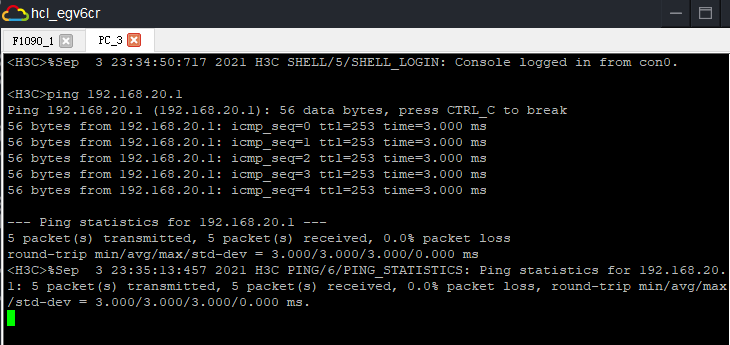
实验结果: