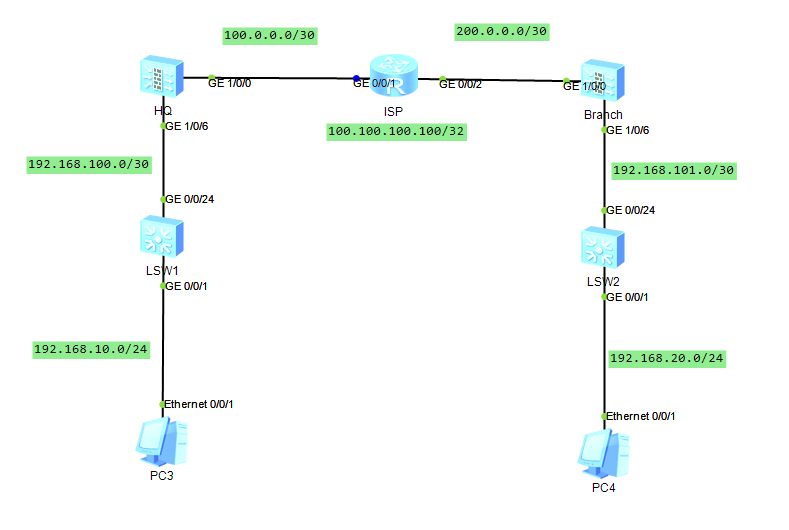
场景说明:HQ与Branch之间客户端互访,HQ、Branch分别与本部核心交换机运行OSPF协议,HQ、Branch之间通过GREP隧道运行OSPF协议通告两端的客户端路由,使得客户端可以互访。同时HQ的客户端PC3可以访问公网100.100.100.100。
防火墙配置:
#
sysname A
#
acl number 3000 //配置IPSec感兴趣流,这里地址填写建立GRE隧道的地址,用于保护GRE隧道通讯的流量
rule 5 permit ip source 100.0.0.2 0 destination 200.0.0.2 0
#
ipsec proposal A_B //配置IPSec安全提议,这里封装模式使用的隧道模式,安全协议为esp,由于是默认配置因此不显示
esp authentication-algorithm sha2-512
esp encryption-algorithm aes-256
#
ike proposal 1 //配置IKE安全提议
encryption-algorithm aes-256
dh group16
authentication-algorithm sha2-512
authentication-method pre-share
integrity-algorithm hmac-sha2-512
prf hmac-sha2-512
#
ike peer A //配置IKE PEER
pre-shared-key %^%#glANCEF9v&t}}(;!Esd(B}"V<;WDT@pxei&zBy;<%^%#
ike-proposal 1
remote-address 200.0.0.2
#
ipsec policy A_B 1 isakmp //配置IPSEC策略
security acl 3000
ike-peer A
proposal A_B
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
ipsec policy A_B //将IPSec策略应用在出接口上,在此场景不能运行在Tunnel口上
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.100.1 255.255.255.252
service-manage ping permit
#
interface Tunnel0 //配置GRE隧道的逻辑接口
ip address 10.0.12.1 255.255.255.252
tunnel-protocol gre
source 100.0.0.2
destination 200.0.0.2
gre key cipher %^%#v(`f',AH-Uy/SAL\~"C0|UOFK]:KoYQF4-#*R&gG%^%#
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Tunnel0
#
ospf 1
area 0.0.0.0
network 10.0.12.0 0.0.0.3
network 192.168.100.0 0.0.0.3
#
ip route-static 0.0.0.0 0.0.0.0 100.0.0.1
ip route-static 200.0.0.2 255.255.255.255 100.0.0.1
#
security-policy
rule name Local_Untrust //配置策略允许FW访问Untrust
source-zone local
destination-zone untrust
action permit
rule name Untrust_Local //允许Branch-FW访问HQ-FW
source-zone untrust
destination-zone local
source-address 200.0.0.2 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
action permit
rule name Trust_Untrust //配置策略允许HQ终端访问公网
source-zone trust
destination-zone untrust
action permit
rule name Untrust_Trust_Permit //允许Branch终端访问HQ终端
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_IPsec //允许HQ与Branch之间GREP隧道建立
source-zone untrust
destination-zone local
source-address 10.0.12.2 mask 255.255.255.255
destination-address 10.0.12.1 mask 255.255.255.255
action permit
#
nat-policy
rule name Trust_Untrust_NO-NAT //配置NO-NAT策略,让HQ与Branch之间互访不走NAT
source-zone trust
destination-zone untrust
destination-address 192.168.20.0 mask 255.255.255.0
action no-nat
rule name Trust_Untrust_SNAT //配置HQ侧终端访问公网时进行SNAT
source-zone trust
destination-zone untrust
action source-nat easy-ip
#
return
#
sysname A
#
acl number 3000 //配置IPSec感兴趣流,这里地址填写建立GRE隧道的地址,用于保护GRE隧道通讯的流量
rule 5 permit ip source 100.0.0.2 0 destination 200.0.0.2 0
#
ipsec proposal A_B //配置IPSec安全提议,这里封装模式使用的隧道模式,安全协议为esp,由于是默认配置因此不显示
esp authentication-algorithm sha2-512
esp encryption-algorithm aes-256
#
ike proposal 1 //配置IKE安全提议
encryption-algorithm aes-256
dh group16
authentication-algorithm sha2-512
authentication-method pre-share
integrity-algorithm hmac-sha2-512
prf hmac-sha2-512
#
ike peer A //配置IKE PEER
pre-shared-key %^%#glANCEF9v&t}}(;!Esd(B}"V<;WDT@pxei&zBy;<%^%#
ike-proposal 1
remote-address 200.0.0.2
#
ipsec policy A_B 1 isakmp //配置IPSEC策略
security acl 3000
ike-peer A
proposal A_B
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.2 255.255.255.252
service-manage ping permit
ipsec policy A_B //将IPSec策略应用在出接口上,在此场景不能运行在Tunnel口上
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 192.168.100.1 255.255.255.252
service-manage ping permit
#
interface Tunnel0 //配置GRE隧道的逻辑接口
ip address 10.0.12.1 255.255.255.252
tunnel-protocol gre
source 100.0.0.2
destination 200.0.0.2
gre key cipher %^%#v(`f',AH-Uy/SAL\~"C0|UOFK]:KoYQF4-#*R&gG%^%#
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/6
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Tunnel0
#
ospf 1
area 0.0.0.0
network 10.0.12.0 0.0.0.3
network 192.168.100.0 0.0.0.3
#
ip route-static 0.0.0.0 0.0.0.0 100.0.0.1
ip route-static 200.0.0.2 255.255.255.255 100.0.0.1
#
security-policy
rule name Local_Untrust //配置策略允许FW访问Untrust
source-zone local
destination-zone untrust
action permit
rule name Untrust_Local //允许Branch-FW访问HQ-FW
source-zone untrust
destination-zone local
source-address 200.0.0.2 mask 255.255.255.255
destination-address 100.0.0.2 mask 255.255.255.255
action permit
rule name Trust_Untrust //配置策略允许HQ终端访问公网
source-zone trust
destination-zone untrust
action permit
rule name Untrust_Trust_Permit //允许Branch终端访问HQ终端
source-zone untrust
destination-zone trust
source-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name Untrust_Local_IPsec //允许HQ与Branch之间GREP隧道建立
source-zone untrust
destination-zone local
source-address 10.0.12.2 mask 255.255.255.255
destination-address 10.0.12.1 mask 255.255.255.255
action permit
#
nat-policy
rule name Trust_Untrust_NO-NAT //配置NO-NAT策略,让HQ与Branch之间互访不走NAT
source-zone trust
destination-zone untrust
destination-address 192.168.20.0 mask 255.255.255.0
action no-nat
rule name Trust_Untrust_SNAT //配置HQ侧终端访问公网时进行SNAT
source-zone trust
destination-zone untrust
action source-nat easy-ip
#
return
# sysname A # acl number 3000 //配置IPSec感兴趣流,这里地址填写建立GRE隧道的地址,用于保护GRE隧道通讯的流量 rule 5 permit ip source 100.0.0.2 0 destination 200.0.0.2 0 # ipsec proposal A_B //配置IPSec安全提议,这里封装模式使用的隧道模式,安全协议为esp,由于是默认配置因此不显示 esp authentication-algorithm sha2-512 esp encryption-algorithm aes-256 # ike proposal 1 //配置IKE安全提议 encryption-algorithm aes-256 dh group16 authentication-algorithm sha2-512 authentication-method pre-share integrity-algorithm hmac-sha2-512 prf hmac-sha2-512 # ike peer A //配置IKE PEER pre-shared-key %^%#glANCEF9v&t}}(;!Esd(B}"V<;WDT@pxei&zBy;<%^%# ike-proposal 1 remote-address 200.0.0.2 # ipsec policy A_B 1 isakmp //配置IPSEC策略 security acl 3000 ike-peer A proposal A_B # interface GigabitEthernet1/0/0 undo shutdown ip address 100.0.0.2 255.255.255.252 service-manage ping permit ipsec policy A_B //将IPSec策略应用在出接口上,在此场景不能运行在Tunnel口上 # interface GigabitEthernet1/0/6 undo shutdown ip address 192.168.100.1 255.255.255.252 service-manage ping permit # interface Tunnel0 //配置GRE隧道的逻辑接口 ip address 10.0.12.1 255.255.255.252 tunnel-protocol gre source 100.0.0.2 destination 200.0.0.2 gre key cipher %^%#v(`f',AH-Uy/SAL\~"C0|UOFK]:KoYQF4-#*R&gG%^%# service-manage ping permit # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/6 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0 add interface Tunnel0 # ospf 1 area 0.0.0.0 network 10.0.12.0 0.0.0.3 network 192.168.100.0 0.0.0.3 # ip route-static 0.0.0.0 0.0.0.0 100.0.0.1 ip route-static 200.0.0.2 255.255.255.255 100.0.0.1 # security-policy rule name Local_Untrust //配置策略允许FW访问Untrust source-zone local destination-zone untrust action permit rule name Untrust_Local //允许Branch-FW访问HQ-FW source-zone untrust destination-zone local source-address 200.0.0.2 mask 255.255.255.255 destination-address 100.0.0.2 mask 255.255.255.255 action permit rule name Trust_Untrust //配置策略允许HQ终端访问公网 source-zone trust destination-zone untrust action permit rule name Untrust_Trust_Permit //允许Branch终端访问HQ终端 source-zone untrust destination-zone trust source-address 192.168.20.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 action permit rule name Untrust_Local_IPsec //允许HQ与Branch之间GREP隧道建立 source-zone untrust destination-zone local source-address 10.0.12.2 mask 255.255.255.255 destination-address 10.0.12.1 mask 255.255.255.255 action permit # nat-policy rule name Trust_Untrust_NO-NAT //配置NO-NAT策略,让HQ与Branch之间互访不走NAT source-zone trust destination-zone untrust destination-address 192.168.20.0 mask 255.255.255.0 action no-nat rule name Trust_Untrust_SNAT //配置HQ侧终端访问公网时进行SNAT source-zone trust destination-zone untrust action source-nat easy-ip # return
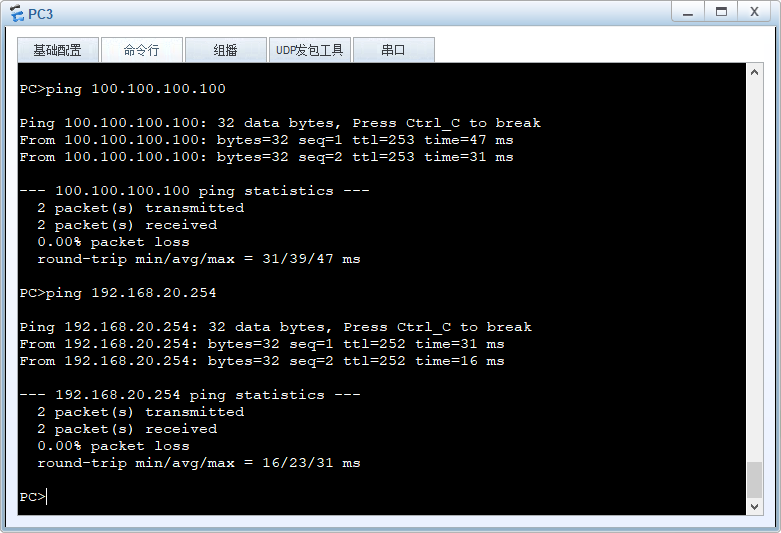
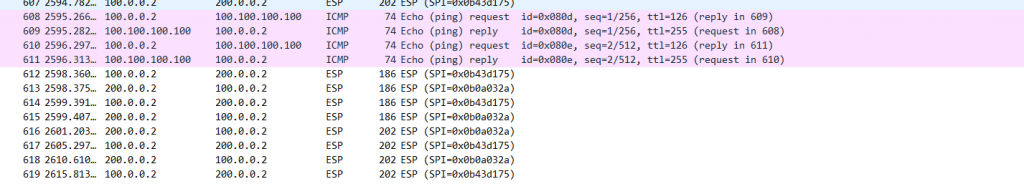
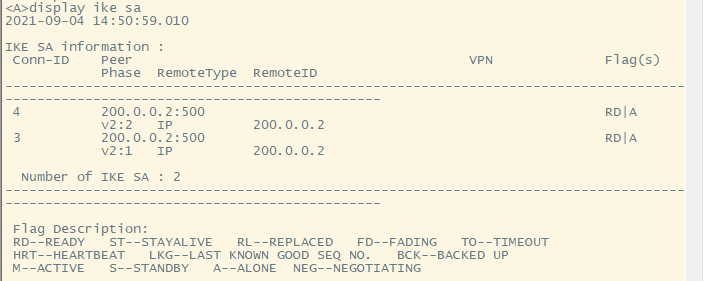
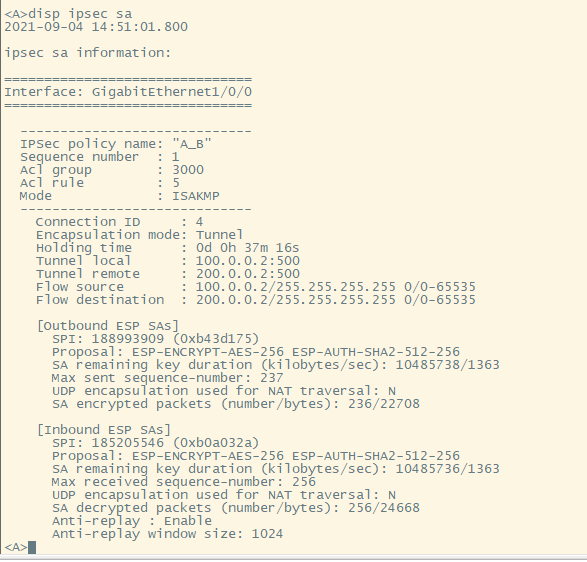
实验结果: