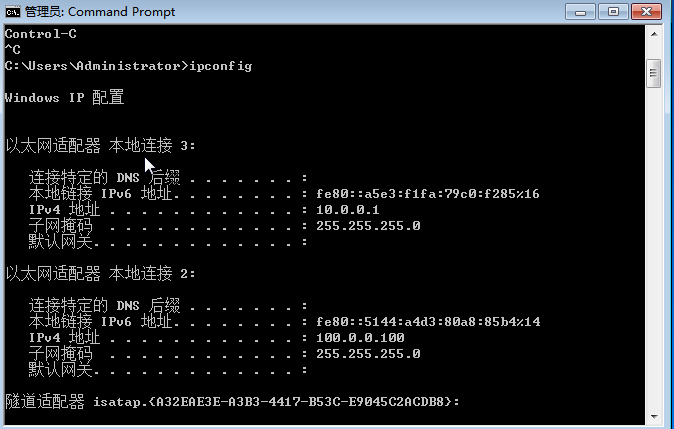
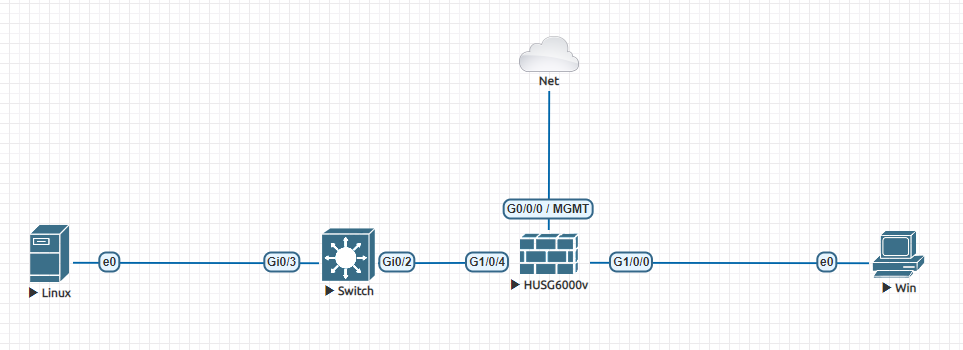
场景说明:防火墙作为企业网关,外网PC通过SSL VPN访问公司内部资源
防火墙配置:
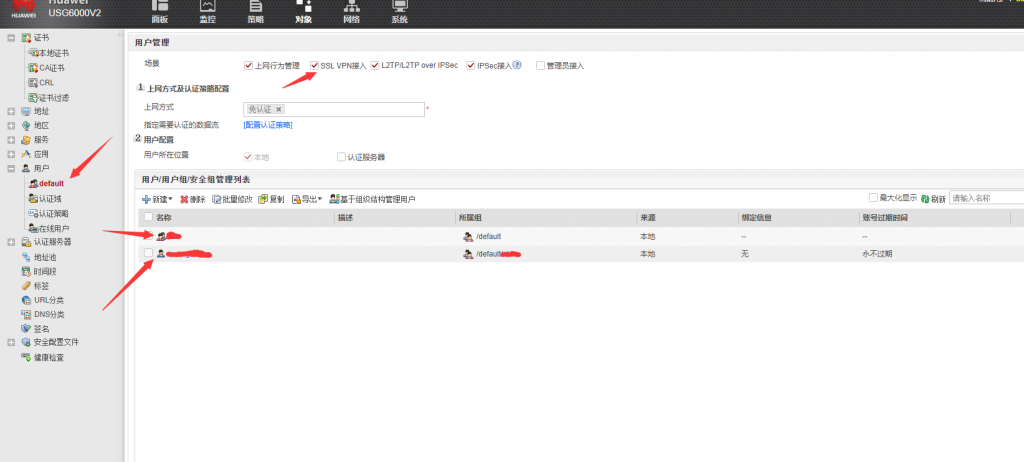
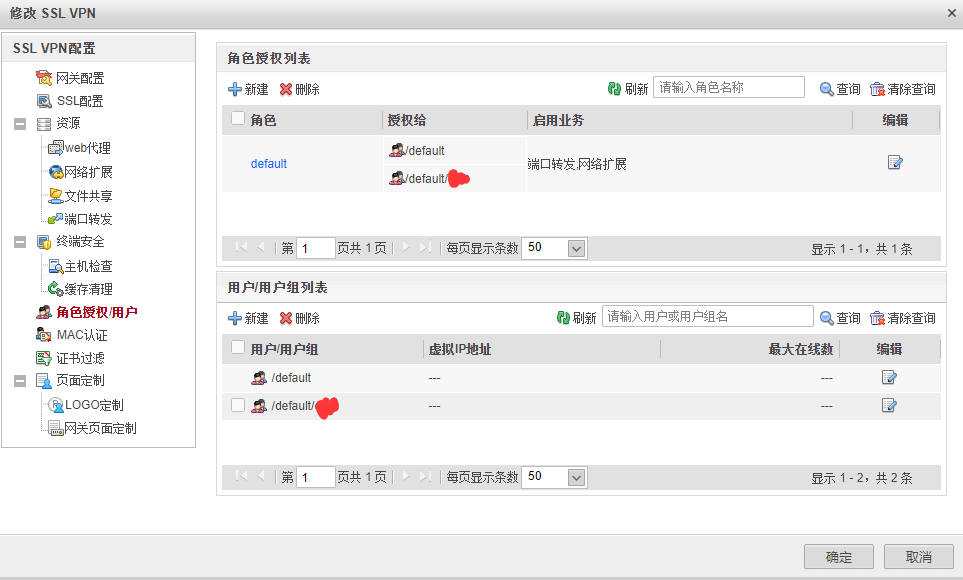
建议创建组来区分具体权限,这样管理方便。
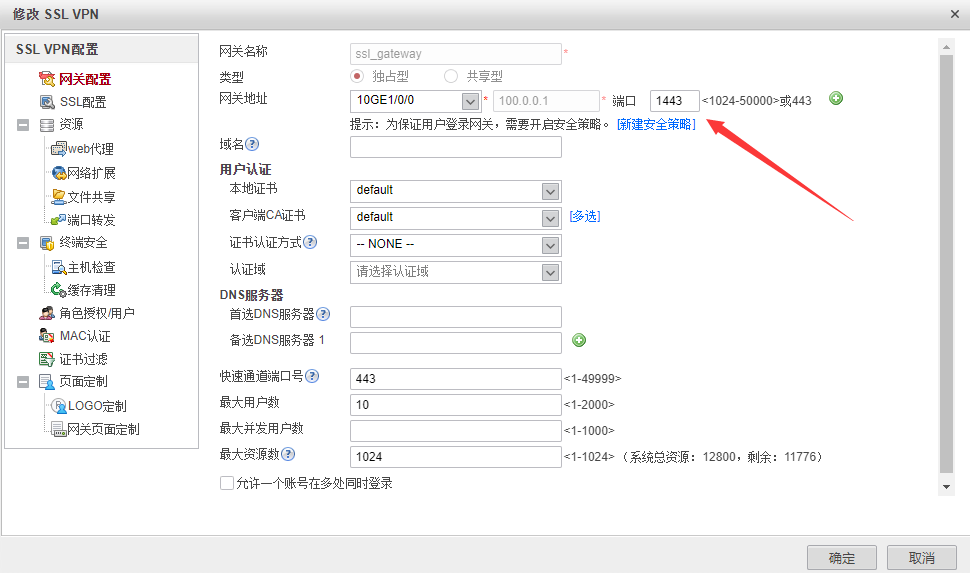
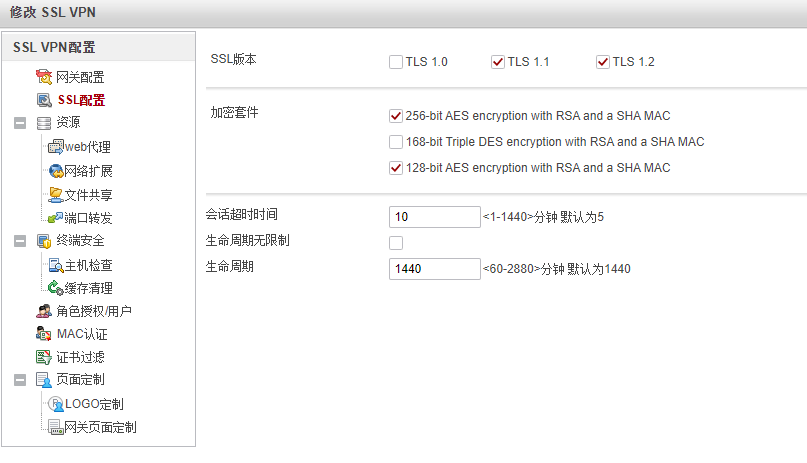
这里我修改了虚拟网关的端口为1443,客户端通过地址:1443的方式访问SSL网关。关于证书认证方式:华为叫做证书米明和证书挑战。
证书匿名:只认证证书的正确性即可访问VPN
证书挑战:认证证书的正确性的时候又需要进行用户名和口令的认证
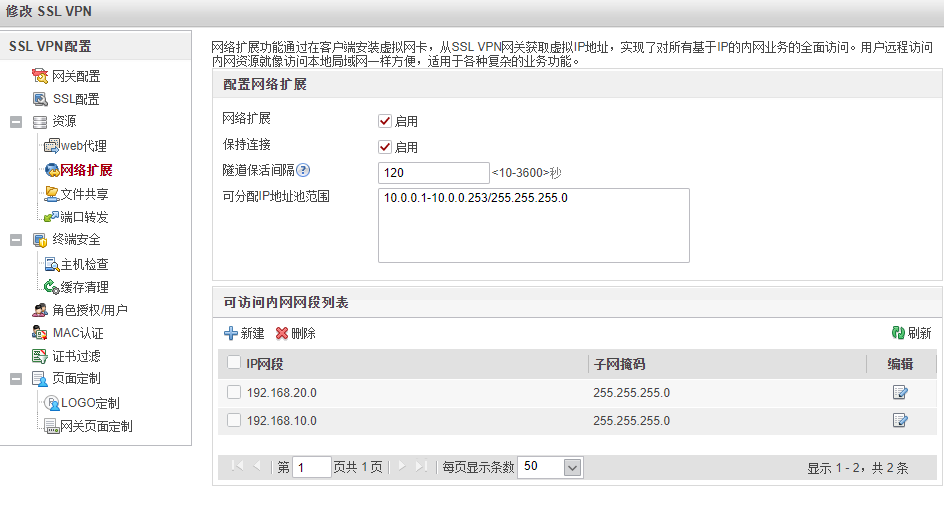
设置资源管理方式,这里设置的是访问某个子网的全量资源,也就是网络扩展方式,对应其他VPN的NC方式。
这里授权给用户组即可,组内用户自动会被赋予该组的权限
防火墙配置CLI:
#
sysname FW
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.110.50 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.100.1 255.255.255.252
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
#
api
#
ip route-static 192.168.10.0 255.255.255.0 192.168.100.2
ip route-static 192.168.20.0 255.255.255.0 192.168.100.2
#
v-gateway public ssl version tlsv11 tlsv12
v-gateway public ssl ciphersuit custom aes256-sha non-des-cbc3-sha aes128-sha
v-gateway ssl_gateway interface GigabitEthernet1/0/0 port 1443 private
v-gateway ssl_gateway alias SSL_Gateway
#
#
user-interface con 0
authentication-mode password
set authentication password cipher $1c$uMM_BG!%M:$Q+N<0jBRb0!o)C)'@Hj6ASlG%9-a7&9Q"cK!~ig&$
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
#****BEGIN***ssl_gateway**1****#
v-gateway ssl_gateway //创建虚拟网关
basic
ssl version tlsv11 tlsv12
ssl timeout 10
ssl lifecycle 1440
ssl ciphersuit custom aes256-sha non-des-cbc3-sha aes128-sha
service
port-forwarding enable
port-forwarding auto-start enable
port-forwarding resource VC host-ip 192.168.10.1 443
port-forwarding resource VC-5480 host-ip 192.168.10.1 5480
network-extension enable
network-extension keep-alive enable
network-extension keep-alive interval 120
network-extension netpool 10.0.0.1 10.0.0.253 255.255.255.0
netpool 10.0.0.1 default
network-extension mode manual
network-extension manual-route 192.168.20.0 255.255.255.0
network-extension manual-route 192.168.10.0 255.255.255.0
security
policy-default-action permit vt-src-ip
certification cert-anonymous cert-field user-filter subject cn group-filter subject cn
certification cert-anonymous filter-policy permit-all
certification cert-challenge cert-field user-filter subject cn
certification user-cert-filter key-usage any
undo public-user enable
hostchecker
cachecleaner
role
role default
role default condition all
role default network-extension enable
role default port-forwarding enable
#****END****#
#
right-manager server-group
#
security-policy
rule name Untrust_Local_SSL-VPN //设置SSL-VPN访问虚拟网关的策略
source-zone untrust
destination-zone local
destination-address 100.0.0.1 mask 255.255.255.255
service TCP_1443
action permit
rule name Untrust_Trust_SSL-VPN //设置SSL-VPN客户端访问内网资源的策略,源地址为虚拟地址
source-zone untrust
destination-zone trust
source-address 10.0.0.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
#
return
#
sysname FW
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.110.50 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.0.0.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.100.1 255.255.255.252
service-manage ping permit
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/4
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
#
api
#
ip route-static 192.168.10.0 255.255.255.0 192.168.100.2
ip route-static 192.168.20.0 255.255.255.0 192.168.100.2
#
v-gateway public ssl version tlsv11 tlsv12
v-gateway public ssl ciphersuit custom aes256-sha non-des-cbc3-sha aes128-sha
v-gateway ssl_gateway interface GigabitEthernet1/0/0 port 1443 private
v-gateway ssl_gateway alias SSL_Gateway
#
#
user-interface con 0
authentication-mode password
set authentication password cipher $1c$uMM_BG!%M:$Q+N<0jBRb0!o)C)'@Hj6ASlG%9-a7&9Q"cK!~ig&$
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
#****BEGIN***ssl_gateway**1****#
v-gateway ssl_gateway //创建虚拟网关
basic
ssl version tlsv11 tlsv12
ssl timeout 10
ssl lifecycle 1440
ssl ciphersuit custom aes256-sha non-des-cbc3-sha aes128-sha
service
port-forwarding enable
port-forwarding auto-start enable
port-forwarding resource VC host-ip 192.168.10.1 443
port-forwarding resource VC-5480 host-ip 192.168.10.1 5480
network-extension enable
network-extension keep-alive enable
network-extension keep-alive interval 120
network-extension netpool 10.0.0.1 10.0.0.253 255.255.255.0
netpool 10.0.0.1 default
network-extension mode manual
network-extension manual-route 192.168.20.0 255.255.255.0
network-extension manual-route 192.168.10.0 255.255.255.0
security
policy-default-action permit vt-src-ip
certification cert-anonymous cert-field user-filter subject cn group-filter subject cn
certification cert-anonymous filter-policy permit-all
certification cert-challenge cert-field user-filter subject cn
certification user-cert-filter key-usage any
undo public-user enable
hostchecker
cachecleaner
role
role default
role default condition all
role default network-extension enable
role default port-forwarding enable
#****END****#
#
right-manager server-group
#
security-policy
rule name Untrust_Local_SSL-VPN //设置SSL-VPN访问虚拟网关的策略
source-zone untrust
destination-zone local
destination-address 100.0.0.1 mask 255.255.255.255
service TCP_1443
action permit
rule name Untrust_Trust_SSL-VPN //设置SSL-VPN客户端访问内网资源的策略,源地址为虚拟地址
source-zone untrust
destination-zone trust
source-address 10.0.0.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
action permit
#
return
# sysname FW # interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.110.50 255.255.255.0 service-manage http permit service-manage https permit service-manage ping permit # interface GigabitEthernet1/0/0 undo shutdown ip address 100.0.0.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/4 undo shutdown ip address 192.168.100.1 255.255.255.252 service-manage ping permit # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/4 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0 # firewall zone dmz set priority 50 # api # ip route-static 192.168.10.0 255.255.255.0 192.168.100.2 ip route-static 192.168.20.0 255.255.255.0 192.168.100.2 # v-gateway public ssl version tlsv11 tlsv12 v-gateway public ssl ciphersuit custom aes256-sha non-des-cbc3-sha aes128-sha v-gateway ssl_gateway interface GigabitEthernet1/0/0 port 1443 private v-gateway ssl_gateway alias SSL_Gateway # # user-interface con 0 authentication-mode password set authentication password cipher $1c$uMM_BG!%M:$Q+N<0jBRb0!o)C)'@Hj6ASlG%9-a7&9Q"cK!~ig&$ user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user-interface vty 16 20 # pki realm default # sa # location # multi-linkif mode proportion-of-weight # #****BEGIN***ssl_gateway**1****# v-gateway ssl_gateway //创建虚拟网关 basic ssl version tlsv11 tlsv12 ssl timeout 10 ssl lifecycle 1440 ssl ciphersuit custom aes256-sha non-des-cbc3-sha aes128-sha service port-forwarding enable port-forwarding auto-start enable port-forwarding resource VC host-ip 192.168.10.1 443 port-forwarding resource VC-5480 host-ip 192.168.10.1 5480 network-extension enable network-extension keep-alive enable network-extension keep-alive interval 120 network-extension netpool 10.0.0.1 10.0.0.253 255.255.255.0 netpool 10.0.0.1 default network-extension mode manual network-extension manual-route 192.168.20.0 255.255.255.0 network-extension manual-route 192.168.10.0 255.255.255.0 security policy-default-action permit vt-src-ip certification cert-anonymous cert-field user-filter subject cn group-filter subject cn certification cert-anonymous filter-policy permit-all certification cert-challenge cert-field user-filter subject cn certification user-cert-filter key-usage any undo public-user enable hostchecker cachecleaner role role default role default condition all role default network-extension enable role default port-forwarding enable #****END****# # right-manager server-group # security-policy rule name Untrust_Local_SSL-VPN //设置SSL-VPN访问虚拟网关的策略 source-zone untrust destination-zone local destination-address 100.0.0.1 mask 255.255.255.255 service TCP_1443 action permit rule name Untrust_Trust_SSL-VPN //设置SSL-VPN客户端访问内网资源的策略,源地址为虚拟地址 source-zone untrust destination-zone trust source-address 10.0.0.0 mask 255.255.255.0 destination-address 192.168.10.0 mask 255.255.255.0 destination-address 192.168.20.0 mask 255.255.255.0 action permit # return
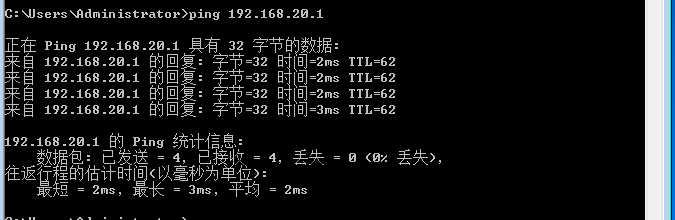
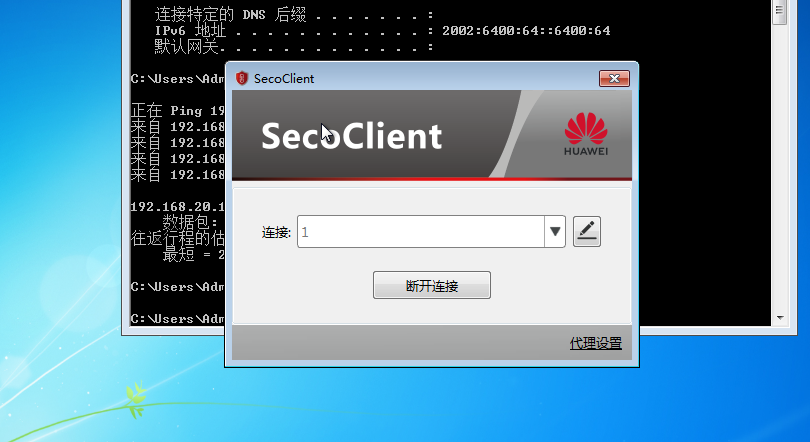
实验结果: